- Mar 12, 2024
- 190
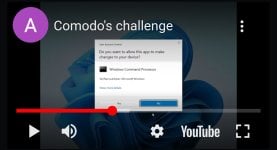
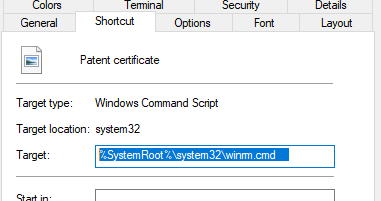
This video demonstrates how an exploit was able to obliterate Comodo Internet Security 2025's AutoContainment, completely rendering all layers of protection of this free security suite, which is well-known for its virtualization technology, useless.
Check this out:
The video has subtitles in 10 languages, including english, so anybody can watch and understand.
Check this out:
The video has subtitles in 10 languages, including english, so anybody can watch and understand.