cruelsister
Level 43
Thread author
Verified
Honorary Member
Top Poster
Content Creator
Well-known
Forum Veteran
- Content source
- https://youtu.be/clU0AIJZLgI
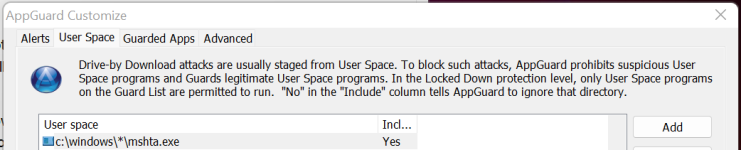
Remote Access Trojans (RATs) malware have increased significantly as of late with a great deal send via Email. Unlike in the past where the malicious file would be an exe or vbs, popular now (and confusing to some) are hta (hypertext markup language) and OneNote files.
Here are examples of both.
Here are examples of both.