- Jul 22, 2014
- 2,525
Usernames, passwords swiped for hours, malware dropped on PCs
Rather than picking off online banking customers one by one, ambitious hackers took control of a Brazilian bank's entire DNS infrastructure to rob punters blind.
The heist, detailed by security engineers at Kaspersky Lab, took place over about five hours on Saturday October 22, 2016, after the miscreants managed to get control of the bank's DNS hosting service using targeted attacks. They managed to transfer all 36 of the bank's domains to phony websites that used free HTTPS certs from Let's Encrypt. These sites masqueraded as the bank's legit online services, tricking marks into believing the malicious servers were the real deal. That allowed the crims to steal customers' usernames and passwords as they were typed into the sites' login boxes.
"All domains, including corporate domains, were in control of the bad guy," said Fabio Assolini, a senior security researcher at Kaspersky, in a blog post. He said the attackers also took over the bank's email servers so that staff couldn't warn customers not to log in.
During the attack, every time a customer logged in, they were handing over their details to the attackers, all of which were sent off to a command and control server in Canada. In addition, the dummy websites dropped malware onto each visitor's computer in the form of .zip'd Java plugin files: clicking on those would start an infection on machines capable of running the malicious code.
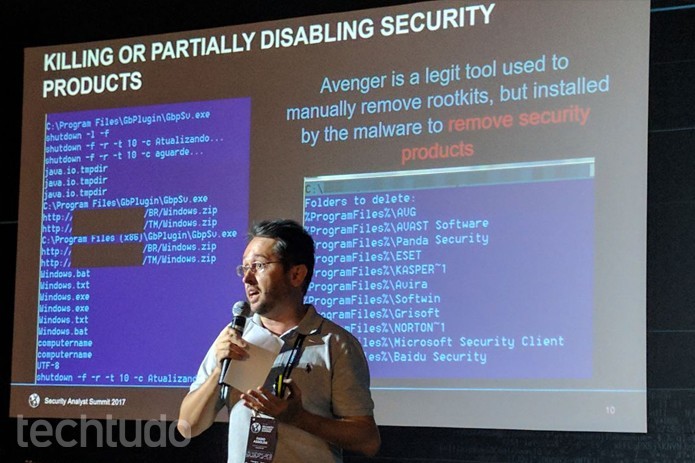
The malware had eight separate modules, covering abilities like credential-stealing for Microsoft Exchange, Thunderbird, and the local address book, updating systems, and a program called Avenger. This software is a legitimate rootkit removal tool that had been modified to shut down security software on any computer that downloaded it.
"The bad guys wanted to use that opportunity to hijack operations of the original bank, but also drop malware with the capacity to steal money from banks of other countries," said Dmitry Bestuzhev, director of Kaspersky Lab's global research and analysis team in Latin America.
The burst of malware did set off alarms elsewhere, and the source was traced back to the bank. Security staff managed to get the original DNS credentials restored to the bank, however the attack shows the importance of managing such things much more tightly.
"Imagine if one employee is phished and the attackers had access to the DNS tables, man that would be very bad," Bestuzhev said. "If DNS was under control of the criminals, you're screwed."
Rather than picking off online banking customers one by one, ambitious hackers took control of a Brazilian bank's entire DNS infrastructure to rob punters blind.
The heist, detailed by security engineers at Kaspersky Lab, took place over about five hours on Saturday October 22, 2016, after the miscreants managed to get control of the bank's DNS hosting service using targeted attacks. They managed to transfer all 36 of the bank's domains to phony websites that used free HTTPS certs from Let's Encrypt. These sites masqueraded as the bank's legit online services, tricking marks into believing the malicious servers were the real deal. That allowed the crims to steal customers' usernames and passwords as they were typed into the sites' login boxes.
"All domains, including corporate domains, were in control of the bad guy," said Fabio Assolini, a senior security researcher at Kaspersky, in a blog post. He said the attackers also took over the bank's email servers so that staff couldn't warn customers not to log in.
During the attack, every time a customer logged in, they were handing over their details to the attackers, all of which were sent off to a command and control server in Canada. In addition, the dummy websites dropped malware onto each visitor's computer in the form of .zip'd Java plugin files: clicking on those would start an infection on machines capable of running the malicious code.
The malware had eight separate modules, covering abilities like credential-stealing for Microsoft Exchange, Thunderbird, and the local address book, updating systems, and a program called Avenger. This software is a legitimate rootkit removal tool that had been modified to shut down security software on any computer that downloaded it.
"The bad guys wanted to use that opportunity to hijack operations of the original bank, but also drop malware with the capacity to steal money from banks of other countries," said Dmitry Bestuzhev, director of Kaspersky Lab's global research and analysis team in Latin America.
The burst of malware did set off alarms elsewhere, and the source was traced back to the bank. Security staff managed to get the original DNS credentials restored to the bank, however the attack shows the importance of managing such things much more tightly.
"Imagine if one employee is phished and the attackers had access to the DNS tables, man that would be very bad," Bestuzhev said. "If DNS was under control of the criminals, you're screwed."