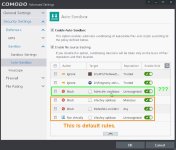
David- at 22 seconds of the video above (and at 22 seconds of the original video) there is a Sandbox setting in the 3rd position. This is a general setting that had to be created as it is not default. At Default Comodo would only have the General settings in positions 4, 5, and 6.
As a comparison look at the 49 second mark of my video (post 29). You can disregard the first 2 (Ignore) as these are specific to SeaMonkey and Java.
So where did this General Rule on your video come from?
Hello cruel sister's first game is infestation and the other is a T-cleaner both legitimate files.With java it has nothing to anis Saemonkey.
Last edited: