shmu26
Level 85
Thread author
Verified
Honorary Member
Top Poster
Content Creator
Well-known
Forum Veteran
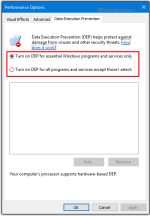
There is an option in advanced system settings of Windows to turn on DEP for all programs and services.
Did you do this, and is it wise to do so?
Did you do this, and is it wise to do so?