Is the installer still blocked
No.
BTW: I always keep the executable in the Windows folder.
Last edited:
Is the installer still blocked
I found out what was the issue. As I suspected it was related to WD whitelisting signatures. The portable CD is a simple NSIS installer which contains 3 files (2 signed executables: for Windows 64-bit and 32-bit + unsigned uninstaller). I send first the signed executables for whitelisting and after a day I noticed that uninstaller also has to be whitelisted. At the time you ran the application, WD did not have the whitelisting signatures for the uninstaller. So, when you ran the portable ConfigureDefender everything was OK, until you closed it. The uninstaller was blocked by ASR due to low prevalence, so you have two signed executables somewhere in "C:\Windows\Temp" folder - they were not cleaned by the uninstaller.I am getting apparently harmless blocks of CD by ASR rule "Block executables unless they ..."
View attachment 238721
... but I also got a separate, one-time system notification that NSIS was blocked or failed to install.
Yes. That is true. Although, some of ASR rules in MAX settings can cause issues. For example, the factory firmware on some laptops uses WMI. Also, when the firmware wants to update, this can be prevented for some days by ASR due to the low prevalence....
So really wondering why/what is the caution in using the MAX setting, because people running plain Windows with free or microsoft office, don't install programs, so the MAX setting works extremely well.
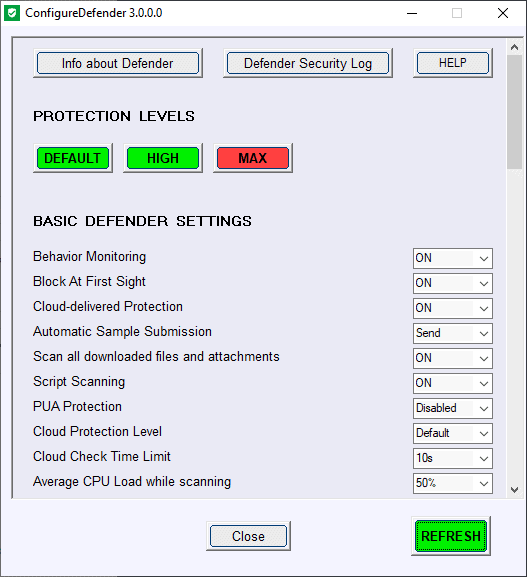
All settings can be customized from within the interface. It is easy enough to turn features such as Behavior Monitoring, PUA Protection or Controlled Folder Access on or off using the program. Values of some settings can be modified, e.g. to change the cloud check time limit or average CPU load while scanning.High
Enhanced configuration which enables Network Protection and most of Exploit Guard (ASR) features. Three Exploit Guard features and Controlled Folder Access ransomware protection are disabled to avoid false positives. This is the recommended configuration which is appropriate for most users and provides significantly increased security.
Max
This is the most secure protection level which enables all advanced Windows Defender features and hides Windows Security Center. Configuration changes can be made only with the ConfigureDefender user interface. The "Max" settings are intended to protect children and casual users but can also be used (with some modifications) to maximize the protection. This protection level usually generates more false positives compared to the "High" settings may require more user knowledge or skill.

 malwaretips.com
malwaretips.com
No need. I have already set up everything via GPE.
You probably used one of the old CD versions, which was first whitelisted by Microsoft, and after 4 months flagged as malicious, after changing the malware criteria by Microsoft. The reason for this was an option that allowed the user to disable real-time protection. This story is well documented on the ConfigureDefender thread.
At that time, I downloaded the latest version from GitHub. But, the interesting part; alert was shown few days after changing settings. When detection occured, I didn't even have ConfigureDefender on my PC.You probably used one of the old CD versions, which was first whitelisted by Microsoft, and after 4 months flagged as malicious, after changing the malware criteria by Microsoft. The reason for this was an option that allowed the user to disable real-time protection. This story is well documented on the ConfigureDefender thread.
Here is my ironic comment to this detection:
https://malwaretips.com/threads/configuredefender-utility-for-windows-10.79039/post-767631
At that time, I downloaded the latest version from GitHub. But, the interesting part; alert was shown few days after changing settings. When detection occured, I didn't even have ConfigureDefender on my PC.

This will require testing by others. But, WD Network Protection is by design independent of the application which connects to the Internet. It will work for web browsers, Internet Downloaders, script engines, etc. So, this issue (if it will be confirmed on other machines) would be probably related to the web browser or to the way it interacts with WD Network Protection. Anyway, I would not be surprised if protecting the network could slow down the connection a little.Did anyone notice high ping when Network Protection is enabled (HIGH settings)? I ran a speed test in Firefox and the first test I got normal ping (~7ms):
View attachment 239348
I ran several speeds tests immediately afterwards and I got really high ping with slightly lower up/down speeds:
View attachment 239349
I had to wait for 1-2 min for ping to go down to normal. I didn't run into this issue with Edge though. I'm not sure if it's WD or Firefox issue. I disabled Network Protection for now.
Thanks Andy. Is there a way to allow single app to bypass WD Network Protection?This will require testing by others. But, WD Network Protection is by design independent of the application which connects to the Internet. It will work for web browsers, Internet Downloaders, script engines, etc. So, this issue (if it will be confirmed on other machines) would be probably related to the web browser or to the way it interacts with WD Network Protection. Anyway, I would not be surprised if protecting the network could slow down the connection a little.
I do not think that it could be possible. Anyway, this would be also not safe.Thanks Andy. Is there a way to allow single app to bypass WD Network Protection?

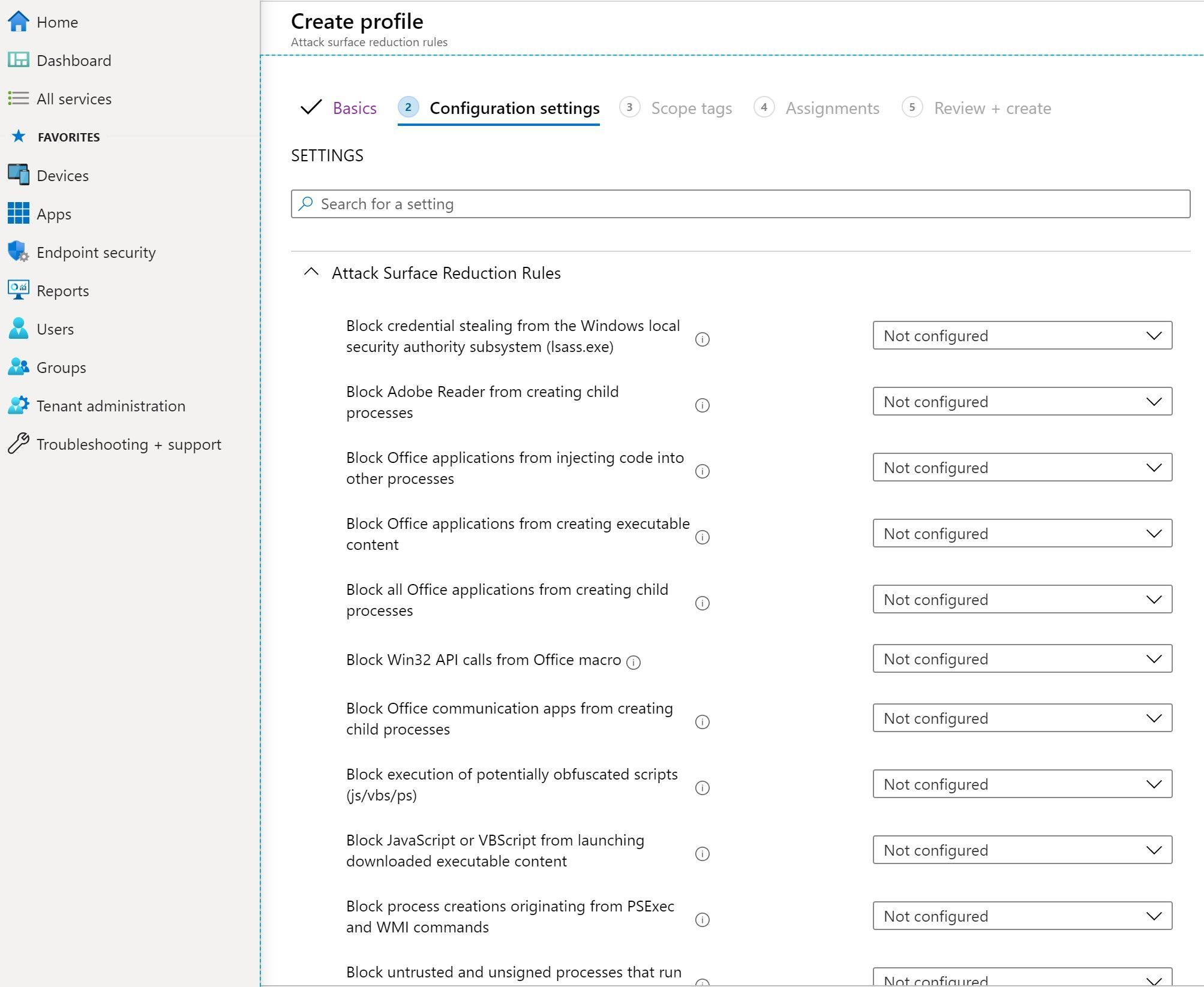
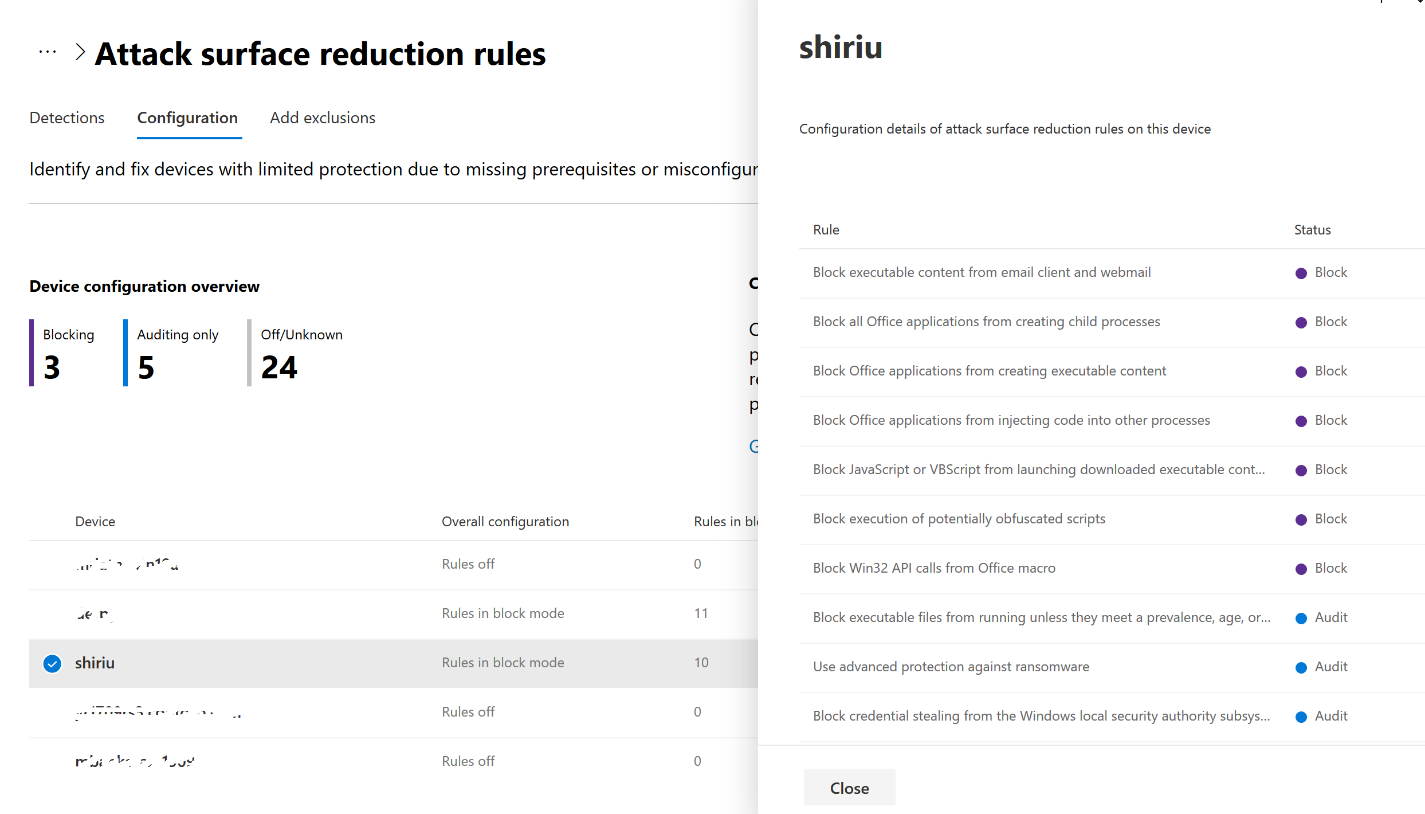
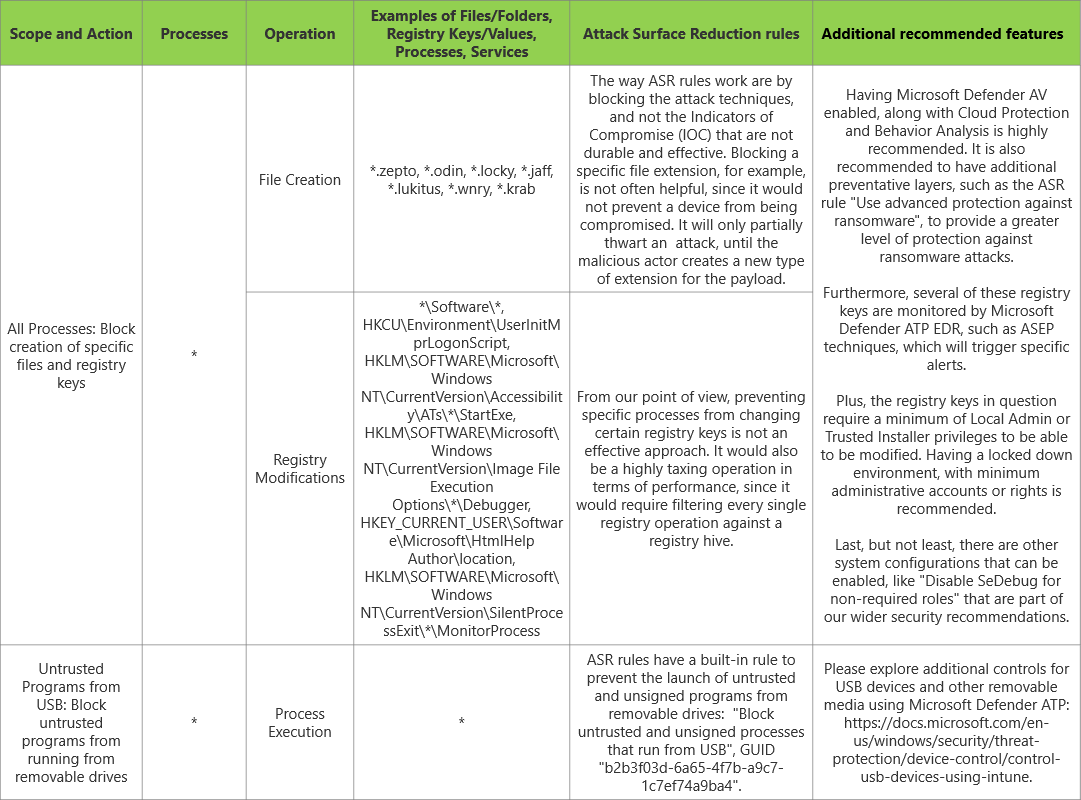
Yes I read them all. Unfortunately, I knew all of it already from Microsoft documentation.Here's a nice overview of ASR functionality and the principles behind them.

Demystifying attack surface reduction rules - Part 1 | Microsoft Community Hub
An A to Z guide, to help you understand what are Attack Surface Reduction (ASR) rules and how to successfully adopt it.techcommunity.microsoft.com

Demystifying attack surface reduction rules - Part 2 | Microsoft Community Hub
An A to Z guide, to help you understand what are Attack Surface Reduction (ASR) rules and how to successfully adopt it.techcommunity.microsoft.com

Demystifying attack surface reduction rules - Part 3 | Microsoft Community Hub
An A to Z guide, to help you understand what are Attack Surface Reduction (ASR) rules and how to successfully adopt it.techcommunity.microsoft.com

Demystifying attack surface reduction rules - Part 4 | Microsoft Community Hub
An A to Z guide, to help you understand what are Attack Surface Reduction (ASR) rules and how to successfully adopt it.techcommunity.microsoft.com
When I used WD, Network Protection made the dslreports bufferbloat test show absurdly high latency spikesDid anyone notice high ping when Network Protection is enabled (HIGH settings)? I ran a speed test in Firefox and the first test I got normal ping (~7ms):
View attachment 239348
I ran several speeds tests immediately afterwards and I got really high ping with slightly lower up/down speeds:
View attachment 239349
I had to wait for 1-2 min for ping to go down to normal. I didn't run into this issue with Edge though. I'm not sure if it's WD or Firefox issue. I disabled Network Protection for now.