I can take the definition of 'irresponsible' for using CF from super Decopi, I wonder how people who took the burden to test Comodo -among other things- will think about you when you imply they are all dishonest :
While I am still waiting to read a detailed Containment failure from you, I have to note that people clearly less obsessed than you were in te past banned or threads closed for manifest trollism.
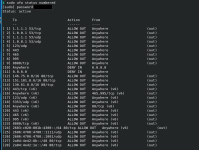
No honest video can hide Comodo Firewall's flaw
While I am still waiting to read a detailed Containment failure from you, I have to note that people clearly less obsessed than you were in te past banned or threads closed for manifest trollism.