I'm add Lolbins and recommended H_C. And turn on logging events. It's enough?
ConfigureDefender utility for Windows 10/11
- Thread starter Andy Ful
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Yes.I'm add Lolbins and recommended H_C. And turn on logging events. It's enough?
@Andy Ful without me reading all 91 pages of posts... (I normally use danb's DefenderUI but on this VM I only use MSD and your tools), and my Defender systray icon has a yellow flag  and it says Tamper Protection is Off. I assume I ran ConfigureDefender at default (or max or recommended) so should Tamper protection be off. should I just turn it ON from system Windows Security, or open ConfigureDefender and run it again? ie, is it normal for Tamper to be off after running CD?
and it says Tamper Protection is Off. I assume I ran ConfigureDefender at default (or max or recommended) so should Tamper protection be off. should I just turn it ON from system Windows Security, or open ConfigureDefender and run it again? ie, is it normal for Tamper to be off after running CD?
I assume I ran ConfigureDefender at default (or max or recommended) so should Tamper protection be off. should I just turn it ON from system Windows Security, or open ConfigureDefender and run it again? ie, is it normal for Tamper to be off after running CD?
ConfigureDefender does not change Tamper Protection. If I recall correctly DefenderUI does.
You should turn ON Tamper Protection.
ThanksConfigureDefender does not change Tamper Protection. If I recall correctly DefenderUI does.
You should turn ON Tamper Protection.
It looks like ConfigureDefender can also be downloaded from the WinGet repository:

 winstall.app
winstall.app
WinGet installs ConfigureDefender into the directory:
%LocalAppData%\Microsoft\WinGet\Packages\AndyFul.ConfigureDefender_Microsoft.Winget.Source_8wekyb3d8bbwe
WinGet adds this directory to the PATH environment variable, so ConfigureDefender can be executed from anywhere by invoking the configuredefender variable (similarly to system executables).

Install ConfigureDefender with winget - winstall
Utility for configuring Windows 10 built-in Defender antivirus settings.
WinGet installs ConfigureDefender into the directory:
%LocalAppData%\Microsoft\WinGet\Packages\AndyFul.ConfigureDefender_Microsoft.Winget.Source_8wekyb3d8bbwe
WinGet adds this directory to the PATH environment variable, so ConfigureDefender can be executed from anywhere by invoking the configuredefender variable (similarly to system executables).
Does the Cloud Protection Level or "Block executables..." use the ISG or SmartScreen backend?
Does the Cloud Protection Level or "Block executables..." use the ISG or SmartScreen backend?
It is possible that the "Block executables..." ASR rule somehow depends on "ISG without a SmartScreen backend (files with no MOTW)". But this rule also depends on the file age. If the file is known in the Microsoft cloud for more than 24 hours, it will be allowed even if ISG still blocks it.
There is no direct connection to SmartScreen. Both Cloud Protection Level and "Block executables..." ASR rule can block executables allowed by SmartScreen. For example, the ASR rule blocked my digitally signed applications a few times (allowed by SmartScreen).
Edit.
The ASR rule "Block executables ..." does not block MSI files and DLLs loaded by EXEs (cannot prevent DLL hijacking), but SAC (and WDAC ISG) can.
When protecting happy clickers with an enabled rule "Block executables ...", enabling also SAC makes sense.
Last edited:
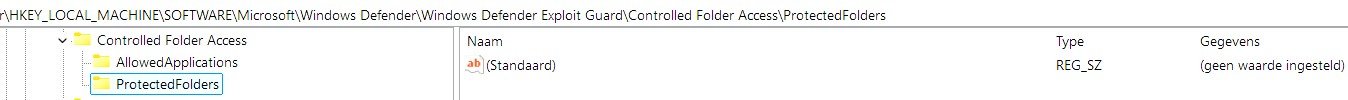
When I click on the button Folders in the section Controlled Folder, the popup window CFA Folders doesn't show the default entries (Protected Folders).
This corresponds to an empty folder in the registry. Is this normal behavior? Windows security dashboard shows the default protected folders (from which source?). I never added folders to it.
This corresponds to an empty folder in the registry. Is this normal behavior? Windows security dashboard shows the default protected folders (from which source?). I never added folders to it.
Attachments
When I click on the button Folders in the section Controlled Folder, the popup window CFA Folders doesn't show the default entries (Protected Folders).
This corresponds to an empty folder in the registry. Is this normal behavior?
Yes, this normal (intended) behavior.
The default CFA protection cannot be decreased - the default folders cannot be removed from CFA (they are skipped in ConfigureDefender).
@Andy Ful i couldn't find anything related to "Block use of copied or impersonated system tools" in configure defender manual. Any tips? Ty!
@Andy Ful i couldn't find anything related to "Block use of copied or impersonated system tools" in configure defender manual. Any tips? Ty!
Block use of copied or impersonated system toolsThis rule blocks the use of executable files that are identified as copies of Windows system tools. These files are either duplicates or impostors of the original system tools. Some malicious programs might try to copy or impersonate Windows system tools to avoid detection or gain privileges. Allowing such executable files can lead to potential attacks. This rule prevents propagation and execution of such duplicates and impostors of the system tools on Windows machines.
@Andy Ful i couldn't find anything related to "Block use of copied or impersonated system tools" in configure defender manual. Any tips? Ty!
I can only add that this ASR rule will block:
- any executable in UserSpace with a file name of a system tool,
- any system tool copied from the original location and renamed (can recognize the internal name).
Fortunately, the blocked file path can be excluded via ASR exclusions.
Last edited:
This specific rule blocked graphics driver after manual install, so I never used it again.I can only add that this ASR rule will block:
Edit.
- any executable in UserSpace with a file name of a system tool,
- any system tool copied from the original location and renamed (can recognize the internal name).
Fortunately, the blocked file can be excluded via ASR exclusions.
My top rules are those cloud-dependent.
This specific rule blocked graphics driver after manual install, so I never used it again.
My top rules are those cloud-dependent.
It was not this rule, but probably "Block abuse of exploited vulnerable signed drivers". If you need to install the vulnerable driver for some important reason, just temporarily set the rule to Audit (Windows restart may be required) and install the driver .
Post edited.
Last edited:
It was "Block use of copied or impersonated system tools", not "Block abuse of exploited vulnerable signed drivers".It was not this rule, but probably "Block abuse of exploited vulnerable signed drivers". If you need to install the vulnerable driver for some important reason, just temporarily set the rule to Audit and install the driver.
The driver was Intel HD graphics one downloaded from the official support page of hp.
Seems MD considered the driver files impersonating the one installed earlier through Windows update.
It was "Block use of copied or impersonated system tools", not "Block abuse of exploited vulnerable signed drivers".
The driver was Intel HD graphics one downloaded from the official support page of hp.
Seems MD considered the driver files impersonating the one installed earlier through Windows update.
Interesting. Do you have access to this driver? I would like to test why it triggered this rule.
I got from this website: https://support.hp.com/us-en/drivers/hp-compaq-pro-6300-small-form-factor-pc/5232881Interesting. Do you have access to this driver? I would like to test why it triggered this rule.
Intel Graphic Driver Win7 64b: sp78306.exe
I got from this website: https://support.hp.com/us-en/drivers/hp-compaq-pro-6300-small-form-factor-pc/5232881
Intel Graphic Driver Win7 64b: sp78306.exe
Are you sure? This driver is for Windows 7. Did you try to install it on Windows 10+?
Last edited:
Intel Graphic Driver Win7 64b: sp78306.exe
Tried to install this driver on my machine (Windows 11 x64) with both ASR rules enabled. I expected that one of the ASR rules would be triggered even if the installation has no chance to be successful (different Windows version and different hardware).
The installation finally failed after a few seconds (as expected) with error:
No blocks from ASR rules.
Anyway, different behavior was possible on the HP computer.
Last edited:
You may also like...
-
Windows 11 Defender Tuning: Safer Settings That Don’t Hurt Performance
- Started by Bot
- Replies: 1
-
Hot Take Microsoft finally admits almost all major Windows 11 core features are broken
- Started by Brahman
- Replies: 18
-
-
New Update Windows 11 Patch Tuesday January 2026 (KB5074109, KB5073455)
- Started by silversurfer
- Replies: 18
-
AExtending Bluetooth® LE Audio on Windows 11 with shared audio (preview)
- Started by Amanda Langowski
- Replies: 0