1) for me, it's a lot. because my svchosts rarely uses that much. My laptop is bad at battery life. 1.5% can cause significant battery drain for me. When I don't use anything, no internet traffic, it must stay calmly at 0%, or it should be removed. It's just me. I care about resource usage and performance x10 than security and privacy
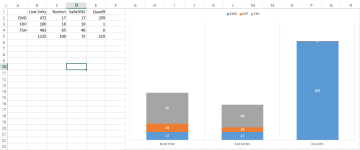
2) depends on its purpose. IMO, it should use =<50MB in total. It even used x2 more RAM than KIS 2018
3) I didn't know that so I didn't change the DNS to google's before the test but it didn't matter much
5) According to my test, KIS's web filter is much much better than Heimdal. Kaspersky is always one of the first vendors to block a brand new phishing on VT, even sooner than Forti and netcraft. I think KIS's web filter + Norton DNS + Google SafeBrowsing should be more than enough for most users
5*) Although we can get it for 50% off but I still think our AV's filter is good enough. Or if we are a bit more paranoid, we can install Panda safe web (though it's like an adware). Everyone can install it as system-wise malware blocker for free