Basic Security Bribon77 2018 security configuration
- Thread starter bribon77
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
P
plat1098
Nice and easy on a machine w/older hardware, right? 
Do you have any problems with Comodo Sandbox and Sandboxie?
Sorry I had not understood, Well in the configuration of @cruelsister you can not use the browser with the Sanbox of Comodo.
Then I just use sandboxie, to navigate
It gave me problems until I unchecked this option.
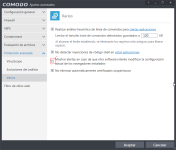
Then I just use sandboxie, to navigate
It gave me problems until I unchecked this option.

Last edited:
I understand. You are using Sandboxie only to run Firefox. Generally, using CF with the active sandbox (like in @cruelsister settings) can sometimes collide with Sandboxie, when both sandboxes want to contain the same process. But, in your case the Firefox processes are whitelisted in CF, so Firefox is going to be contained only by Sandboxie.Sorry I had not understood, Well in the configuration of @cruelsister you can not use the browser with the Sanbox of Comodo.
Then I just use sandboxie, to navigate
It gave me problems until I unchecked this option.
View attachment 177330
Please, check if Sandboxie vendor (Invincea) is on Comodo's Trusted Vendors List. If not, then Comodo can block Sandboxie updates.
CF works well on Windows 7 and it is a kind of default deny protection in CS settings. Having EAM + Comodo (CS settings, default deny) + Sandboxie, you can drop Hard_Configurator (also default deny). It is not necessary to have two default deny protections. Hard_Configurator has some special settings (like blocking SMB), that are not covered by EAM, CF, and Sandboxie, but they would be hardly exploited in Home User environment.
If you will upgrade to Windows 10, then you can consider to drop CF and keep Hard_Configurator.
Hard_Configurator has great compatibility with Windows 10, because it uses Windows built-in policies.
Last edited:
Thanks for the suggestions. Yes, Sandboxie is on the Comodo trust list. there are no problems, I agree that I have a bit of the same when using Comodo and Hard_Configurator, but I like the two Softwars. and at the moment there are no conflicts, if I change to W10 I will take what you recommend, Thanks for bothering to see my Settings. Greetings!
Your welcome.Thanks for the suggestions. Yes, Sandboxie is on the Comodo trust list. there are no problems, I agree that I have a bit of the same when using Comodo and Hard_Configurator, but I like the two Softwars. and at the moment there are no conflicts, if I change to W10 I will take what you recommend, Thanks for bothering to see my Settings. Greetings!
Good config.
You are protected.
Thanks for sharing.
You are protected.
Thanks for sharing.
Have you considered making the move to Windows 10?
Secure config! Thanks for sharing it with us
Secure config! Thanks for sharing it with us
Hello!
It was surprisingly similar to my work, so it was very useful!
Win7 is a red list, how long will you keep using it?
I will last until the last day
I appreciate your sharing! Thank you very much
It was surprisingly similar to my work, so it was very useful!
Win7 is a red list, how long will you keep using it?
I will last until the last day
I appreciate your sharing! Thank you very much
Sorry I had not understood, Well in the configuration of @cruelsister you can not use the browser with the Sanbox of Comodo.
Then I just use sandboxie, to navigate
It gave me problems until I unchecked this option.
View attachment 177330
Hello, bribon77
In the state that cruelister is set up, I use browsers as sandboxes from "run virtual".
Is this the wrong way?
I have no self-confidence.
Hello, bribon77
In the state that cruelister is set up, I use browsers as sandboxes from "run virtual".
Is this the wrong way?
I have no self-confidence.
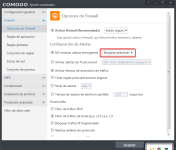
Well, I do not know if I understand you well. But if you use the Cs configuration to block requests in the firewall. It turns out you can not navigate ... that's why I use Sandboxie.
The funny thing is that now, apparently it will be for some update if you let me navigate.
Last edited:
Show- If you are using my settings sandboxing the browsers is not necessary (but you can still do so if you choose).
Understand that in order for an infected webpage to infect your system (either through an exploit kit or through some script), something MUST be downloaded (perhaps without you knowledge) and be able to run locally on your computer. It is this, and any other, action that will be detected by CF and automatically will be shunted into the sandbox, thus affording you protection.
What Bribon stated above is totally correct- if you use my settings AND sandbox the browser the browser will not connect out. But NEVER EVER change the setting that stops sandboxed processes from connecting out (SBIE also has a similar setting), as this setting stops things like Keyloggers, Bankers, and diverse other info stealers from sending any stolen info to the Blackhats (personally I could care less what info a malware file collects as long as it cannot do a God Damned thing with it); also having sandboxed processes precluded from connecting out will stop other malware in their nasty tracks- an example here is the recent GrandCrab ransomware- once the malware sees it cannot connect to its server it just shuts off.
But to make a long post even longer, you really don't have to worry about sandboxing the browser with CF; you can jump through unneeded hops to make it so, but why bother? Life is too precious to waste time...
Understand that in order for an infected webpage to infect your system (either through an exploit kit or through some script), something MUST be downloaded (perhaps without you knowledge) and be able to run locally on your computer. It is this, and any other, action that will be detected by CF and automatically will be shunted into the sandbox, thus affording you protection.
What Bribon stated above is totally correct- if you use my settings AND sandbox the browser the browser will not connect out. But NEVER EVER change the setting that stops sandboxed processes from connecting out (SBIE also has a similar setting), as this setting stops things like Keyloggers, Bankers, and diverse other info stealers from sending any stolen info to the Blackhats (personally I could care less what info a malware file collects as long as it cannot do a God Damned thing with it); also having sandboxed processes precluded from connecting out will stop other malware in their nasty tracks- an example here is the recent GrandCrab ransomware- once the malware sees it cannot connect to its server it just shuts off.
But to make a long post even longer, you really don't have to worry about sandboxing the browser with CF; you can jump through unneeded hops to make it so, but why bother? Life is too precious to waste time...
Thanks @cruelsister. by your configuration a few years ago that I have been using it and I find it excellent .. and I have to say that I am not a newbie in Comodo Firewall, I have it from the beginning I was not even in Spanish.
Show- If you are using my settings sandboxing the browsers is not necessary (but you can still do so if you choose).
Understand that in order for an infected webpage to infect your system (either through an exploit kit or through some script), something MUST be downloaded (perhaps without you knowledge) and be able to run locally on your computer. It is this, and any other, action that will be detected by CF and automatically will be shunted into the sandbox, thus affording you protection.
What Bribon stated above is totally correct- if you use my settings AND sandbox the browser the browser will not connect out. But NEVER EVER change the setting that stops sandboxed processes from connecting out (SBIE also has a similar setting), as this setting stops things like Keyloggers, Bankers, and diverse other info stealers from sending any stolen info to the Blackhats (personally I could care less what info a malware file collects as long as it cannot do a God Damned thing with it); also having sandboxed processes precluded from connecting out will stop other malware in their nasty tracks- an example here is the recent GrandCrab ransomware- once the malware sees it cannot connect to its server it just shuts off.
But to make a long post even longer, you really don't have to worry about sandboxing the browser with CF; you can jump through unneeded hops to make it so, but why bother? Life is too precious to waste time...
Professor, thank you for telling me!
I was an inexperienced person. I only cared about 'infecting' something, I did not assume any concrete attack method such as keylogger at all.
I am very glad that I heard the opinions of you and bribon 77.
Thank you! Someday, I will come back to take class again!
You may also like...
-
-
Security News Cloud Atlas Exploits Office Vulnerabilities to Execute Malicious Code
- Started by Brownie2019
- Replies: 1
-
Security News EDR, Email, and SASE Miss This Entire Class of Browser Attacks
- Started by Brownie2019
- Replies: 1
-
Advanced Plus Security Aries91's Security Configuration 2026
- Started by aries91
- Replies: 14
-
FBI Warns Russian State Hackers Targeting Critical Infrastructure Networking Devices
- Started by Brownie2019
- Replies: 1
