thank you for your swift reply and for your offer, i will contact you.
i am a Real-Time signature-based skeptic by nature, however some things would let me install a signature AV again:
1- light on resources
2- very very few Fps
6- total control of the applications and settings.
Can you give us some infos about those 3 points and your product?
This is really a good question, thanks!
Deepviz is not based on signature, we try to keep ourselves as much far as possible from this approach, I think there are already solid solutions and AV out there that use a signature based approach, the world doesn't really need another player playing the same game.
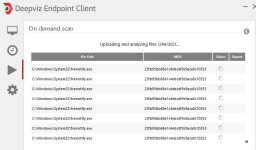
Deepviz analyzes PE files as well as PDF and OLE files (only PE files on the Endpoint Client) thanks to our cloud malware analysis engine, we then extract from the analysis their behaviour as well as static metadata (network activities, packets, code injection, strings from dumped memory etc...) and we match them against our threat intelligence database. Here what happens is:
- We have a set (400+ dynamic rules) to identify malicious activities and thus automatically identify malware
- We have a machine learning AI classifier acting as a second opinion classifier if the above rules don't show anything clear
- We correlate in realtime all the metadata and behavioral information we extracted from the analysis against what we already have in our database. By doing so, we can find malware families and identify similar samples even if they are repacked or slightly modified (this last feature is available only ondemand when you dig into our threat intelligence database, but will be included in the set of automatic determination rules used to automatically find and mark new malware). It's a self-learning database, the more data we inject into it, the better it will perform
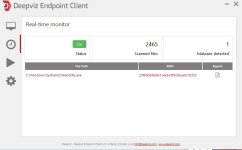
Everything is executed in our backend, thus the client itself is very light on the system. Suspicious files are automatically uploaded to our cloud infrastructure and the result is pushed back to the client. During our internal beta we had good feedback about people almost getting infected by ransomware and alerted by our Endpoint Client where the installed AV didn't see anything at all.
Regarding application control: users will be able to enable/disable realtime monitoring, enable/disable the automatic sample upload (if disabled, the client will only check files against our database but it won't find anything if we don't have already such sample), eventually decide whether the client should prevent file execution or simply monitoring the system (not available yet, the client is only a monitor right now).
The very nice thing about our endpoint client is the centralized cloud-based management console at Deepviz - Endpoint Protection where you can monitor all the endpoints you registered with your API key and check whether they are infected, what malware has been found, deploy specific configurations to the client (not available yet), deactivate registered endpoints and thus free seats.
About false positives: nobody is really FP-free, nor we are, I'd be cheating if I say we are totally FP-free. Our technology is being improved everyday and we will be able to improve it even thanks to your reports and feedbacks. This is the reason why if you find false positives or anything that doesn't work as expected, please don't hesitate and contact me. We will add a local feature to the client where you can right click on files wrongly determined as malware and automatically alert our research team - our engineers will take care about your report and fix it as soon as possible.
I really hope I have provided you with a good understanding of our approach and technology. If not, please keep asking, I'm monitoring this thread and I will try to do my best to reply here as quick as possible.
Thanks!