That makes sense to me. I'm not sure if it was set, for some reason in the settings only for essential Windows programs and Avast correctly changed it to allowed for all programs? But I'm not sure why or if Windows would have initially set it that way? But, I'll leave it as it is on both laptops.DEP is a setting since way back, I had always used the option 'turn on DEP for all programs',
Question Avast custom installation
- Thread starter Divine_Barakah
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Please provide comments and solutions that are helpful to the author of this topic.
Back then DEP was a new thing. And some programs do fail when DEP is turned on for them.
I think execution in memory space is when programmers use 'system.exec ("some command") ' . 'some command' is a data string residing in a section of memory reserved for data.
So it sounds like a normal user wouldn't have to worry about leaving it in the Windows default, being enabled for all programs and services. I've never noticed or had any issue that I'm aware of.I think execution in memory space is when programmers use 'system.exec ("some command") ' . 'some command' is a data string residing in a section of memory reserved for data.
No problemI don't know. Never used F-Secure before.
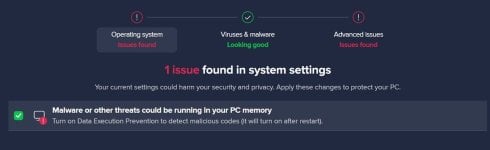
edit: @lokamoka820 I changed DEP back to its default, restarted my laptop and ran a Avast Smart Scan. It seems to want to change it to the "more secure" enable for all option? I did the same thing with my F-Secure laptop, ran a Quick scan but it didn't give me a notification that I had changed the DEP setting.
Last edited:
I'm answering my own question, F-Secure did not make the DEP change, Avast did. I previously had Avast on both Laptops before I uninstalled it on one and replaced it with F-Secure. I'm sure on the initial Avast Smart Scan, I allowed it to change DEP for all programs and services. When I uninstalled it, it did no revert the change back to only for Windows essential programs....my mornings wake up epiphany LOLThen why were both of my notebooks enabled for all? Did both F-Secure (in a setting below) and Avast change it?
View attachment 293625
I asked for Perplexities advice, and it seems for the average user, Avast was changing it (asking to make a change) as a security enhancement. @Victor M thank you for your posts
Enabling DEP (Data Execution Prevention) for all programs does improve security, but it can occasionally break older or niche software. The safest general approach is to enable it for all programs and add exceptions only if something you trust stops working.
Microsoft’s guidance
Windows enables DEP by default for core system programs and services. Microsoft and security vendors state that protection can be increased by having DEP monitor all programs, not just essential Windows components.
Pros and cons of “all programs”
Turning DEP on for all programs extends this memory protection to your entire userland, reducing the chance that a vulnerable third‑party app is used as an entry point. However, some older or specialized applications that generate or execute code in unusual ways (for example, certain compilers, simulation tools, or in‑house utilities) may crash or refuse to start under strict DEP.
Typical issues you might see
- Older 32‑bit or legacy business apps failing to launch or crashing immediately.
- Custom tools or obscure utilities being terminated with a DEP error even though they are benign.
In short: yes, use DEP for all programs for better security in most setups, but be prepared to whitelist only the rare, trustworthy applications that cannot run under it.
Last edited:
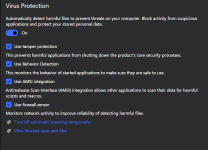
The same result of Norton smart scan.@Jonny Quest I searched for the settings that Avast modifies during the "Operating System Scanning" phase and found them. The one I mentioned called "Data Execution Prevention" and appear in the following image:
View attachment 293621
To check if it has been modified in your system, you need to do the following:
The default setting should be as shown in the following image:
- Open the Control Panel.
- Click System and Security > System > Advanced System Settings.
- Once you are on the Advanced tab, click Settings.
- Click the Data Execution Prevention tab.
View attachment 293622
If the other option is selected, then Avast has modified it.
This was really difficult to find.
Do you support Avast's recommendation to modify the default settings for Data Execution Prevention (DEP)? Is this better?DEP is a setting since way back, I had always used the option 'turn on DEP for all programs',
As far as I know, only the Avast antivirus family changes this setting, other antiviruses don't because the user will be safe anyway. I think this is just a way to show that Avast is doing more, while I think this setting will make Windows use more resources to scan each application rather than the essential ones.No problemWith Avast, does it think it's protecting our PC's better by enabling (suggesting) DEP for all, wouldn't that be a more secure environment for a normal user?
edit: @lokamoka820 I changed DEP back to its default, restarted my laptop and ran a Avast Smart Scan. It seems to want to change it to the "more secure" enable for all option? I did the same thing with my F-Secure laptop, ran a Quick scan but it didn't give me a notification that I had changed the DEP setting.
View attachment 293626
Regarding your F-Secure laptop, are you sure you have never installed Avast or AVG on it?
Yep, that is what happened, as I mentioned above (post #29). I had previously installed Avast on that laptopRegarding your F-Secure laptop, are you sure you have never installed Avast or AVG on it?
I always change DEP settings to all programs; I use MD, so I need every possible, single help.Do you support Avast's recommendation to modify the default settings for Data Execution Prevention (DEP)? Is this better?
In case I caused app malfunction (never encountered before), I can easily add it to the "allow" list.
Yes, I noticed that after posting the replyYep, that is what happened, as I mentioned above (post #29). I had previously installed Avast on that laptop
Apologies, but I didn't realize there was also this option until Gemini mentioned it. We can't tweak those settings during install, but we don't need to go to Windows Apps/Avast/ Modify like I previously mentioned. Instead, go to the Avast UI Settings/General/Troubleshooting/Still having problems?/Add modify components, will bring us to that window and the feature options to enable, or disable.

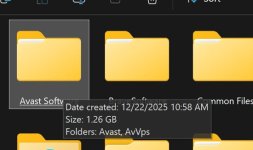
Does removing components actually work, or does Avast just hide them from the GUI? I remember once installing just the core components of Avast, and it was larger than 1 GB.Apologies, but I didn't realize there was also this option until Gemini mentioned it. We can't tweak those settings during install, but we don't need to go to Windows Apps/Avast/ Modify like I previously mentioned. Instead, go to the Avast UI Settings/General/Troubleshooting/Still having problems?/Add modify components, will bring us to that window and the feature options to enable, or disable.
View attachment 293932
I'm not sure, that's a good questionDoes removing components actually work, or does Avast just hide them from the GUI? I remember once installing just the core components of Avast, and it was larger than 1 GB.
Edit: The folder size may not change when we disable a feature, in case we enable it again, it will be easily re-accessed from the folder. We can probably confirm it by trying to run or load that feature, when its been disabled?
Last edited:
Your guess is correct; all components already have landed on drive, regardless of which one you select to install.Does removing components actually work, or does Avast just hide them from the GUI? I remember once installing just the core components of Avast, and it was larger than 1 GB.
You can even notice adding or removing components doses not take more than a couple of seconds.
I always set DEP for all programs. Never ran into any issues.
Few portabole programs might face issues, but I never had before with the few portables I have used.I always set DEP for all programs. Never ran into any issues.
You may also like...
-
-
Privacy News Avast users awarded $15.3 million for misleading privacy claims
- Started by nicolaasjan
- Replies: 3
-
New Update The one thing i have found different from in Norton from AVG and Avast.
- Started by nickstar1
- Replies: 38
-
Microsoft may soon allow IT admins to uninstall Copilot
- Started by Parkinsond
- Replies: 2
-