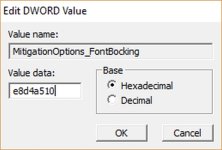
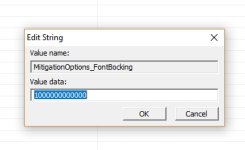
You found out this by yourself, so I was late. Every reg tweak I put in my post is exported from the Registry. So, it can be imported via regedit.exe . For example create the file UntrustedFontBlocking.reg in the notepad and copy the text between asterisks:
**********
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows NT\MitigationOptions]
"MitigationOptions_FontBocking"="1000000000000"
**********
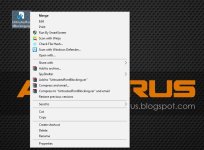
then import the UntrustedFontBlocking.reg in regedit.exe (Menu-File-Import) .