omidomi
Level 71
Thread author
Verified
Honorary Member
Top Poster
Malware Hunter
Well-known
Forum Veteran
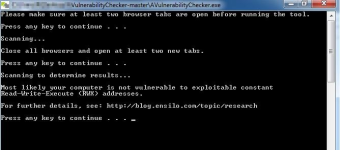
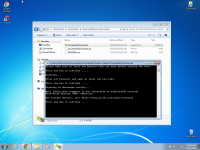
I find a tool in Github whom Test your AV Vulnerability here:
BreakingMalware/AVulnerabilityChecker · GitHub
i want all member test it with their AVs to see which program is vulnerable and which one is no vulnerable, I test EIS its safe.
stay for your test
*These avs pass the test successfully:
Windows Defender
Avira AV Pro + Firefox = not vulnerable
Norton
Emsisoft
Kaspersky
Watchdog anti malware
Eset
Qihoo
Sophos
AVG
Bitdefender
Firefox + Webroot = Passed
Firefox + Avira Pro = Passed
Agnitium
Secure Alive
McAfee
Avira AV Pro + HitmanPro.Alert + Firefox
Avira AV Pro + HitmanPro.Alert + Chrome
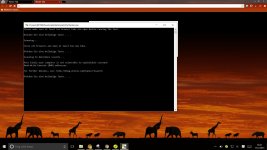
*These avs failed in the test :
Chrome + Webroot = Failed
Avira AV Pro + Chrome
Chrome + Avira Pro
Baidu
Bitdefender Internet Security 2016
Trend Micro
Avast
Bullgaurd
BreakingMalware/AVulnerabilityChecker · GitHub
i want all member test it with their AVs to see which program is vulnerable and which one is no vulnerable, I test EIS its safe.
stay for your test
*These avs pass the test successfully:
Windows Defender
Avira AV Pro + Firefox = not vulnerable
Norton
Emsisoft
Kaspersky
Watchdog anti malware
Eset
Qihoo
Sophos
AVG
Bitdefender
Firefox + Webroot = Passed
Firefox + Avira Pro = Passed
Agnitium
Secure Alive
McAfee
Avira AV Pro + HitmanPro.Alert + Firefox
Avira AV Pro + HitmanPro.Alert + Chrome
*These avs failed in the test :
Chrome + Webroot = Failed
Avira AV Pro + Chrome
Chrome + Avira Pro
Baidu
Bitdefender Internet Security 2016
Trend Micro
Avast
Bullgaurd
Last edited: