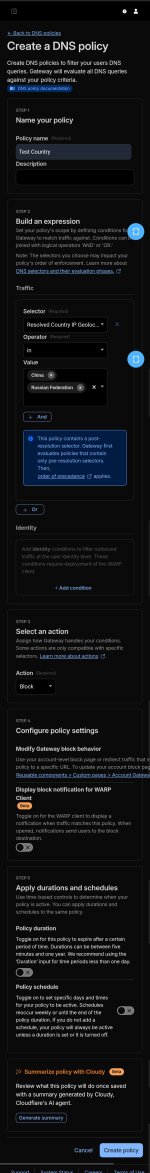
Currently, I am testing Gateway with WARP as an anti-malware firewall.
I leverage the fact that configuring DOH in the web browser bypasses Zero Trust. So, I can block many things via Zero Trust without affecting web browsing.





The full list of TLDs (often abused by phishing or malware):
[.](accountants|ac|ad|am|al|app|asia|bar|bd|beauty|bid|boats|bot|br|buzz|bz|cc|cd|cf|cfd|ci|club|cm|cn|co|country|cx|cyou|cz|date|de|dev|digital|download|ee|email|es|esq|fi|fit|fo|foo|fr|fun|ga|gdn|gq|hair|help|hk|host|hu|icu|id|il|im|in|info|ing|ink|jetzt|jp|ke|kim|la|lat|lc|lgbt|li|life|link|live|locker|loan|loans|lol|ltd|ly|md|me|meme|ml|mobi|mom|monster|mov|mw|mx|net|ng|nl|okinawa|one|online|page|part|ph|pics|pk|pictures|pink|pizza|pocker|pro|pub|pw|qpon|quest|ren|rest|review|ro|ru|sbs|sh|shop|site|space|skin|st|store|stream|su|surf|sx|td|th|tk|tn|to|top|town|tr|trade|tv|tw|vc|vg|vip|wang|wiki|work|world|ws|win|wtf|xin|xxx|xyz|zip|zw)$
Edit1.
It is possible that some geolocation rules for continents can work too.
Edit2.
These policies also involve whitelisting. The links below can be useful:


I leverage the fact that configuring DOH in the web browser bypasses Zero Trust. So, I can block many things via Zero Trust without affecting web browsing.
The full list of TLDs (often abused by phishing or malware):
[.](accountants|ac|ad|am|al|app|asia|bar|bd|beauty|bid|boats|bot|br|buzz|bz|cc|cd|cf|cfd|ci|club|cm|cn|co|country|cx|cyou|cz|date|de|dev|digital|download|ee|email|es|esq|fi|fit|fo|foo|fr|fun|ga|gdn|gq|hair|help|hk|host|hu|icu|id|il|im|in|info|ing|ink|jetzt|jp|ke|kim|la|lat|lc|lgbt|li|life|link|live|locker|loan|loans|lol|ltd|ly|md|me|meme|ml|mobi|mom|monster|mov|mw|mx|net|ng|nl|okinawa|one|online|page|part|ph|pics|pk|pictures|pink|pizza|pocker|pro|pub|pw|qpon|quest|ren|rest|review|ro|ru|sbs|sh|shop|site|space|skin|st|store|stream|su|surf|sx|td|th|tk|tn|to|top|town|tr|trade|tv|tw|vc|vg|vip|wang|wiki|work|world|ws|win|wtf|xin|xxx|xyz|zip|zw)$
Edit1.
It is possible that some geolocation rules for continents can work too.
Edit2.
These policies also involve whitelisting. The links below can be useful:

Connection endpoints for Windows 11 Enterprise - Windows Privacy
Explains what Windows 11 endpoints are used for, how to turn off traffic to them, and the impact. Specific to Windows 11.
learn.microsoft.com

Connection endpoints for Windows 10 Enterprise, version 21H2 - Windows Privacy
Explains what Windows 10 endpoints are used for, how to turn off traffic to them, and the impact. Specific to Windows 10 Enterprise, version 21H2.
learn.microsoft.com
Last edited: