I tried it again at Defender high settings, and this time, no problem. Either the file was already whitelisted, or the scanning is behaving inconsistently, or, like you said, the system was just busy with something else.I have no idea. I also configured 'Defender high settings' and even installed OSArmour (default). Everything is normal. But except OSArmor, I do not use another non-Microsoft security.
.
Edit.
Please, check it after some minutes, because Windows can slow down when updating Windows Store, performing some scheduled tasks, etc.
ConfigureDefender utility for Windows 10/11
- Thread starter Andy Ful
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
I tested Defender High settings + OSArmor default settings. No issues. When I unticked "Block execution of .vbs scripts" while keeping ticked the option "Block any process executed from wscript.exe", then Defender ASR protection blocked VBScript trojan downloaders before OSArmor.Do you see any possible conflicts between Defender high settings and OSArmor? Would you recommend such a setup?
Both Defender ASR nad OSArmor default, can be bypassed to download and execute the payload via some PowerShell scripts.
And if you completely block powershell, in OSA?Both Defender ASR nad OSArmor default, can be bypassed to download and execute the payload via some PowerShell scripts.
PowerShell cannot be completely blocked in OSA. But, you can block powershell.exe. This will improve the protection (still can be bypassed by simply copying/renaming powershell.exe). But if you do not block cmd.exe, then VBS scripts can be run with spoofed extensions.And if you completely block powershell, in OSA?
That's a good trick to know about. Thanks.But if you do not block cmd.exe, then VBS scripts can be run with spoofed extensions.
I found Controlled Folder Access somewhat irritating, when during installation of programs, you get an error, because program shortcut cannot be created on the desktop. But there is a very simple solution for that. The shortcut is also created at the Start Menu. So you can simply open the Start Menu and use a mouse to drag & drop the shortcut to the Desktop (if you need it there).
The above is much easier than navigating to the program executable in Explorer and creating the shortcut manually.
The above is much easier than navigating to the program executable in Explorer and creating the shortcut manually.
...just to know that "Close" button is not working, close on X is OK 
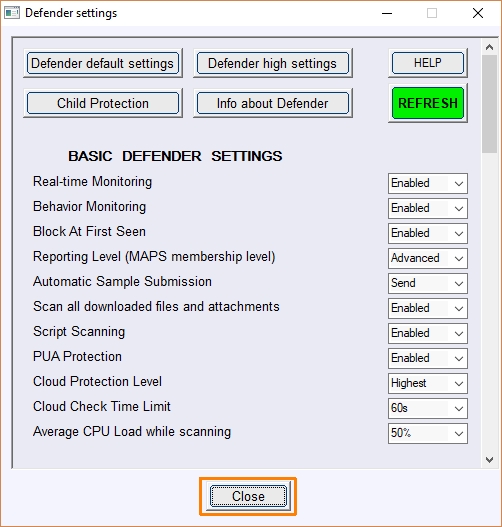
BTW:
Does PC need to be restarted to all these tweak to work or is it OK without that?
BTW:
Does PC need to be restarted to all these tweak to work or is it OK without that?
It works, but sometimes you must click it more than one time.
Most settings do not require to reboot. I noticed that 'Cloud Protection Level' and 'Hide Security Center' works well only after rebooting....just to know that "Close" button is not working, close on X is OK
View attachment 178413
BTW:
Does PC need to be restarted to all these tweak to work or is it OK without that?
The reg tweak used in Hard_Configurator worked in previous Windows versions, but there are some indicators that it may not work in the new versions. It is hard to test this, because in the new Windows 10 versions, all PUPs that I tested were stopped by Defender with disabled PUP protection. I can recommend using ConfigureDefender PUP protection setting, and I plan to remove PUP protection option from Hard_Configurator in the next version with integrated ConfigureDefender feature.@Andy Ful ,
I just made some tests using CD. In Hardconfigurator I already enabled WD PUP protection. But if I open CD it shows PUP protection is disabled. Any idea why?
- Apr 28, 2015
- 9,400
- 1
- 84,828
- 8,389
It is a safe file.
It runs scripts that modify system settings. I am surprised that more AV engines don't flag it for that reason.
Any advanced security software without a digital signature is bound to get false positives like this.
It runs scripts that modify system settings. I am surprised that more AV engines don't flag it for that reason.
Any advanced security software without a digital signature is bound to get false positives like this.
Pretty good little application that lets you control all those WD settings. Well done.
For me it was also removing it completely and not moving to quarantine. Just make exceptions before you open word and it will be fine after that. I think it's because of the extension or something.Works great.
This comment is about Office exploit protection in general, not about ConfigureDefender:
I have a certain Word add-on, "SaveReminder Ver 2.1.dotm", it lives in the Word startup folder in Appdata/Roaming/Microsoft. After enabling Office exploit protection, I got an error message when opening Word, saying that the file was blocked. Okay fine, but when I open the exceptions tab to fix the problem, I discover that the add-on file is gone entirely. It is not even in WD quarantine. Cute, huh?
Question about: "Block office applications from creating child processes"--enabled.
Will this also prevent process hollowing, which involves the creation of a child process?
Another question: "Block... from injecting into other processes"--enabled.
How does this compare to the injection protection of Excubits Memprotect?
Will this also prevent process hollowing, which involves the creation of a child process?
Another question: "Block... from injecting into other processes"--enabled.
How does this compare to the injection protection of Excubits Memprotect?
Those are the questions for @Opcode. Generally, ASR should prevent both techniques, but there can be some bugs allowing the attacker to bypass ASR. From articles/tests I read (and made by myself), if you turn on all ASR mitigations, then you will get the solid protection.Question about: "Block office applications from creating child processes"--enabled.
Will this also prevent process hollowing, which involves the creation of a child process?
Another question: "Block... from injecting into other processes"--enabled.
How does this compare to the injection protection of Excubits Memprotect?
D
Deleted member 65228
Theoretically, yes.Will this also prevent process hollowing, which involves the creation of a child process?
To cut it really short, Excubits MemProtect doesn't actually intercept the Remote Code Execution (RCE) operation. It prevents process/thread handles being dished out with specific access rights for those processes which are protected via ObRegisterCallbacks, one of the self-defense techniques which is common for an AV product to use. This in turn has an effect that makes you *think* it can intercept RCE operations since it cuts off the legs so the attackers using traditional RCE techniques never make it to the RCE operation deployment. It will not behave like an anti-exploit product regarding memory access/modification interception, like EMET/HitmanPro.Alert/Malwarebytes Anti-Exploit.How does this compare to the injection protection of Excubits Memprotect?
However, ObRegisterCallbacks is far from perfect on its own and thus this explains why it is usually only *one* of the self-defense techniques used in security solution packages from resourceful vendors. Don't forget about Extra Window Memory (EWM) injection with GUI programs as well.
I would presume that the injection prevention feature you're referring to in the quoted post will actually prevent the RCE operation; there are ways you could try to test/check it through checking if you can still open a handle to a process with specific access rights or through reverse engineering.
Thanks.Theoretically, yes.
To cut it really short, Excubits MemProtect doesn't actually intercept the Remote Code Execution (RCE) operation. It prevents process/thread handles being dished out with specific access rights for those processes which are protected via ObRegisterCallbacks, one of the self-defense techniques which is common for an AV product to use. This in turn has an effect that makes you *think* it can intercept RCE operations since it cuts off the legs so the attackers using traditional RCE techniques never make it to the RCE operation deployment. It will not behave like an anti-exploit product regarding memory access/modification interception, like EMET/HitmanPro.Alert/Malwarebytes Anti-Exploit.
However, ObRegisterCallbacks is far from perfect on its own and thus this explains why it is usually only *one* of the self-defense techniques used in security solution packages from resourceful vendors. Don't forget about Extra Window Memory (EWM) injection with GUI programs as well.
I would presume that the injection prevention feature you're referring to in the quoted post will actually prevent the RCE operation; there are ways you could try to test/check it through checking if you can still open a handle to a process with specific access rights or through reverse engineering.
There are various types of memory access. Memprotect is said to block them all.
What about this ASR mitigation?
In the next integrated version, I think you mentioned somewhere that it will include Exploit protection settings for some common exploitable apps. Could you add 7-Zip to that list?The reg tweak used in Hard_Configurator worked in previous Windows versions, but there are some indicators that it may not work in the new versions. It is hard to test this, because in the new Windows 10 versions, all PUPs that I tested were stopped by Defender with disabled PUP protection. I can recommend using ConfigureDefender PUP protection setting, and I plan to remove PUP protection option from Hard_Configurator in the next version with integrated ConfigureDefender feature.
You may also like...
-
Windows 11 Defender Tuning: Safer Settings That Don’t Hurt Performance
- Started by Bot
- Replies: 1
-
Hot Take Microsoft finally admits almost all major Windows 11 core features are broken
- Started by Brahman
- Replies: 18
-
-
New Update Windows 11 Patch Tuesday January 2026 (KB5074109, KB5073455)
- Started by silversurfer
- Replies: 18
-
AExtending Bluetooth® LE Audio on Windows 11 with shared audio (preview)
- Started by Amanda Langowski
- Replies: 0