silversurfer
Super Moderator
Thread author
Verified
Top Poster
Staff Member
Malware Hunter
Forum Veteran
- Aug 17, 2014
- 12,746
- 123,926
- 8,399
Chances are that if you deploy a Linux server online these days and you leave even the tiniest weakness exposed, a cybercrime group will ensnare it as part of its botnet.
The latest of these threats is named DreamBus. Analyzed in a report published last week by security firm Zscaler, the company said this new threat is a variant of an older botnet named SystemdMiner, first seen in early 2019.
Currently, the botnet targets enterprise-level apps that run on Linux systems. Targets include a wide collection of apps, such as PostgreSQL, Redis, Hadoop YARN, Apache Spark, HashiCorp Consul, SaltStack, and the SSH service. [...]
Zscaler also said that DreamBus employed quite a few measures to prevent easy detection. One of them was that all systems infected with the malware communicated with the botnet's command and control (C&C) server via the new DNS-over-HTTPS (DoH) protocol. DoH-capable malware is very rare, as it's complex to set up.
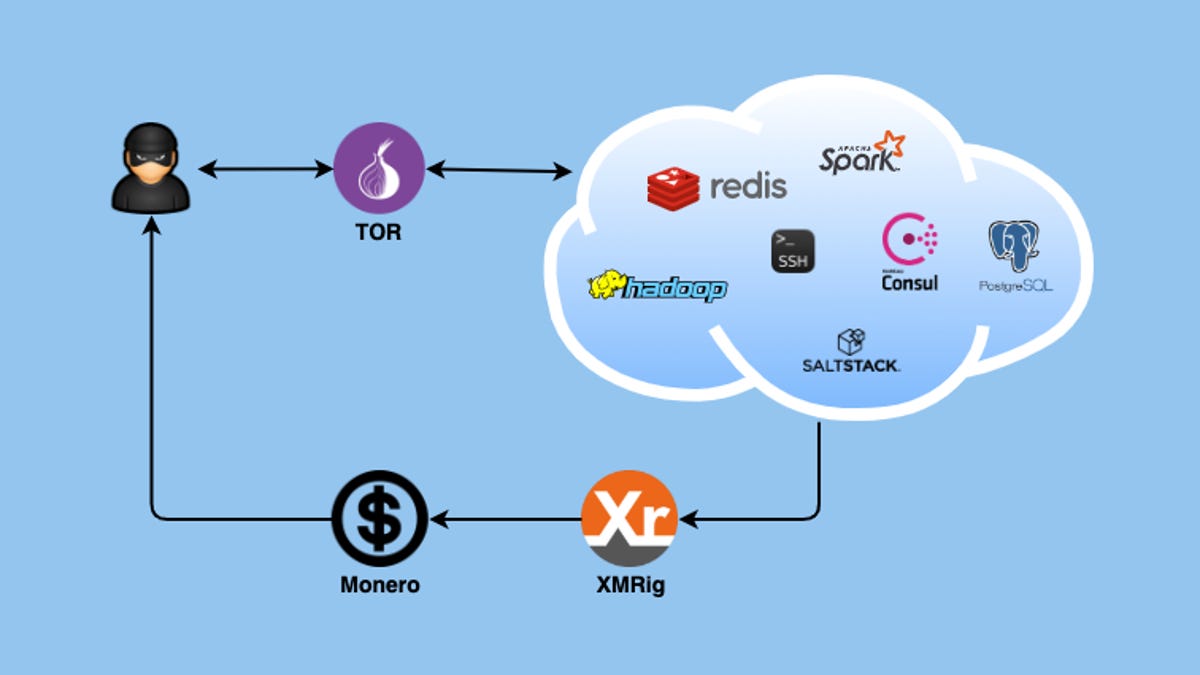
DreamBus botnet targets enterprise apps running on Linux servers
DreamBus botnet uses exploits and brute-force to target PostgreSQL, Redis, SaltStack, Hadoop, Spark, and others.
 www.zdnet.com
www.zdnet.com