It is very common to see Portable Executable (PE) file infector viruses. It is a bit more unusual to see file infection via the raw file system — in this case, a Master Boot Record (MBR) file system infector.
Partly this is because PE infectors are less troublesome to create — they can be more robust, are easier to develop, and to control. In contrast, MBR infectors are more complex and their size is limited to 62 sectors (7C00H). Also, there's less room for error — a small mistake or bug in an MBR file system infector causes the system to be unbootable.
So an MBR file system infector such as Trojan:W32/Smitnyl.A (98b349c7880eda46c63ae1061d2475181b2c9d7b), which appears to be distributed via some free file-sharing networks, seems worth a quick analysis, even if it only targets one portable executable system file and the infection is straightforward compared to common virus file infectors.
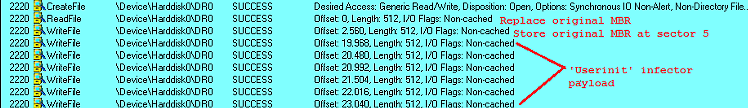
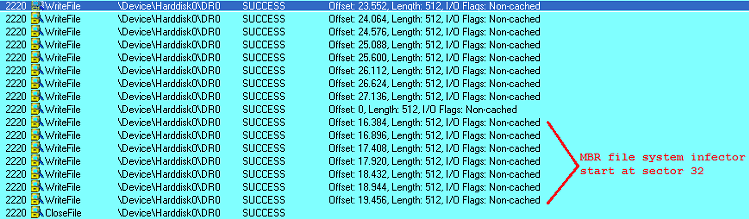
Smitnyl.A first infects the MBR via raw disk access. Then it replaces it with a malicious MBR containing the file infector routine (stored at sector 32).
More details - link
Partly this is because PE infectors are less troublesome to create — they can be more robust, are easier to develop, and to control. In contrast, MBR infectors are more complex and their size is limited to 62 sectors (7C00H). Also, there's less room for error — a small mistake or bug in an MBR file system infector causes the system to be unbootable.
So an MBR file system infector such as Trojan:W32/Smitnyl.A (98b349c7880eda46c63ae1061d2475181b2c9d7b), which appears to be distributed via some free file-sharing networks, seems worth a quick analysis, even if it only targets one portable executable system file and the infection is straightforward compared to common virus file infectors.
Smitnyl.A first infects the MBR via raw disk access. Then it replaces it with a malicious MBR containing the file infector routine (stored at sector 32).


More details - link