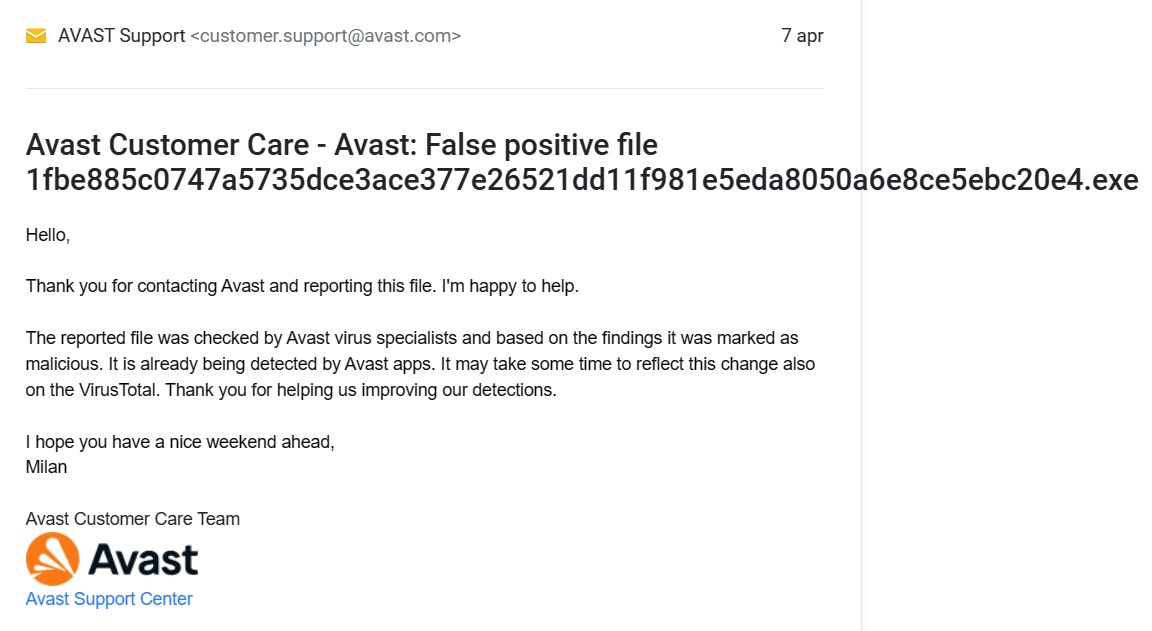
Hi, everyone! It's been almost three days since AVG/Avast customer support indicated that a sample I uploaded is indeed a malware, but it's still not being detected by their products. Looks like a major hole in AVG/Avast protection to me... Ordinary users are not supposed to be hunting for malware, and to be doing their job for them. There's no other explanation for this ridiculous situation, unless someone on the inside in AVG/Avast doesn't want this particular malware to be detected. 'Cause this one is detected virtually by every other security vendor, except by AVG/Avast. Makes me wonder if it's because this malware was actually originated by someone from AVG/Avast VirusTotal They are saying "it is already being detected by Avast apps", but it is a lie...
AVG/Avast could be lying....
- Thread starter Pilot777
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
There must a logical explanation for this, Easter.
Are you able to verify that VirusTotal has the latest updates for the Avast engine?
Are you able to verify that VirusTotal has the latest updates for the Avast engine?
Perhaps they are right and it is indeed marked as malicious by Avast/AVG but not updated in the VirusTotal database yet. In line with the VirusTotal report, the hash goes undetected by F-Secure even though it uses the signatures of Bitdefender, and Bitdefender does detect it
F-Secure uses Avira.undetected by F-Secure even though it uses the signatures of Bitdefender
Virustotal detection and in-product detections are not always the same.They are saying "it is already being detected by Avast apps", but it is a lie...
Anyway, I just checked, it's not detected by Avast. It seems the file is corrupt. It won't run, so maybe that's why it's not detected.
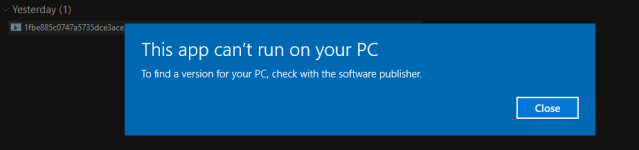
GrandCrab is still extensively distributed to customers (RAAS) with many of them malformed as SeriousHoax correctly points out. Of those that recently been in the Wild, AVAST has no problems detecting those that do actually work but will blow off those that won't run.
So although the VT results may rightly make an AVAST user concerned it is in this case of no consequence.
So although the VT results may rightly make an AVAST user concerned it is in this case of no consequence.
This. It's Easter. AVAST is European and owned by Norton which is American. Big time of the year in the Christian world. Bigger than XMAS.There must a logical explanation for this, Easter.
@Pilot777 hello and belated welcome to MalwareTips.
As @cruelsister and @SeriousHoax previously pointed out, this is ransomware-as-a-service (RAAS) and the sample is malformed for one reason or another, perhaps someone’s had a little play with it.
As a security vendor Avast does not participate in malware creation and distribution (it is a criminal offence as well). In fact, Avast has released decryptors throughout the years for various ransomware families/strains.
I believe the Avast parser may be unable to read the file properly or due to the sample being damaged, they may have refused to add detection, as a properly-working sample may already be covered by other detections and protection methods. It my have been miscommunication between the support agent and the analyst. For more information, it would be best to reply to this email and ask Avast.
It has been discussed by @struppigel who works at GData on another thread that not everything that gives off a malicious vibe gets added to definitions. They are not a recycle bin, they are operated in accordance with strict policies that different vendors have implemented. For example Symantec would refuse to add artefacts by themselves not malicious (for example a driver that has been used as part of BYOVD attack or a PDF that contains links to malicious sites). Avira would add a detection for everything in definitions.
Avast would certainly add a detection for something that’s truly malicious and has been sent to them, regardless whether it’s a working day or festive.
As @cruelsister and @SeriousHoax previously pointed out, this is ransomware-as-a-service (RAAS) and the sample is malformed for one reason or another, perhaps someone’s had a little play with it.
As a security vendor Avast does not participate in malware creation and distribution (it is a criminal offence as well). In fact, Avast has released decryptors throughout the years for various ransomware families/strains.
I believe the Avast parser may be unable to read the file properly or due to the sample being damaged, they may have refused to add detection, as a properly-working sample may already be covered by other detections and protection methods. It my have been miscommunication between the support agent and the analyst. For more information, it would be best to reply to this email and ask Avast.
It has been discussed by @struppigel who works at GData on another thread that not everything that gives off a malicious vibe gets added to definitions. They are not a recycle bin, they are operated in accordance with strict policies that different vendors have implemented. For example Symantec would refuse to add artefacts by themselves not malicious (for example a driver that has been used as part of BYOVD attack or a PDF that contains links to malicious sites). Avira would add a detection for everything in definitions.
Avast would certainly add a detection for something that’s truly malicious and has been sent to them, regardless whether it’s a working day or festive.
Last edited:
That is true, biblically speaking. But in reality, Christmas is much bigger.This. It's Easter. AVAST is European and owned by Norton which is American. Big time of the year in the Christian world. Bigger than XMAS.
@Pilot777 hello and belated welcome to MalwareTips.
As @cruelsister and @SeriousHoax previously pointed out, this is ransomware-as-a-service (RAAS) and the sample is malformed for one reason or another, perhaps someone’s had a little play with it.
As a security vendor Avast does not participate in malware creation and distribution (it is a criminal offence as well). In fact, Avast has released decryptors throughout the years for various ransomware families/strains.
I believe the Avast parser may be unable to read the file properly or due to the sample being damaged, they may have refused to add detection, as a properly-working sample may already be covered by other detections and protection methods. It my have been miscommunication between the support agent and the analyst. For more information, it would be best to reply to this email and ask Avast.
It has been discussed by @struppigel who works at GData on another thread that not everything that gives off a malicious vibe gets added to definitions. They are not a recycle bin, they are operated in accordance with strict policies that different vendors have implemented. For example Symantec would refuse to add artefacts by themselves not malicious (for example a driver that has been used as part of BYOVD attack or a PDF that contains links to malicious sites). Avira would add a detection for everything in definitions.
Avast would certainly add a detection for something that’s truly malicious and has been sent to them, regardless whether it’s a working day or festive.
My boy F-Secure is also lacking according to VT. Avast, AVG, Avira, and F-Secure are the only four vendors of any consequence that don’t detect this file. Do you think Avira decided not to add definitions due to the sample being corrupt? And regardless of what Avira does, I would hope F-Secure adds its own sig, since they say they don’t just rely on Avira but also have their own engines.
Virgo, DeepGuard, and Hydra, where you at? Gotta pick up the slack when Capricorn is sleeping.
In the beginning of the file this is what they’ve placed:My boy F-Secure is also lacking according to VT. Avast, AVG, Avira, and F-Secure are the only four vendors of any consequence that don’t detect this file. Do you think Avira decided not to add definitions due to the sample being corrupt? And regardless of what Avira does, I would hope F-Secure adds its own sig, since they say they don’t just rely on Avira but also have their own engines.
Virgo, DeepGuard, and Hydra, where you at? Gotta pick up the slack when Capricorn is sleeping.
Should be:MZ......................@...............................................!..L.!This .D...Am cannot be run in DOS mode....$.......%..ga~o4a~o4a~o4...4{~o4...4F~o4...4.~o4h..4h~o4a~n46~o4.^.*`~o4...4`~o4...s`~o4Richa~o4................PE..L.....)[...........
!This program cannot be run in DOS mode. $ <rich header> PE
This is what renders the sample unable to execute and before scanning a file, an AV must use parsers to discover the true file type. The invalid headers may confuse some parsers and because of that, the scan engine may be unable to handle the file properly.
Most likely somebody just wanted to pass a quick static analysis to see if the sample is detected and they damaged the file.
Last edited:
Btw just for testing purposes, in Avast Resident Shield settings, there is an option called “Test Whole Files”. Can somebody enable that and scan the file? Also, maybe disable scanning by file type and select scan all files by extension. Let’s see if the scanner is failing to calculate the offset or something of this sort.
I don’t have access to the real file, I just saw the preview on Joe Sandbox from my phone.
I don’t have access to the real file, I just saw the preview on Joe Sandbox from my phone.
Last edited:
Btw just for testing purposes, in Avast Resident Shield settings, there is an option called “Test Whole Files”. Can somebody enable that and scan the file? Also, maybe disable scanning by file type and select scan all files by extension. Let’s see if the scanner is failing to calculate the offset or something of this sort.
Interested in this as well. When I used Avast many many moons ago, I always made these adjustments so everything was scanned. That + letting Avast re-scan the same files, even if there were no changes. Some AVs don’t scan a file a second time after the first scan unless they detect a “change” in it.
For a paranoic like me, that was just asking for trouble. I never underestimate malware authors from finding an ingenious way to trick an AV into thinking a file hasn’t been changed, when it has. And so the AV fails to stop the infection even if they had the right sigs.
With SHA256 I don’t think it’s possible, more likely a file will get cached and after a signature is added (if the cache is not purged on definitions update) it may not be scanned for some time or until a system restart.For a paranoic like me, that was just asking for trouble. I never underestimate malware authors from finding an ingenious way to trick an AV into thinking a file hasn’t been changed, when it has. And so the AV fails to stop the infection even if they had the right sigs.
They don’t reveal too much information on how the cache is managed (for obvious reasons) but I would assume they cache files that are trusted and don’t cache unknown files so they could be rescanned again and again with streaming updates.
Even on files that are added to persistent cache, these will have digital signature. Avast can revoke the digital signature at any time using their Win32/BadSig detection and this will remove the file.
Welcome.
I had this situation with AVG recently:
Wanting to test AVG for threat detection - I downloaded some malware samples.
After extracting, AVG was silent detecting nothing.
After analyzing the files on VT - AVG and Avast should detect these files as a threat.
Databases like the AVG program itself up to date.
Could it be that these files are corrupted ? That is why they are not detected ?
I had this situation with AVG recently:
Wanting to test AVG for threat detection - I downloaded some malware samples.
After extracting, AVG was silent detecting nothing.
After analyzing the files on VT - AVG and Avast should detect these files as a threat.
Databases like the AVG program itself up to date.
Could it be that these files are corrupted ? That is why they are not detected ?
VirusTotal is a tool used mainly for analysts and for reference. Detections on VirusTotal might differ from detections in any actual product that’s deployed on wide scale. Without having the samples it’s hard to tell but I would assume there was some factor of non-maliciousness. Did you try executing them? What were they? If they were installers, did you have scanning of compressed files enabled?Welcome.
I had this situation with AVG recently:
Wanting to test AVG for threat detection - I downloaded some malware samples.
After extracting, AVG was silent detecting nothing.
After analyzing the files on VT - AVG and Avast should detect these files as a threat.
Databases like the AVG program itself up to date.
Could it be that these files are corrupted ? That is why they are not detected ?
Try to enable scanning of archives, scanning for PUP and tools, testing of whole files and scan by extension, not by content type. You can change all these settings for contextual scan and then right click on these files, and scan them.AVG is set to maximum
I have these files on disk still but I haven't run them
Try to enable scanning of archives, scanning for PUP and tools, testing of whole files and scan by extension, not by content type. You can change all these settings for contextual scan and then right click on these files, and scan them.
I have it set up like this
All 3 samples are 10-year-old+. One of them surely is a false positive, it is a Chinese game, signed with a valid signature (not revoked). The other 2 are infostealers/keyloggers, but because they’ve long been decommissioned, they are not a threat to confidentiality, integrity or availability of information. Hence, they’ve been removed from definitions. They are not detected on VT either.I have it set up like this
I'm happy to report that the issue has been resolved. Well done, AVG/Avast!
You may also like...
-
Hot Take Avira, AVG, Avast, BullGuard will combination in future!! (Maybe)
- Started by Lintianyun Luo
- Replies: 19
-
-
Malware News Malware bypassed macOS Gatekeeper by abusing Apple's notarization proccess
- Started by enaph
- Replies: 1
-

