No, because then it will not do anything, it will just send notification to the console and wait on your action. Not recommended.
That's what I was "afraid" of

Let me reopen that screen, timeout...
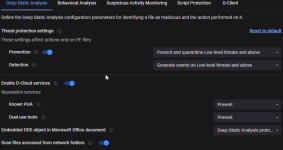
I see two settings: | Script Protection | Deep Script Analysis at the top of this page
Malicious PowerShell Command Execution is set to Prevent
Di info comment (Defines the action that is performed on Powershell commands with malicious content)
____________________________________________________________
bottom half of same screen
Script Control
PowerShell execution is now set to Detect (was set to Prevent) CyF said Prevent will block good powershell commands that windows needs...
I am no expert (did anyone suspect anything different?) But not every powershell command is malicious, right? How do you tell? I'm expecting Di to figure that one out

unrealistic??

Or the 2 scripts blocked overnight perhaps should have not been blocked? And if user has to write a specific rule for each action in windows, that seems unrealistic. Don't get me wrong, I am not saying you are wrong, but should Di be blocking good scripts at 3:55 AM while I'm usually sleeping.


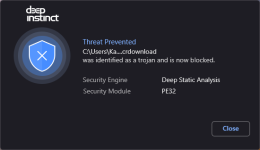
And now seeing the full breakdown of the powershell script block: process chain wininit.exe -> services.exe -> svchost.exe -> CompatTelRunner.exe -> CompatTelRunner.exe -> powershell.exe |
User Name | NT Authority\System
Seeing all the info is Di_nice! Sounds like MS phoning home?? (can't share screenshot as I'm in VM, Di on Host)
So you're saying (I think) better on Prevent, but then when you see an event like this, Di should let user specifically allow that script from that source change the next time. And that's the better procedure every time something like this happens.
But so far worth the trip...