Do DNS rebinding attacks matter for home users?
Question DNS rebinding attacks
- Thread starter Parkinsond
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Please provide comments and solutions that are helpful to the author of this topic.
They can matter, but for most home users DNS rebinding is a niche but real risk rather than a day‑to‑day concern. It’s most relevant if you have poorly secured routers / NAS / IoT devices on your network.Do DNS rebinding attacks matter for home users?
What is a DNS rebinding attack (in simple terms)?
Very simplified:
- You visit a malicious or compromised website.
- That site runs JavaScript in your browser.
- The attacker controls a domain where the DNS answer can change quickly.
- Initially the domain resolves to the attacker’s server (to load the JS).
- Then the DNS answer is changed to an internal IP, like 192.168.0.1 or 192.168.1.100 (your router or another device).
- Because of how some browsers and same-origin policies work, that JS can then send requests to your internal device as if you directly visited it.
If your internal device has a weak or no password, bad CSRF protections, or dangerous APIs, the attacker might:
- Change router DNS settings
- Open ports / change firewall rules
- Access an insecure NAS web interface
- Control smart home / IoT devices with web UIs
Why it can matter for home users
It’s more relevant if:
- Your router’s admin password is still default or very weak.
- You have NAS/IoT devices with web interfaces exposed to the LAN that:
- Use default credentials, or
- Have weak or no authentication, or
- Trust LAN-origin traffic too much.
- You or others in your home frequently browse random/unknown sites, click on sketchy ads, or run shady web apps.
If an attacker can control your router DNS or firewall from inside the LAN, they might:
- Silently redirect all your traffic via malicious DNS
- Open up ports from WAN to LAN (exposing devices to the internet)
- Inject ads or phishing pages (via malicious DNS)
Why it’s less critical for many home users
A few reasons the practical risk is often limited:
- Modern browsers and some DNS resolvers include partial DNS rebinding protections.
- Many consumer routers now:
- Block admin access from WAN by default
- Require non-default passwords at first setup
- Use basic CSRF protections and/or confirmation prompts
- NAT doesn’t directly stop rebinding (it targets internal IPs), but it does reduce other types of direct attacks from the internet.
- Exploiting this in the wild is more work than simple phishing, malvertising, or credential theft, which are more common.
So for an average home user with:
- A reasonably modern router
- Unique, strong admin password
- No weird custom DNS or exposed admin panels
…DNS rebinding is possible but not the top threat to worry about compared to phishing, weak passwords, and unpatched software.
Practical protection steps (low effort, high value)
If you want to be safer with minimal hassle:
- Secure your router
- Change the default admin username/password to something long and unique.
- Disable remote administration from the internet (WAN) unless you absolutely need it.
- If there’s an option to restrict admin to LAN only, keep that enabled.
- Update router firmware from the official vendor site when possible.
- Harden your internal devices
- Change default passwords on NAS, cameras, smart plugs, etc.
- Disable web admin interfaces you don’t use.
- If your NAS/IoT has an option like “only allow HTTPS” and “require login from LAN”, enable them.
- Use safer DNS resolvers (optionally)
- Some public DNS providers implement DNS rebinding protections (they block responses that resolve public domains to private IP ranges).
- If you use such a provider, DNS rebinding attacks are harder to pull off. Check each provider’s documentation for “DNS rebinding protection” in particular.
- Browser hygiene
- Use an up-to-date browser.
- Consider limiting JavaScript on random sites (script blockers, privacy extensions, or at least adblockers that reduce malvertising).
When you should care more
You should pay extra attention to DNS rebinding risks if:
- You run a home lab (Docker, Kubernetes, self-hosted services, etc.) accessible via browser from your PC.
- You run custom DNS or local hostnames for internal services.
- You expose any internal web console (router, NAS, hypervisor, etc.) to the internet via port forwarding or cloud tunneling.
In those cases, it’s worth:
- Using DNS resolvers with rebinding protection
- Putting admin interfaces behind VPN / SSH / strong auth rather than open web
- Using different browsers or profiles for “admin stuff” vs general browsing
Summary
DNS rebinding can affect home users, mainly by attacking routers/NAS/IoT through your browser, but in practice it’s a lower-frequency threat compared to common attacks. If your router and devices are not using default passwords, remote admin is off, firmware and browser are up to date, and you use a reputable DNS resolver, your real-world risk as a home user is relatively low.
If you want, post your router model and a brief list of devices you have (NAS/cameras/etc.), and I can suggest more specific hardening steps.
Sadly yes, I used to disable DNS Cache, but unfortunately, DoH and DoT rely on it. I disable DNS Cache (DNS Boost in NextDNS), but it does not matter, if Windows uses it.
DNS Cache is an obsolete feature, even if you would use the DNS server on the other side of the world, you would get ~800ms delay, less than a second, hardly noticeable.
DNS Cache is an obsolete feature, even if you would use the DNS server on the other side of the world, you would get ~800ms delay, less than a second, hardly noticeable.
When tested for dns rebinding attack vulnerability, those of NextDns and Adguard (free with account to include Hagezi rebinding protection list) passed, while all the free dns (without account) such as Adguard, ControlD, and others, failed.Sadly yes, I used to disable DNS Cache, but unfortunately, DoH and DoT rely on it. I disable DNS Cache (DNS Boost in NextDNS), but it does not matter, if Windows uses it.
DNS Cache is an obsolete feature, even if you would use the DNS server on the other side of the world, you would get ~800ms delay, less than a second, hardly noticeable.
I wonder, what test did you use? ControlD failed a basic NRDs, they supposedly fixed it, but how the hell can you fail that, unless they cheated and used a blacklist?while all the free dns (without account) such as Adguard, ControlD, and others, failed.
If the domain is less than 30 days old, it should be blocked automatically, yet they failed doing that. I like their free service, but I have some reservation about it. We had a crash.
I wonder, what test did you use?
DNS Rebind Test: Secure Your Network from Hidden Threats
Protect your devices from DNS rebinding attacks. Run a DNS rebind test to guard against malicious actors and keep your data safe.
I think that the problem is that the service uses ControlD and bigdig.energy to test, so it might be a little biased.
DNS Rebind Test: Secure Your Network from Hidden Threats
Protect your devices from DNS rebinding attacks. Run a DNS rebind test to guard against malicious actors and keep your data safe.controld.com
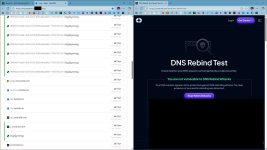
ControlD free failed to pass ControlD test; NextDNS and Aguard (with rebinding attack protection enabled in controld or rebinding attack hagezi list included in adguard) pass the test with success.I think that the problem is that the service uses ControlD and bigdig.energy to test, so it might be a little biased.
View attachment 293319
I am "not vulnerable to DNS Rebind Attacks"  on this VM according to
on this VM according to

 controld.com
controld.com

DNS Rebind Test: Secure Your Network from Hidden Threats
Protect your devices from DNS rebinding attacks. Run a DNS rebind test to guard against malicious actors and keep your data safe.
I would piss in my pants if my multi-zillion dollar network infrastructure is exposed by such an attack. I spent half a day configuring it. I just hope the router updates will help. I passed the test posted above.
Last edited:
It reported some routers are equipped with dns rebinding attack protection; mine does not have such an option in settings, but NextDNS and Adguard DNS (the free account with 300K limit) have.I just hope the router updates will help
What router do you use? Most Routers already have DNS Rebinding Protection included. Even the basic ones.It reported some routers are equipped with dns rebinding attack protection; mine does not have such an option in settings, but NextDNS and Adguard DNS (the free account with 300K limit) have.
Here for example my Asus router:
ISP-provided "sub-basic" oneEven the basic ones
Never heard of that one but Google says it also has DNS Rebinding Protection. Open the Router interface and scroll through the WAN settings. Maybe you find it thereISP-provided "sub-basic" oneIt is Zyxel.
It is a Taiwanese brand; it is not bad compared to my ISP worse routers by ZTE, but it looks like a low-end one by Zyxel, lacking several features.Never heard of that one but Google says it also has DNS Rebinding Protection. Open the Router interface and scroll through the WAN settings. Maybe you find it there
ISPs do not care about security; only profit matters.
Last edited:
Ziggo with Sagemcom Modem/Router. Netherlands
ControlD Free DNS (HaGeZi Pro Plus) absolutely passes this test on my PC. I'm connecting through my Asus router (which is behind the NAT of ISP issued router Huawei).ControlD free failed to pass ControlD test; NextDNS and Aguard (with rebinding attack protection enabled in controld or rebinding attack hagezi list included in adguard) pass the test with success.
Failed for me, as well as all the free dns plans by controld and other providers; only passed with NextDNS (only with enabled rebinding protection in settings) and Adguard free account (with including Hagezi rebind protection list).ControlD Free DNS (HaGeZi Pro Plus) absolutely passes this test on my PC. I'm connecting through my Asus router (which is behind the NAT of ISP issued router Huawei).
View attachment 293325
It's either your web browser acting up or you misconfigured ControlD; can't be anything else.Failed for me, as well as all the free dns plans by controld and other providers; only passed with NextDNS (only with enabled rebinding protection in settings) and Adguard free account (with including Hagezi rebind protection list).
If you're willing to test:
Open your browser DoH settings, enter
https://freedns.controld.com/x-hagezi-proplus and try again. It should pass the test immediately. If you still don't pass the test, try doing the same in Firefox and see if it passes the test. If it does, your default browser is acting up and not the ControlD.Didn't pass again? Download and run tiny ControlD Setup Utility (doesn't need installing, just running), for Resolver ID enter
x-hagezi-proplus and click Connect button. This will make ControlD system-wide and now it should definitely pass this test in all web browsers. If neither works, it's your router then and not the ControlD or your device.To stop using ControlD Setup Utility, run it again and press Disconnect button. This will remove ControlD entirely from your system.
Last edited:
Edge stable (updated)It's either your web browser acting up
ControlD free has no settings; it is similar to Adguard free without account (with account, AG free is customizable, such as NextDNS).or you misconfigured ControlD
You may also like...
-
-
Serious Discussion HaGeZi DNS: Free, Non-Commercial EU Public DNS Servers
- Started by rashmi
- Replies: 13
-
-
Security News Ongoing Attacks Exploiting Critical RCE Vulnerability in Legacy D-Link DSL Routers
- Started by Parkinsond
- Replies: 10
-


