Shameless promotion: I gently urge all MT Brave users to get active on Brave Community. Help make Brave even better! 
Brave Browser Feature Review (release v.1.3.115 Windows)
- Thread starter oldschool
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Shameless promotion: I gently urge all MT Brave users to get active on Brave Community. Help make Brave even better!
Oh no, the walk of shame? I won't survive!
Here's an example of what I like about Brave:

Aa-ron
Feb 13
If you visit a site and disable Sheilds,
e.g.

image758×736 53.6 KB
It will add it to the Allow list automatically.

image1384×1130 58.4 KB
Brilliant Shields UI! Easy on the eyes and supremely functional!

Aa-ron
Feb 13
If you visit a site and disable Sheilds,
e.g.

image758×736 53.6 KB
It will add it to the Allow list automatically.

image1384×1130 58.4 KB
Brilliant Shields UI! Easy on the eyes and supremely functional!
I don't know if I posted this on another thread, but I thought some of you may have an interest in this:
Source: brave/brave-browser
_______________________________________________________
pes edited this page 23 days ago · 7 revisions
What is Fingerprinting Protection?
Fingerprinting Protection is a privacy feature that makes it harder for sites to track you while you browse.
Warning: enabling Fingerprinting Protection might cause some sites to display incorrectly.
Technical Details
Brave includes best-effort defense against browser fingerprinting. Broadly speaking, browser fingerprinting is the detection of browser and operating system features that differ between users for the purpose of covertly identifying users and tracking them across the web. Although fingerprinting attacks will always be possible, it is worthwhile for us to make these attacks as slow / costly / difficult as possible.
Brave includes two types of fingerprinting protections, (i) blocking, removing or modifying APIs, to make Brave instances look as similar as possible, and (ii) randomizing values from APIs, to prevent cross session and site linking (e.g. making Brave instances look different to websites each time).
In cases where we block, remove or modify API behavior, we attempt to return empty, or non-identifying values, that have the "shape" of expected values, to minimize web compatibility issues.
In cases where we randomize API values, we attempt to make modifications that are imperceivable to humans, but distinguishing to computers / fingerprinters. These randomization values are derived from a seed that changes per session, and per eTLD+1. Third party frames and script share the seed value of the top level, eTLD+1 domain. This approach is especially useful in fingerprinters that hash together a large number of semi-identifiers into a single identifier, since randomizing just one value "poisons" the entire fingerprint.
Fingerprinting methods blocked in Fingerprinting Protection Mode
Privacy protection enabled regardless of whether Fingerprinting Protection Mode is on
This list is not complete. See brave/brave-browser for other things which are disabled in Brave but not in Chrome.
See https://community.brave.com/t/how-d...ing-protection-and-make-sure-that-its-working.
Why does panopticlick.eff.org or some other site say that I am fingerprintable?
Although useful for raising awareness of fingerprinting techniques, sites like Panopticlick are not a perfect indicator of how fingerprintable your browser is. Some known limitations are:
Exceptions
Brave makes a small number of exceptions for sites that require functionality that could be used for fingerprinting, but which is used for benign and user-serving purposes. These exceptions are built into Brave, and can be found in Brave's source code.
TODO
Source: brave/brave-browser
_______________________________________________________
pes edited this page 23 days ago · 7 revisions
What is Fingerprinting Protection?
Fingerprinting Protection is a privacy feature that makes it harder for sites to track you while you browse.
Warning: enabling Fingerprinting Protection might cause some sites to display incorrectly.
Technical Details
Brave includes best-effort defense against browser fingerprinting. Broadly speaking, browser fingerprinting is the detection of browser and operating system features that differ between users for the purpose of covertly identifying users and tracking them across the web. Although fingerprinting attacks will always be possible, it is worthwhile for us to make these attacks as slow / costly / difficult as possible.
Brave includes two types of fingerprinting protections, (i) blocking, removing or modifying APIs, to make Brave instances look as similar as possible, and (ii) randomizing values from APIs, to prevent cross session and site linking (e.g. making Brave instances look different to websites each time).
In cases where we block, remove or modify API behavior, we attempt to return empty, or non-identifying values, that have the "shape" of expected values, to minimize web compatibility issues.
In cases where we randomize API values, we attempt to make modifications that are imperceivable to humans, but distinguishing to computers / fingerprinters. These randomization values are derived from a seed that changes per session, and per eTLD+1. Third party frames and script share the seed value of the top level, eTLD+1 domain. This approach is especially useful in fingerprinters that hash together a large number of semi-identifiers into a single identifier, since randomizing just one value "poisons" the entire fingerprint.
Fingerprinting methods blocked in Fingerprinting Protection Mode
- WebRTC IP leakage
- SVG fingerprinting (specifically, the SVGTextContentElement.prototype.getComputedTextLength and SVGPathElement.prototype.getTotalLength methods)
- HSTS fingerprinting
- Client Hints
- Media Streams: Enumerate Devices
Privacy protection enabled regardless of whether Fingerprinting Protection Mode is on
This list is not complete. See brave/brave-browser for other things which are disabled in Brave but not in Chrome.
- 3rd party cookies and referers blocked by default due to the third party tracking risk
- User-Agent is set to Chrome except on a few sites that need it for major functionality to work to prevent sites from using Brave's UA as a tracking mechanism.
- navigator.plugins and navigator.mimeTypes is empty unless you've enabled Flash to trigger HTML5 fallback for Flash whenever possible.
- Connections to known tracking domains are blocked via the Ad block Rust library in a list similar to Disconnect.
- Battery Status API is disabled because the battery level can be used as a tracking signal.
- navigator.credentials is disabled on desktop prior to C73; we are re-enabling it to support webauthn.
- Web Bluetooth is disabled on desktop due to us not seeing much benefit to enabling it right now
- We are also planning on disabling client-hints, see Disable Client-Hints in brave · Issue #3539 · brave/brave-browser for rationale
See https://community.brave.com/t/how-d...ing-protection-and-make-sure-that-its-working.
Why does panopticlick.eff.org or some other site say that I am fingerprintable?
Although useful for raising awareness of fingerprinting techniques, sites like Panopticlick are not a perfect indicator of how fingerprintable your browser is. Some known limitations are:
- Panopticlick only reports your uniqueness relative to the population of users visiting Panopticlick, which is almost certainly skewed relative to the entire population of users on the web. For instance, imagine that a very large number of Tor Browser users visit Panopticlick because they're trying to test their Tor Browser privacy settings. If you then visit Panopticlick in Chrome with default settings, you will then appear as more identifiable than Tor Browser users despite the fact that Chrome with default settings is more popular than Tor Browser overall. Similarly, because many Panopticlick users care about privacy and turn on Do Not Track, Panopticlick reports that users are less unique when they have DNT turned on than off, even though probably less than 12% of web users have DNT enabled.
- Panopticlick does not account for the fact that randomized fingerprint values are an effective way to prevent real-world fingerprinting. For instance, if Brave browser randomized canvas fingerprints on every page request, then it would be impossible for a site to track a specific Brave user across requests using canvas fingerprinting. However, because the randomized values would be unique, Panopticlick would report Brave as being highly canvas-fingerprintable.
Exceptions
Brave makes a small number of exceptions for sites that require functionality that could be used for fingerprinting, but which is used for benign and user-serving purposes. These exceptions are built into Brave, and can be found in Brave's source code.
TODO
- Decrease JS timer resolution
- Limit fonts fingerprinting: Limit fingerprinting via fonts · Issue #816 · brave/brave-browser
- Limit fingerprinting via viewport/screen size: Window size is a fingerprinting vector · Issue #720 · brave/brave-browser
- Lots more at brave/brave-browser and brave/brave-browser
Actually, if you test Brave at browserleaks.com I doubt you can get good fingerprint results
Actually, if you test Brave at browserleaks.com I doubt you can get good fingerprint results
I've tested Brave at many sites. It's not as simple and as clear-cut as you make it sound.
Edit: If you read Brave's goals and the referenced links in addition to other reading you will see how many methods go into fingerprinting. It's much more than any one factor.
Last edited:
Adopting API behavior from within the browser, because it can lead to undesired side effects and website breakage, takes (at the same time) care and courage. Care to increase the fingerprinting protection in small steps to prevent website breakage. API's guarantee the access of functions and/or data, so Brave taking a different position (denying, randomizing or nullyfing) from all other (chromium) based browsers takes courage.
IMO you can't expect the same results in synthetic tests or proof of concepts from an extension promising to block or randomize API results as you can ask from a browser. Extensions are installed by users, so it s the users responsibility when things brake. When the product (browser) has an option, the developer has responsibility to provide protection with an acceptable level of false positives (website breakage in this case).
So wait, time will see how this all pans out.
IMO you can't expect the same results in synthetic tests or proof of concepts from an extension promising to block or randomize API results as you can ask from a browser. Extensions are installed by users, so it s the users responsibility when things brake. When the product (browser) has an option, the developer has responsibility to provide protection with an acceptable level of false positives (website breakage in this case).
So wait, time will see how this all pans out.
Last edited:
Recently with Brave I get 100% uniqueness on browser leaks, but my signature changes with each browser restart, no site problems so far 

(Edit: I've stuck with Brave for a while, there has been some near misses with Edge but managed to resist)
(Edit: I've stuck with Brave for a while, there has been some near misses with Edge but managed to resist)
Last edited:
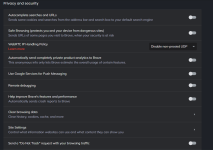
Recent (not new) changes migrated from Nightly and other versions have brought improvements to Brave Shields, which now offer "Standard" or "Strict" options for tracking/ad protection and fingerprinting protection.
And I can report that cookie exclusions has been fixed and now work properly when configured in Settings>Privacy & Security>Site & Shield Settings>Cookies & Site Data> Clear cookies and site data when you quit Brave> On. You must also select Settings>Etc.>Clear Browsing Data>Cookies and site data>Unchecked in both Advanced and Clear on exit options.
Enjoy the built-in goodness, space fans! Stay Brave and stay safe!

And I can report that cookie exclusions has been fixed and now work properly when configured in Settings>Privacy & Security>Site & Shield Settings>Cookies & Site Data> Clear cookies and site data when you quit Brave> On. You must also select Settings>Etc.>Clear Browsing Data>Cookies and site data>Unchecked in both Advanced and Clear on exit options.
Enjoy the built-in goodness, space fans! Stay Brave and stay safe!
Last edited:
Attachments
Last edited:
You may also like...
-
-
Dedoimedo: Brave browser on the iPhone - Very, very interesting
- Started by Gandalf_The_Grey
- Replies: 2
-
Serious Discussion Brave browser passes 100 million monthly active users
- Started by cofer123
- Replies: 13
-
-
New Update Brave for Android now lets you block elements, just like on desktop
- Started by silversurfer
- Replies: 1