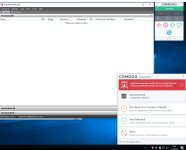
I had the impression that allowing this privilege escalation alert would actually bypass the sandbox. I'm glad to see it doesn't.
Haven't done any focused testing on the container dynamic, except to look at the dynamics of unblocking via "Unblock Applications". At any rate, I think maybe Comodo is really attempting to give the user running W10 and UAC the best of all possible scenarios for an unknown process with unlimited rights. Comodo says, "it can run but it will be running partially limited and in the sandbox." OK, yes this absolutely could be a bug, considering it doesn't work that way in Windows 7. It gets the user choice of restriction. However, this issue does seem serious if it is a bug.
Still, I think maybe I understand why this happens and maybe why it could be intentional. I'm not attempting to say this would be a good decision by the way. At any rate, clicking "Run Unlimited" means to the user, "just let it run." "I know what this is and it's safe." Well, since the app is sandboxed because auto-contain is on, Comodo could be thinking, "user wants unlimited rights for this , but auto-contain is on, and there has to be some restriction, or the sandbox is meaningless." OK, well it wouldn't be meaningless. It still could be run virtually100% without restriction and everything associated recorded in the box. This is dangerous since malware can break Windows and maybe break out of the container. Yet, I could see how it could happen for Comodo to actually decide on "Partially Limited" for that alert with the system set to Auto-Contain and in W10. Just maybe it is Comodo's choice. Again, not saying it's a good choice if so.
That brings questions for me. If this is Comodo's choice, why on Windows 10 and not Windows 7. So already I guess it's back to it could just be a bug. Yet, if it's a bug, then it is definitely Comodo's intention on 7 and 10 for the sandbox to use the user's containment settings even with the privilege elevation alert allowed. Well, I feel like having a discussion with Comodo about this wouldn't be simple. They want you to call it a bug even if it isn't one, because they probably don't want W10 users breathing down their neck about why their security was lowered on purpose. But then will Comodo do anything about it, or just bury it with all the other bugs? In the end, how can we know whether or not this was intended or if it's a bug? Maybe they just went out on a strange limb with Windows 10...especially with UAC on. It does have better native security that W7.
Very complex these issues to deal with with Comodo generally. There is one other question about this. Why does the privilege escalation alert say "Run inside the Container" or "Run Unlimited"? Shouldn't it say "Run by User Settings" or "Run Unlimited". Or maybe "Run Contained Partially Restricted (whatever user's setting is)" or "Run Unlimited". This alert is messed up I think. If the alert were phrased a way I could understand it, I think Comodo would have to change the "Run Unlimited" part to still sandbox but at a lower restriction or whatever they choose. Or else users would knock on their forum asking why it doesn't run when they choose "Run Unlimited".
This is nothing but bothersome to me, not so much a concern really. I feel like Comodo just decided that users in Windows 10 get less strict treatment from allowing "Run Unlimited". Or it's a bug. However, I am interested to know what Comodo does if the original container rule is set to "Run Virtually"->"Partially Limited". I wonder if it would run the same way in W10. Would be interesting to see in W7 too...
One last thing. I happen to have heard that there is pressure on Comodo on this to actually change this alert so that there are multiple options. I got PMed on the Comodo site about it by someone interested in seeing the change. Hopefully it will be improved. I hope so...