Beyond Stolen CPU Cycles, Miners Pose Enterprise Security Risks

Criminals who want to mine for cryptocurrency such as monero can skip buying dedicated hardware (pictured) and instead sneak mining malware onto PCs and servers.
In about a day, a consumer PC can generate about a 25 cents worth of monero, a privacy-focused cryptocurrency that has become one of bitcoin's more successful cousins.
See Also: How to Scale Your Vendor Risk Management Program
With those trickling returns, it seems hardly worth the effort to willingly run "mining" software, which does the hashing computations that contribute to monero's blockchain that records exchanges of the cryptocurrency.
But booming interest and sometimes surging values of cryptocurrencies are drawing the interest of cybercriminals on a scale not seen before. And while cybercriminals' interest in stealing computing power to mine cryptocurrency is nothing new, security experts say the scale of such efforts and resulting profits have increased dramatically.
Several security companies this week released new research into how hijacking computers is turning real profits for cybercriminals. In fact, three cryptocurrency mining applications - Coinhive, Crytoloot and Rocks - are now among the top 10 malware families even though the code itself isn't malware, according to Check Point Software. The company estimates that 55 percent of businesses have been affected by cryptocurrency mining applications.
In a report released Thursday, the threat intelligence security vendor Digital Shadows called such schemes the new frontier of fraud.
"With over 1,442 cryptocurrencies in circulation, and new alternative coins - 'altcoins' - emerging every week, cybercriminals have developed several schemes to defraud those looking to profit from the growth in cryptocurrencies," Digital Shadows says.
Mining vs. Ransomware
Cryptocurrency mining is low touch - it requires few interactions between attacker and victims - which may be why it has become such an appealing alternative to schemes such as ransomware for criminals.
"There are many reasons why adversaries might choose to leverage cryptocurrency mining to generate revenue," writes Cisco's Talos intelligence unit in a blog post. "There isn't any command-and-control activity, and it generates revenue consistently until it's removed."
Ransomware encrypts hard drives, with attackers demanding a ransom payable in cryptocurrency. But the cycle is messy: Computers have to be infected with ransomware, and then the victims have to be scared enough to pay out and get their hands on cryptocurrency. Organizations with few options often do opt to pay. While it can be difficult to defend against ransomware, there is growing awareness of needing to have backups for fast recovery.
With cryptocurrency mining, users often remain unaware that their CPU has ticked up a few clock cycles to do attackers' bidding. Mining software doesn't have to be delivered by an exploit, either: It's possible to deliver the mining code via JavaScript, running within an open web browser tab. Google's YouTube, for example, was recently targeted by a malicious advertising campaign to do precisely that while users remained logged into the site watching videos.
Cryptocurrency mining code for sale on the marketplace OpenBazaar. (Source: Digital Shadows)
"Attackers are not stealing anything more than computing power from their victims, and the mining software isn't technically malware," Talos writes. "So theoretically, the victims could remain part of the adversary's botnet for as long as the attacker chooses."
Talos says its research indicates that cryptocurrency-mining botnets could generate up to $100 million a year. Individual infections generating the equivalent of spare change still add up: Talos says creating a modest botnet, consisting of 200,000 nodes, could pull in $500 a day in monero, or $182,500 annually.
Massive Mining Operations
Well-known malware researcher Kafeine, who works for the security firm Proofpoint, has been tracking a massive cryptocurrency mining botnet dubbed Smominru. To infect machines, Smominru uses the leaked NSA exploit, EternalBlue, that enabled the WannaCry ransomware to rapidly spread in May 2017.
Smominru is nearly twice of the size of Adylkuzz, a monero-mining botnet that appeared before the WannaCry attack and also used EternalBlue. The U.S. and U.K. governments attributed WannaCry to North Korea, which has also been suspected of running monero mining operations (see Before WannaCry, Cryptocurrency Miners Exploited SMB Flaw).
"The operators had already mined approximately 8,900 monero (valued this week between $2.8M and $3.6M)," Kafeine writes. Each day, the botnet mined roughly 24 monero, worth an average of $8,500 this week."
With help from the ShadowServer Foundation and Abuse.ch, Smominru's size was estimated at more than 526,000 Windows computers, most of which are servers. "These nodes are distributed worldwide but we observed the highest numbers in Russia, India, and Taiwan," Kafeine writes.
Enterprise Risk
Browser-based mining is the least intrusive because no application has to be installed on a machine. Still, there's the issue of permission: Mining done without asking is considered a no-no. In-browser mining scripts are often positioned as a way for website owners to get an alternative source of revenue without advertising.
"Enterprises have to decide if miners are malware within their environments."
—Cisco Talos
Mining without permission already landed The Pirate Bay in hot water. The site infuriated some users by inserting a miner, Coinhive, into one of its web pages around last September, according to TorrentFreak. Security companies tend to regard this kind of activity as a threat. In October, security firm Malwarebytes said it would block connections to known mining servers but allow users to whitelist them if they choose.
"Regardless of whether the miner was deployed using malicious methods or simply by an enterprise user trying to generate some coin from their work computer, enterprises have to decide if miners are malware within their environments," Talos writes.
Servers Under Serialization Fire
As noted, PCs are not the only systems being targeted. Security firm Imperva, in a recent blog post, warns that cryptocurrency-mining malware attackers are also targeting insecure deserialization in web applications - primarily in Java. Attackers have especially been targeting four specific flaws discovered last year in JBoss Application Server, Oracle WebLogic Server, the REST plugin in Apache Struts and Java Message Service, Imperva says.
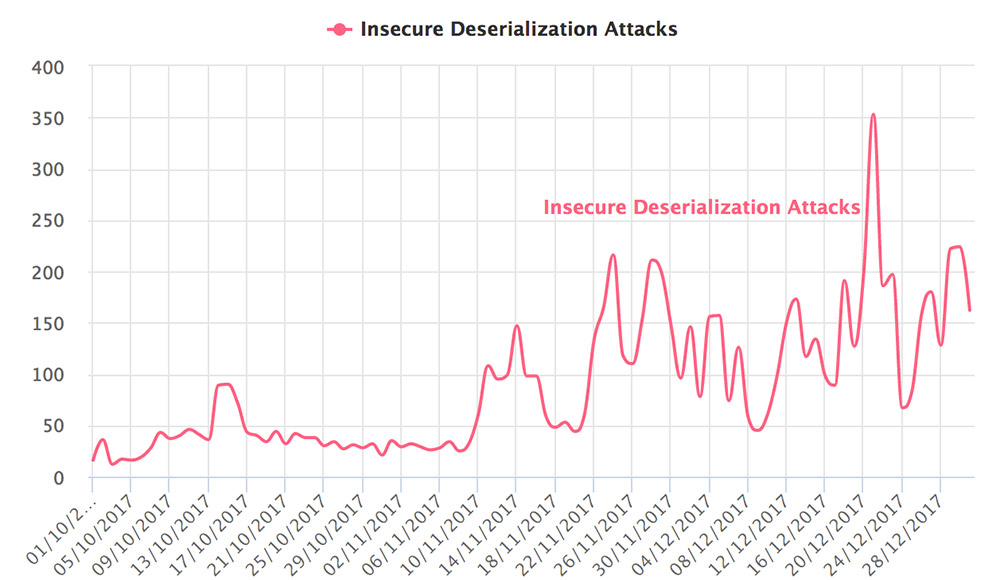
Insecure deserialization attacks over the course of three months, escalating sharply near the end of 2017. (Source: Imperva)
"The process of serialization converts a 'live' object (structure and/or state), like a Java object, into a format that can be sent over the network, or stored in memory or on disk. Deserialization converts the format back into a 'live' object," Imperva says.
By exploiting insecure deserialization, attackers may be able to trick a Java server into running a script to evade security controls and deliver payloads designed to download malware, including cryptocurrency-mining applications.
Mining code that lands on a system via an exploit has a potentially darker side. While compromised systems may just be used for unnoticed mining, that could change if cryptocurrency prices fall. It means whoever is behind the code might shift from mining to something more damaging, thanks to their having already installed a backdoor on the system.