- Jan 5, 2018
- 163
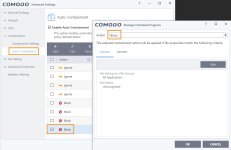
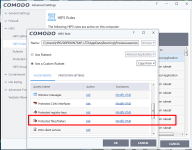
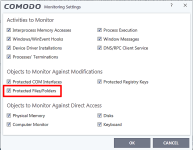
If this is how it is supposed to run or is the only way it CAN run with UAC and partially limited has been implemented in a way that completely protects the user I am fine with that. I just want to know just like all of you. CS has stated that partially limited has been beefed up and is completely secure.
This isn't a witch hunt against Comodo, it is just that those of us who are concerned about security need to know it can be trusted to protect us.
CS also has demonstrated many times with her great videos that CFW with her settings completely protects from infection with UAC on.
It may come down to us not gettings answers and we will just have to trust her. I don't know about you guys but I think that is good enough for me.
What do you guys think?
This isn't a witch hunt against Comodo, it is just that those of us who are concerned about security need to know it can be trusted to protect us.
CS also has demonstrated many times with her great videos that CFW with her settings completely protects from infection with UAC on.
It may come down to us not gettings answers and we will just have to trust her. I don't know about you guys but I think that is good enough for me.
What do you guys think?