cruelsister
Level 43
Thread author
Verified
Honorary Member
Top Poster
Content Creator
Well-known
Forum Veteran
- Content source
- https://www.youtube.com/watch?v=YQwKeYcF39I
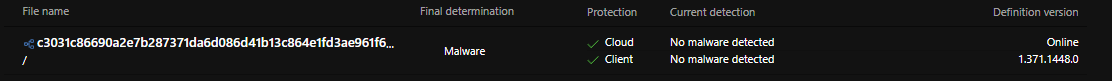
Ever wonder how fast Microsoft enters previously submitted malware into its AV database?
Last edited: