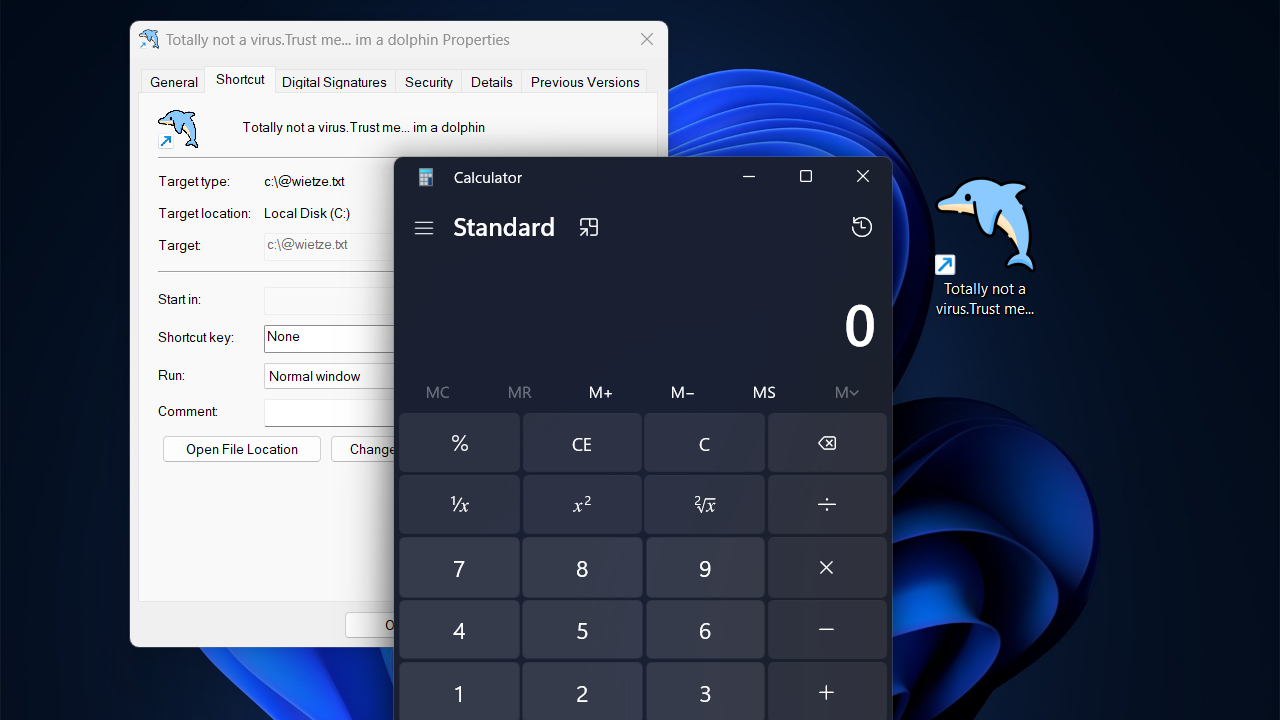
Trust Me, I’m a Shortcut
Windows’ primary mechanism for shortcuts, LNK files, is frequently abused by threat actors for payload delivery and persistence. This blog post introduces several new LNK file flaws that, amongst other things, allow attackers to fully spoof an LNK’s target. It also introduces
lnk-it-up, a tool suite that can generate such deceptive LNK files, as well as detect anomalous ones.
Windows’ primary mechanism for shortcuts, LNK files, is frequently abused by threat actors for payload delivery and persistence. This blog post introduces several new LNK file flaws that, amongst other things, allow attackers to fully spoof an LNK’s target. It also introduces lnk-it-up, a tool...

www.wietzebeukema.nl
www.wietzebeukema.nl

