@Andy Ful - As I posted earlier, I recently switched from H_C to the new versions of ConfigureDefender and RunbySmartscreen. I have all settings in WD set to max, but I was blocked from doing a couple of things:
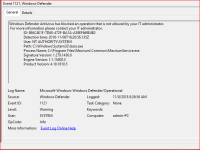
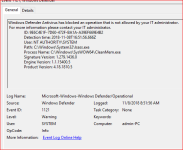
1. Prevented from installing Brave Beta browser. Solved by switching off PUA protection and ASR rule "Block executable files from running unless...". I'm not sure which feature was blocking the action. Please explain, was it the former or the latter?
I'm not sure which feature was blocking the action. Please explain, was it the former or the latter?
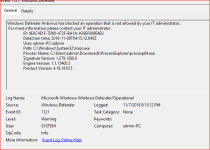
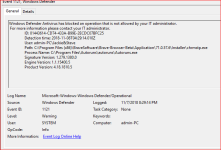
2. I opened Autoruns and was blocked from checking a file via the Virus Total feature. Was this a Windows Defender ASR rule ? or (probably not)maybe RunBySmartrscreen? Or, could it be a registry key, etc.?
As always, thanks in advance as I continue to learn much from you!
1. Prevented from installing Brave Beta browser. Solved by switching off PUA protection and ASR rule "Block executable files from running unless...".
2. I opened Autoruns and was blocked from checking a file via the Virus Total feature. Was this a Windows Defender ASR rule ? or (probably not)maybe RunBySmartrscreen? Or, could it be a registry key, etc.?
As always, thanks in advance as I continue to learn much from you!
Last edited: