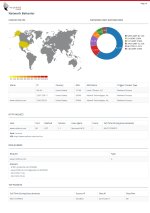
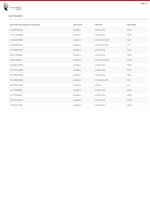
Not really, advanced user will probably never be infected in real lifeThis Valkyrie project is very ambitious and the same time very risky.
And if that happens once, valkyrie probably wont fp that and the backup saves ass anyways
If you take a look at CCAV its great av when comparing the performance and it comes as free product
The malware couldnt even prompt, and woul've been clean after antimalware reboot