Well, apparently I got this lovely thing on my desktop today:
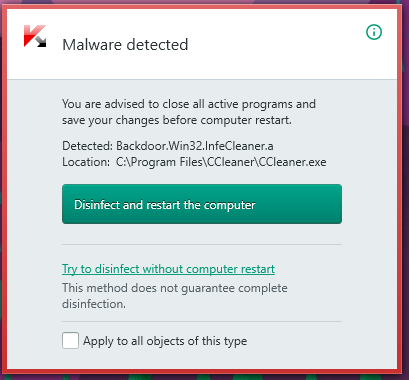
First, I really cannot understand how someone can inject code into an executable without changing its signature and certificate. I really cannot understand. So if anybody can explain me that, I love learning new things and I really would like to know.
Second, I had been experiencing some weird things occurring for the past week or two. My windows store broke, it uninstalled itself. And with it, every software associated to it broke too. Like for example, outlook, that has quite some sensible information in my microsoft university account. Also, from time to time, my timestamp would change to 8:00 something of the actual day we were on, despite it being on auto. I'd have to manually configure it. I'm not sure if it's to do with this, but it's somewhat likely that it has.
If you're experiencing some similar symptoms, hour change or windows store uninstall, you might want to check your ccleaner install date.
Third and even more severe, I don't even know how I got it. My machine had ccleaner installed, but I was 6 months out of my country (since february, 10) and I haven't used ccleaner (and I am sure of it), since at least January of this year.
And further than that, I revoked its rights to auto update, like I do to every other software and I revoked its rights to start up on boot in the day I installed ccleaner (more than half a year ago at least). And I just checked this, it's still disabled to boot with windows.
Well, I am the owner and only user of the machine and I still got the newer version autoinstalled! How?? I have absolutely no idea!

This was my semi-rant post, I am quite upset with all of this, extremely upset with Avast for everything.
If there is someone from the Avast team around, I'd love to hear what you have to say about this.
First, I really cannot understand how someone can inject code into an executable without changing its signature and certificate. I really cannot understand. So if anybody can explain me that, I love learning new things and I really would like to know.
Second, I had been experiencing some weird things occurring for the past week or two. My windows store broke, it uninstalled itself. And with it, every software associated to it broke too. Like for example, outlook, that has quite some sensible information in my microsoft university account. Also, from time to time, my timestamp would change to 8:00 something of the actual day we were on, despite it being on auto. I'd have to manually configure it. I'm not sure if it's to do with this, but it's somewhat likely that it has.
If you're experiencing some similar symptoms, hour change or windows store uninstall, you might want to check your ccleaner install date.
Third and even more severe, I don't even know how I got it. My machine had ccleaner installed, but I was 6 months out of my country (since february, 10) and I haven't used ccleaner (and I am sure of it), since at least January of this year.
And further than that, I revoked its rights to auto update, like I do to every other software and I revoked its rights to start up on boot in the day I installed ccleaner (more than half a year ago at least). And I just checked this, it's still disabled to boot with windows.
Well, I am the owner and only user of the machine and I still got the newer version autoinstalled! How?? I have absolutely no idea!
This was my semi-rant post, I am quite upset with all of this, extremely upset with Avast for everything.
If there is someone from the Avast team around, I'd love to hear what you have to say about this.