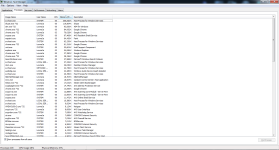
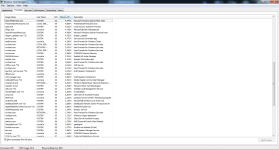
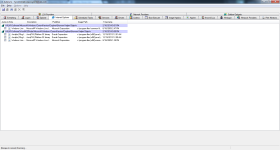
"";"IRP hook, C:\Windows\system32\DRIVERS\mouclass.sys IRP_MJ_READ -> EagleX64.sys +0x14CC0, C:\Windows\system32\drivers\EagleX64.sys";"Cannot be removed
The data is invalid."
"";"IRP hook, C:\Windows\system32\DRIVERS\mouclass.sys IRP_MJ_PNP -> EagleX64.sys +0x14F80, C:\Windows\system32\drivers\EagleX64.sys";"Cannot be removed
The data is invalid."
"";"IRP hook, C:\Windows\system32\DRIVERS\kbdclass.sys IRP_MJ_READ -> EagleX64.sys +0x131C0, C:\Windows\system32\drivers\EagleX64.sys";"Cannot be removed
The data is invalid."
"";"IRP hook, C:\Windows\system32\DRIVERS\kbdclass.sys IRP_MJ_PNP -> EagleX64.sys +0x134D0, C:\Windows\system32\drivers\EagleX64.sys";"Cannot be removed
The data is invalid."
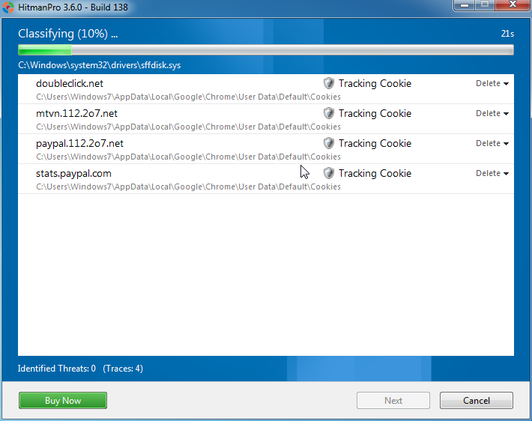
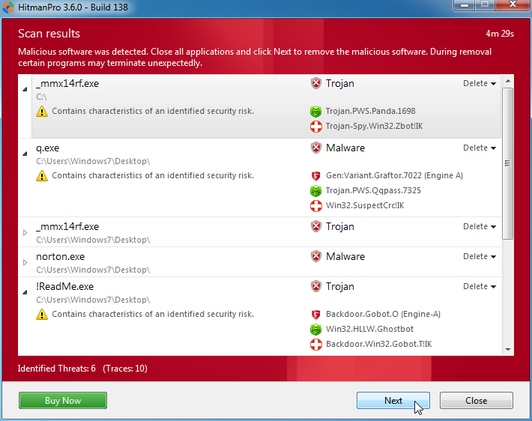
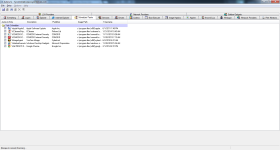
It doesn't want to remove.
I will provide the scans shortly.
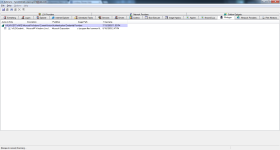
The data is invalid."
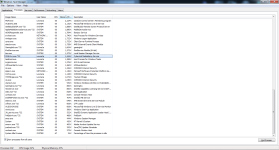
"";"IRP hook, C:\Windows\system32\DRIVERS\mouclass.sys IRP_MJ_PNP -> EagleX64.sys +0x14F80, C:\Windows\system32\drivers\EagleX64.sys";"Cannot be removed
The data is invalid."
"";"IRP hook, C:\Windows\system32\DRIVERS\kbdclass.sys IRP_MJ_READ -> EagleX64.sys +0x131C0, C:\Windows\system32\drivers\EagleX64.sys";"Cannot be removed
The data is invalid."
"";"IRP hook, C:\Windows\system32\DRIVERS\kbdclass.sys IRP_MJ_PNP -> EagleX64.sys +0x134D0, C:\Windows\system32\drivers\EagleX64.sys";"Cannot be removed
The data is invalid."
It doesn't want to remove.
I will provide the scans shortly.