A high-stakes scam is spreading quickly across social media, promoting what appears to be an exclusive token presale for a cryptocurrency called $X Token. With a sleek pitch, fake celebrity endorsements, and promises of massive rewards, it’s gaining traction. The campaign even features a fabricated tweet from Elon Musk, claiming the $X presale is “Live Now” for only 24 hours. The scam, hosted at token-x.live, has already tricked thousands of users into connecting wallets, submitting private keys, and ultimately losing their cryptocurrency.
Let’s be absolutely clear: the $X Token presale is a scam. It is not affiliated with Elon Musk, X (formerly Twitter), OpenAI, Binance, or any other legitimate entity falsely listed on its website. This article will uncover exactly how the scam works, break down the deception, show what victims can do, and provide guidance on how to stay safe from similar traps in the future.
How the Fake $X Token Presale Is Built to Deceive
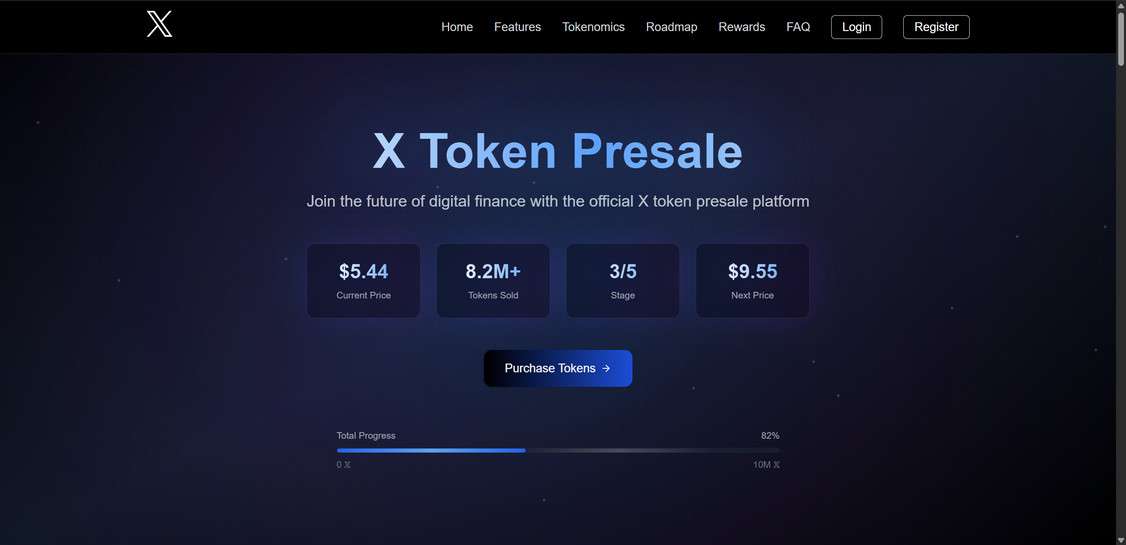
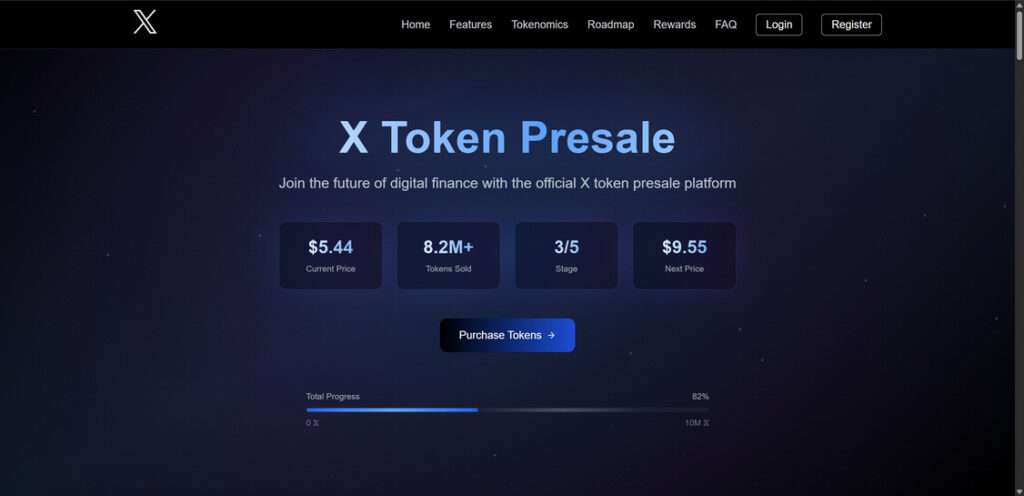
The fraudulent $X Token presale, presented through websites like token-x.live, is designed to look like a high-profile crypto launch. It claims to be backed by top-tier companies including OpenAI, SpaceX, Tesla, Binance, and JPMorgan, and promotes a futuristic roadmap with AI trading tools, Metaverse integration, and VIP benefits. These names and features are completely fabricated.
The scam’s core strategy is to:
- Leverage brand trust by falsely associating with major tech companies
- Use deepfake imagery and fake tweets from Elon Musk to boost legitimacy
- Create fake urgency, such as “only 24 hours left”
- Entice users with unrealistic rewards like private jet access, lifetime free transactions, and exclusive merchandise
While the site promotes an impressive array of fake benefits and investor perks, its real objective is to:
- Trick users into connecting wallets
- Extract seed phrases or private keys
- Execute malicious smart contracts to drain cryptocurrency wallets
Fake Tokenomics and Roadmap
On token-x.live, the scammers provide what appears to be a fully developed tokenomics structure:
- Token Name: X Token
- Symbol: 𝕏
- Total Supply: 1 billion 𝕏
- Initial Price: $5.44
- Hard Cap: $20 million USD
- Distribution: 40% Public Sale, 25% Development, etc.
There is even a fabricated roadmap extending through Q4 2025, with fake features such as AI Neural Networks, Private Banking Services, and Enterprise Expansion.
None of this is real.
Bogus Benefits
Victims are lured in with promises of:
- Lifetime free transactions for holding 10,000+ tokens
- VIP perks like luxury car test drives and private jet access
- Elite tech insider access, exclusive merchandise, and one-on-one consultations with industry experts
These are nothing more than psychological bait to encourage investment and wallet connection.
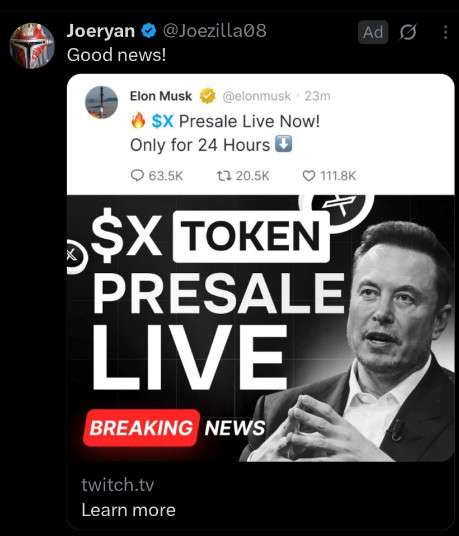
Exploiting FOMO and Trust in Elon Musk
A key tactic in the scam is using a fake Elon Musk tweet, which often appears as an ad or viral post. The tweet says:
“🔥 $X Presale Live Now! Only for 24 Hours ⏳”
This tweet is never posted from Elon Musk’s actual account. It is fabricated or created using hacked/fake profiles and image overlays to simulate authenticity.
The ad is often accompanied by a professionally designed graphic showing Elon Musk beside bold headlines like:
“$X TOKEN PRESALE LIVE – BREAKING NEWS”
All of this is engineered to build false credibility, trigger fear of missing out, and push users toward quick and unverified actions.
How the Scam Works
The $X Token scam is a classic case of crypto phishing, supercharged by fake credibility and urgency. Here’s how it typically plays out—from first contact to wallet drain.
Step 1: Social Media Ads or Posts Create Buzz
Scammers launch the campaign using fake Twitter/X posts, paid social ads, Discord messages, and YouTube comment spam. Many use deepfake videos, impersonated Elon Musk accounts, or altered tweets to promote the presale. The content typically includes phrases like:
- “🔥 $X Presale Live Now! Only for 24 Hours”
- “Official $X Token Launch – Backed by Elon Musk and OpenAI”
- “Get in early. Limited allocation remaining!”
This creates the illusion of urgency and exclusivity, pressuring users to act fast.
Step 2: Victims Click Through to token-x.live
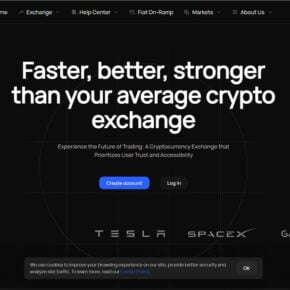
The link in the ad leads to a professionally designed website, token-x.live. It looks legitimate, with design elements mimicking real crypto projects and presale launchpads. The site claims to be backed by major players like:
- X (Twitter)
- Tesla
- Binance
- JPMorgan
- SpaceX
- Coinbase
Logos are displayed prominently to build trust. There’s a slick roadmap, fake team profiles, and tokenomics that include terms like “AI Neural Network Integration” and “Metaverse Expansion.”
Step 3: “Connect Wallet” Button Lures Users Deeper
To participate in the presale, users are prompted to click “Connect Wallet.” Supported wallets typically include:
- MetaMask
- Trust Wallet
- Phantom (Solana)
- WalletConnect
This is where the phishing truly begins.
The moment a wallet is connected, one of two things happens:
- The user is prompted to sign a transaction to “verify ownership” or “approve token purchase.”
- The site throws an error and redirects the user to a “manual verification” form, requesting their seed phrase or private key.
Step 4: Authorization or Seed Phrase Theft
In both scenarios, users unknowingly give full access to their wallet:
- Signing a transaction often grants smart contract approval, allowing the attacker to transfer tokens without additional permission.
- Submitting a seed phrase gives the scammer direct, irreversible access to the entire wallet.
The site may display a “Success” message or promise that $X tokens will be distributed after the presale ends.
But no tokens will ever arrive.
Step 5: Wallet Is Drained
Once the attacker has wallet access, a drain script is executed. This targets:
- High-value crypto like ETH, SOL, BNB
- Stablecoins such as USDT, USDC, DAI
- NFTs and DeFi positions
- Lesser-known tokens with market value
Funds are transferred to scam-controlled wallets and then laundered through mixers or swapped via decentralized exchanges, making them harder to trace.
Victims may not notice anything until they check their wallet later—or receive alerts showing unauthorized transactions.
Step 6: Scammers Disappear or Rebrand
After stealing the funds, scammers may:
- Take the site offline
- Redirect to a new phishing domain
- Delete social media accounts and burner wallets
- Relaunch the same scam under a different token name (e.g., $Z, $AI, $TWITTER)
It’s a rinse-and-repeat model that preys on greed, urgency, and trust in public figures.
What to Do If You Have Fallen Victim to This Scam
If you’ve connected your wallet, signed a transaction, or submitted your seed phrase to the $X Token scam, immediate action is critical.
1. Revoke Contract Approvals Immediately
If you signed a transaction, go to:
Search your wallet address and revoke access to any suspicious contracts.
2. Transfer Remaining Assets to a New Wallet
If your seed phrase was entered, your wallet is compromised forever. Immediately:
- Create a new wallet with a new seed phrase
- Transfer all funds and NFTs to the new address
- Avoid using the old wallet again
3. Scan Your Device
Run a malware and spyware scan using:
- Malwarebytes
- Bitdefender
- Norton
- Windows Defender (as a basic option)
Check browser extensions and remove any suspicious tools, especially those related to crypto wallets.
4. Report the Scam
Help stop the spread by reporting the scam to:
- Chainabuse
- Google Safe Browsing
- Twitter/X Support
- Reddit moderators in r/CryptoCurrency
Provide the URL, screenshots, wallet address interactions, and any messages received.
5. Alert Others
Even if your funds are gone, you can help others by:
- Posting a warning in Telegram and Discord communities
- Sharing your story on Twitter or Reddit
- Submitting a write-up to scam awareness sites
6. Monitor Wallets and Set Alerts
Use tools like:
These allow you to monitor wallet activity and spot unauthorized transfers in real-time.
7. Contact Crypto Exchanges (Optional)
If any of your assets went through an exchange like Binance, Coinbase, or KuCoin, contact their fraud departments immediately. While recovery is unlikely, some exchanges may freeze suspicious accounts if contacted fast enough.
The Bottom Line
The $X Token presale is a high-profile crypto scam leveraging fake branding, celebrity endorsements, and professional marketing to lure victims. It promises tokens, tech perks, and elite access—but instead, it steals from your wallet the moment you connect or share your credentials.
There is no official $X Token. Elon Musk is not launching a presale. Companies like OpenAI, Tesla, Binance, and SpaceX are not involved. Every part of this scheme is fake.
Protect yourself by:
- Never sharing your seed phrase
- Always verifying presales through official sources
- Double-checking URLs and endorsements
- Using hardware wallets for major funds
If something seems too good to be true, it usually is. In the world of Web3, security starts with skepticism.
Frequently Asked Questions (FAQ) About the $X Token Presale Scam
What is the $X Token Presale scam?
The $X Token Presale scam is a fraudulent crypto scheme that impersonates a legitimate token launch. It falsely claims backing from Elon Musk and major tech brands to trick users into connecting their wallets or providing private keys. Once a user interacts with the site, scammers use malicious contracts or stolen credentials to drain their crypto wallets.
Is the $X Token real?
No. There is no legitimate cryptocurrency project called “$X Token” associated with Elon Musk, X (formerly Twitter), OpenAI, Binance, or any of the brands mentioned on token-x.live. The token, its presale, and all associated benefits are entirely fabricated.
How do scammers steal my crypto through this presale?
After users visit the scam website and connect their wallet, they are asked to sign a transaction or enter their seed phrase. Signing the transaction can give scammers control over the wallet via smart contract permissions. If a seed phrase is provided, scammers can immediately access the wallet and transfer out all funds and tokens.
What are the red flags that show this is a scam?
Key warning signs include:
- Requests for seed phrases or wallet private keys
- Urgency tactics such as “only 24 hours left”
- Promises of unrealistic rewards like private jet access or lifetime free transactions
- Use of fake endorsements from Elon Musk and well-known companies
- Professionally designed but unverifiable websites with flashy tokenomics and roadmaps
What happens if I signed a transaction on the scam site?
If you signed a transaction, it may have granted the scammer access to your wallet through smart contract permissions. This allows them to transfer tokens without further approval. You should immediately revoke all wallet permissions and move remaining assets to a secure wallet.
Can I recover my stolen funds?
In most cases, no. Transactions on blockchain networks are irreversible. Once assets have been transferred to a scammer’s wallet, they are typically laundered through mixers or decentralized exchanges. Your best defense is quick action to protect any remaining assets.
How can I revoke wallet access after interacting with the scam?
Use reputable tools like:
- Revoke.cash
- Solana Explorer (for Solana wallets)
- Etherscan Token Approval Checker (for Ethereum-based wallets)
These tools help you disconnect malicious smart contracts from your wallet.
How do I report the $X Token scam?
You can report the scam to:
- Chainabuse
- Google Safe Browsing
- Social media platforms where the scam was promoted (Twitter/X, YouTube, etc.)
- Crypto forums like r/CryptoCurrency or relevant Discord servers
Providing wallet addresses, screenshots, and the site URL helps investigators act faster.
How do I avoid scams like this in the future?
- Never share your wallet seed phrase or private key
- Always verify token presales through official project websites and social media
- Be cautious of ads or posts that promise high rewards and exclusive access
- Use a hardware wallet for added security
- Install browser wallet extensions from official sources only
Is Elon Musk actually involved in this presale?
No. Elon Musk has not launched any token or endorsed the $X Token presale. Any tweet, video, or image suggesting otherwise is fake or manipulated. Always verify high-profile endorsements directly from verified accounts before trusting them.