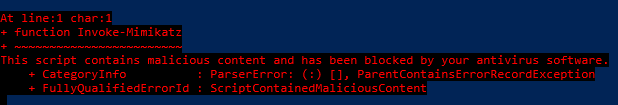
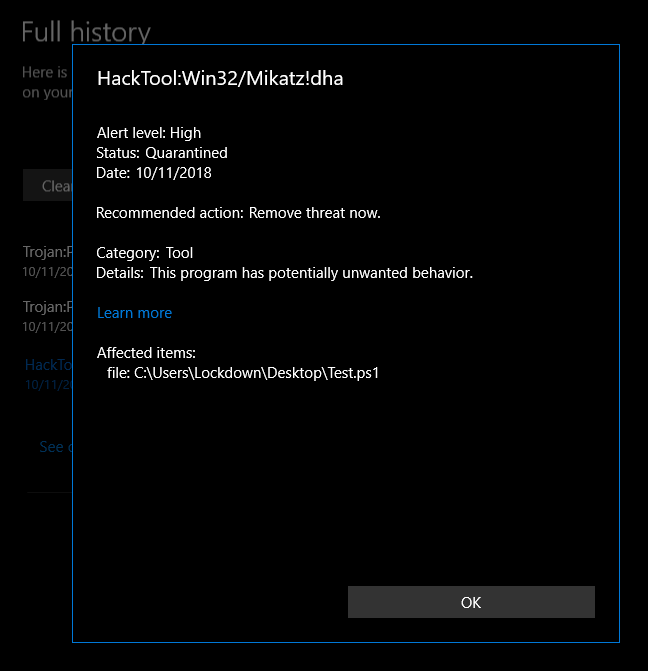
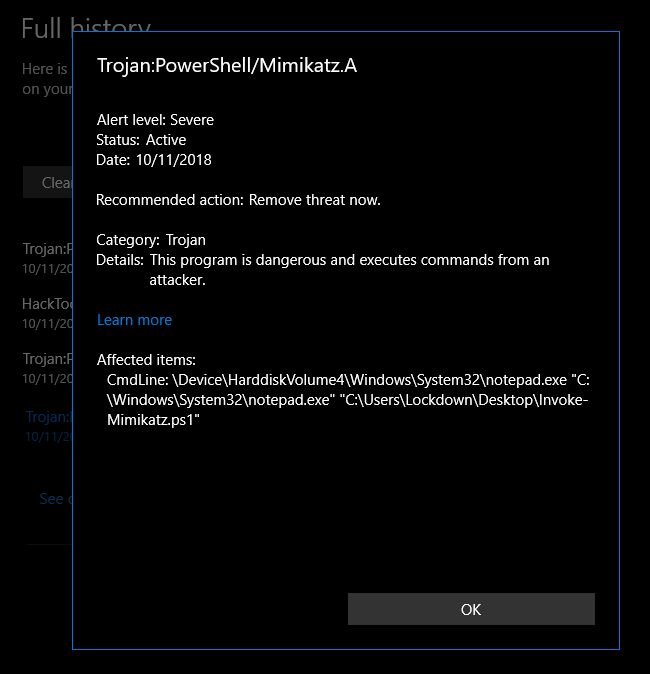
So it looks like even Windows Defender doesn't know how to implement AMSI right.
Microsoft's Windows Defender Team are the only team which know exactly how to implement AMSI properly along with having access to all of the knowledge on what can go wrong and what will or won't trigger it... unless you reverse-engineer everything and even then you may have missed something.
Microsoft intentionally withhold documentation and it causes third-parties to become confused. This can lead to improper implementations which are unreliable and unstable in the long-run and cause an unknown number of issues. It's Microsoft's fault. The public documentation may as well not exist at all in its current state because it's absolutely atrocious - it isn't very descriptive at all and this isn't helpful on any level.
It's a pathetic state of affairs.
Anyway... here is some information from me that may help you guys. Note, this information is from my own experience and may be inaccurate for Windows Defender's case specifically (since I do not have Windows Defender insider knowledge).
1. When you open PowerShell yourself, that triggers AMSI. When you try to execute any scripts by typing/copy-pasting and entering them, that also triggers AMSI.
2. If you open a PowerShell script from a file and then it loads in PowerShell, this will trigger AMSI as well. The same as #1 will trigger AMSI.
However, Windows Defender also supports on-execution scanning, and if PowerShell is included for this... then this will happen before AMSI can be triggered (because it'd be before PowerShell actually tries to execute the script - AMSI doesn't let you scan the original script, it scans the interpreters version which means obfuscation is also defeated).
Therefore, I suspect what is going on here is the normal Windows Defender scanning engine is identifying the PowerShell script for the non-AMSI detection's. At this point, AMSI scanning probably hasn't even been included for that session unless PowerShell has actually tried to execute the script, since it'd be scanning earlier before this point. The first test which had the AMSI detection would have triggered AMSI but it wouldn't have triggered the normal Windows Defender scanning engines (e.g. for on-execution).