PROGRAM INFO
The application can be used on Windows 8+. New ver. 5.1.0.0 available (updated in December 2025).
GitHub - AndyFul/Run-By-Smartscreen
Why the SmartScreen?
The Windows built-in SmartScreen technology is one of the best for fighting 0-day malware files.
Why 'Run By SmartScreen'?
More info:
https://github.com/AndyFul/Run-By-Smartscreen
The application can be used on Windows 8+. New ver. 5.1.0.0 available (updated in December 2025).
GitHub - AndyFul/Run-By-Smartscreen
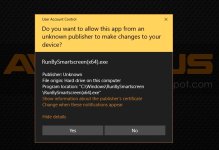
Run By Smartscreen' is a very simple idea to safely open/run the new files via the option on the Explorer right-click context menu. 'Run By Smartscreen' can mark files with MOTW, so they are treated as downloaded from the Internet. This forces the SmartScreen before running the executable with MOTW. Furthermore, the popular documents marked with MOTW will be opened in 'Protected View', if the document application has such an ability (like MS Office 2010+ and Adobe Acrobat Reader 10+). Many file types with unsafe extensions will be blocked when 'Run By Smartscreen' to minimize the chances of infection.
Why the SmartScreen?
The Windows built-in SmartScreen technology is one of the best for fighting 0-day malware files.
Why 'Run By SmartScreen'?
This technology is only halfway adopted in Windows. SmartScreen for Explorer can check executables with the "Mark of the Web", which is attached to files after downloading from the Internet by popular Web Browsers, Windows Store, or Windows OneDrive. There are many cases when files do not have the "Mark of the Web," and then, they are simply ignored by SmartScreen.
More info:
https://github.com/AndyFul/Run-By-Smartscreen
Last edited: