Thanks Andy, I find your effort, product and support to be impeccable. I knew it was "them", :devil:.They probably forgot to whitelist the new Edge build and update the ASR module.
You can add an exclusion (file path) to ASR rules from ConfigureDefender. Although this exclusion will be applied for most ASR rules too, the blocked executable is in a not-writable folder, and excluding Edge should not lower ASR protection.
You can also disable this ASR rule temporarily, restart Windows, next update & run Edge Dev, and finally Enable ASR rule again.
Generally, this ASR rule can produce false positives during software updates. That is why it is disabled in ConfigureDefender HIGH Protection level.
ConfigureDefender utility for Windows 10/11
- Thread starter Andy Ful
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Thanks. I did not know the word impeccable. I learned something.Thanks Andy, I find your effort, product and support to be impeccable. I knew it was "them", :devil:.
@Reldel1 @Andy Ful Yes, I checked and found Edge Dev Upda was also blocked here by this rule.
Also, I looked through WSC Protection History and see it keeps the log quite a long time. I found some older blocks which required exclusions so no problem there. I would advise users to check not only ConfigureDefender logs but also Protection History in WSC to check for blocks which won't receive WD notifications. I think I needed 3 ASR exclusions after checking.
And finally, I see that WD scans have all been optimized with this last update. Have others noticed this?
Also, I looked through WSC Protection History and see it keeps the log quite a long time. I found some older blocks which required exclusions so no problem there. I would advise users to check not only ConfigureDefender logs but also Protection History in WSC to check for blocks which won't receive WD notifications. I think I needed 3 ASR exclusions after checking.
And finally, I see that WD scans have all been optimized with this last update. Have others noticed this?
Why am I seeing this in my logs? Running on high protection, and as far as I remember I did nothing to WD on the date shown. Thanks.
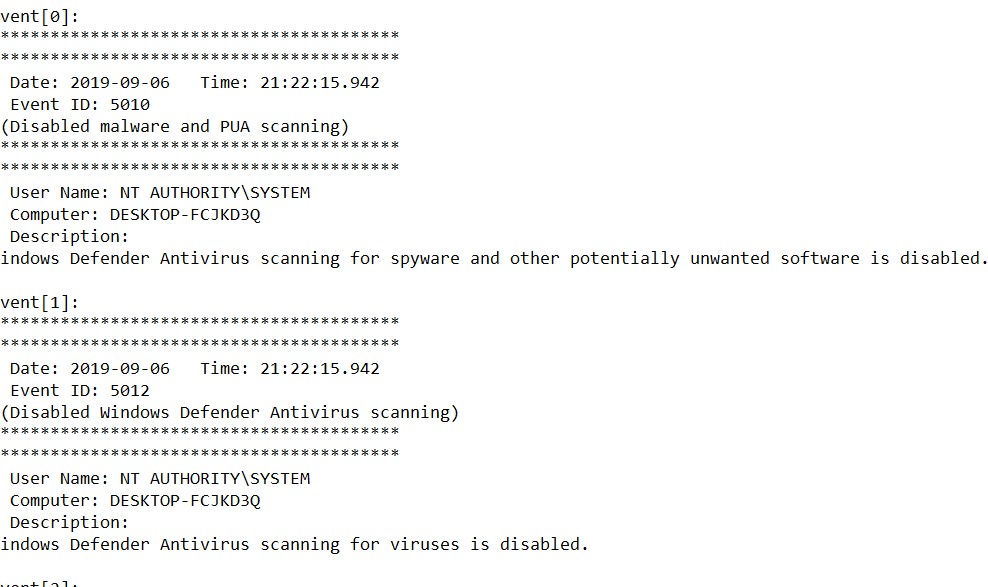
Why am I seeing this in my logs? Running on high protection, and as far as I remember I did nothing to WD on the date shown. Thanks.View attachment 224341
I wondered the same. I was away for 2 days and came back to find it disabled. Maybe just Windows being Windows around an update? That's what I figured.
It appears Microsoft found their problem and have provided and update, below is from their Edge Insider notes:Thanks. I did not know the word impeccable. I learned something.
Hi everyone, just a quick note to say that we deployed a new build 78.0.268.3 to the Dev channel today for Windows only. This corrects an issue with our digital signature that prevented Microsoft Edge from working on Windows 10 S and caused some people to see an "unverified publisher" or similar message. There are no other changes in this update.
This corrects an issue with our digital signature that prevented Microsoft Edge from working on Windows 10 S and caused some people to see an "unverified publisher" or similar message. There are no other changes in this update.
Leave it to M$ to screw up its own apps' performance on its own OS! LOL
Something disabled WD.Why am I seeing this in my logs? Running on high protection, and as far as I remember I did nothing to WD on the date shown. Thanks.
...
There are a few events Id=5010 on my computer, but they are correlated with moments when I disabled WD via Defender Control tool (confirmed a few minutes ago).
I think that it can be also related to updating WD engines (not signatures).
It would be interesting to know how many ConfigureDefender users have this event in the Log.
No 5010 events in my log.Something disabled WD.
There are a few events Id=5010 on my computer, but they are correlated with moments when I disabled WD via Defender Control tool (confirmed a few minutes ago).
I think that it can be also related to updating WD engines (not signatures).
It would be interesting to know how many ConfigureDefender users have this event in the Log.
I just got an engine update when I switched back to Defender. I will check the event log later when I’m at my computer to see if it’s in there.Something disabled WD.
There are a few events Id=5010 on my computer, but they are correlated with moments when I disabled WD via Defender Control tool (confirmed a few minutes ago).
I think that it can be also related to updating WD engines (not signatures).
It would be interesting to know how many ConfigureDefender users have this event in the Log.
The new Edge Development version, Version 78.0.268.1 (Official build) dev (64-bit), failed the update re-start process because the Configure Defender exploit guard setting "Block executable files from running unless they meet a prevalence, age or trusted list criteria" prevented the update restart. For whatever reason the "ON" setting had to be disabled in Configure Defender in order to complete the update AND then to allow Version 78.0.268.1 desktop link to open Development Edge. I am now running with the "Block executable files" setting disabled and Edge updates and opens correctly.
something was amiss with the msedge update to v78, give me BSOD :emoji_grimacing:
It would be interesting to know how many ConfigureDefender users have this event in the Log.
5007 and 5001 yesterday.
ConfigureDefender and the fileless malware.
I would like to share some information about WD ASR rules in the context of fileless attacks. Fileless attack (common definition) is an attack during which no portable executable (PE) file is written to and executed from disk.
The below ASR rules are strictly related to the protection of MS software:

As can be seen from the above points, WD ASR rules do not prevent the attacks performed via Python scripts or Java files ( .jar files), which are sometimes used by malc0ders too. But, such attacks require installing Python or Java engines.
I would like to share some information about WD ASR rules in the context of fileless attacks. Fileless attack (common definition) is an attack during which no portable executable (PE) file is written to and executed from disk.
The below ASR rules are strictly related to the protection of MS software:
- Block executable content from email client and webmail (Outlook or Outlook.com).
It blocks the following file types: EXE, SCR, DLL, PS, JS, VBS, etc. when these files are launched from Outlook or Outlook.com (and probably some other popular webmail providers). - Block Office applications from creating child processes - blocks also the execution of script engines and other LOLBins by Office exploits.
- Block Office applications from injecting into other processes - prevents the Office exploits to inject the malicious code into other processes.
- Block Win32 imports from Macro code in Office - restricts VBA macros when they try to use Win32 API calls.
- Block only Office communication applications from creating child processes - prevents Outlook exploits from creating child processes, also script engines and other LOLBins.
- Use advanced protection against ransomware - includes also remediation of PowerShell trojan-downloaders.
- Impede JavaScript and VBScript to launch executables - blocks common JavaScript and VBScript trojan-downloaders.
- Block credential stealing from the Windows local security authority subsystem (lsass.exe) - protects passwords and credentials.
- Block process creations originating from PSExec and WMI commands - prevents spying, blocks wmic.exe, prevents remote code execution.
- Block Adobe Reader from creating child processes - blocks also the execution of script engines, Office applications, and other LOLBins by Adobe Reader exploits.
- Block execution of potentially obfuscated scripts - blocks some obfuscated JS, VBS, PS, VBA code.
- Block persistence through WMI event subscription - prevents the threats that abuse WMI to persist and stay hidden in WMI repository.

Use attack surface reduction rules to prevent malware infection - Microsoft Defender for Endpoint
Attack surface reduction rules can help prevent exploits from using apps and scripts to infect devices with malware.
docs.microsoft.com
As can be seen from the above points, WD ASR rules do not prevent the attacks performed via Python scripts or Java files ( .jar files), which are sometimes used by malc0ders too. But, such attacks require installing Python or Java engines.
Last edited:
@simmerskool - you may find the latest ConfigureDefender download here, along with other @Andy Ful tools: Hard_Configurator — Download Scroll down to CD, etc. I suggest to upgrade to W10 before too long. 
@simmerskool - you may find the latest ConfigureDefender download here, along with other @Andy Ful tools: Hard_Configurator — Download Scroll down to CD, etc. I suggest to upgrade to W10 before too long.
thanks!!
@Andy Ful can you add 'pause scan' option?
It may not be possible due to Windows Defender itself.
It may not be possible due to Windows Defender itself.
I didn't try it yet but you can enable with gpedit.msc.
Do you mean the option that prevents users to 'pause scan'?@Andy Ful can you add 'pause scan' option?
ConfigureDefender can hide WSC to prevent children or newbies to pause scans or change WD settings.
You may also like...
-
Windows 11 Defender Tuning: Safer Settings That Don’t Hurt Performance
- Started by Bot
- Replies: 1
-
Hot Take Microsoft finally admits almost all major Windows 11 core features are broken
- Started by Brahman
- Replies: 18
-
-
New Update Windows 11 Patch Tuesday January 2026 (KB5074109, KB5073455)
- Started by silversurfer
- Replies: 18
-
AExtending Bluetooth® LE Audio on Windows 11 with shared audio (preview)
- Started by Amanda Langowski
- Replies: 0