App Install Control - Easy Application Control on Windows
Post updated/corrected in July 2025
On Windows 11, App Install Control works when SAC is in Evaluate Mode or OFF.
Default list of blocked file types (Windows 11):
.ade, .adp, .app, .appref-ms, .asp, .bas, .bat, .cer, .chm, .cmd, .cnt, .com, .cpl, .crt, .csh, .der, .exe, .fxp, .gadget, .grp, .hlp, .hpj, .hta, .img, .inf, .ins, .iso, .isp, .its, .js, .jse, .ksh, .lnk, .mad, .maf, .mag, .mam, .maq, .mar, .mas, .mat, .mau, .mav, .maw, .mcf, .mda, .mdb, .mde, .mdt, .mdw, .mdz, .msc, .msh, .msh1, .msh1xml, .msh2, .msh2xml, .mshxml, .msi, .msp, .mst, .msu, .ops, .pcd, .pif, .pl, .plg, .prf, .prg, .printerexport, .ps1, .ps1xml, .ps2, .ps2xml, .psc1, .psc2, .psd1, .psm1, .pst, .reg, .scf, .scr, .sct, .shb, .shs, .slk, .theme, .tmp, .vb, .vbp, .vbs, .vhd, .vhdx, .vsmacros, .vsw, .webpnp, .website, .ws, .wsc, .wsf, .wsh, .xnk
Those are file types that Windows Attachment Manager labels as high-risk:
https://learn.microsoft.com/en-us/t...rivacy/information-about-the-unsafe-file-list
On Windows 11, it is possible to extend the Block List to include other file types by editing the Registry key:
Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\safer\CodeIdentifiers
Details can be found in the post:
https://malwaretips.com/threads/easy-application-control-on-windows.130803/post-1085791
It would be recommended to add:
.accda, .accdu, .cab, .csv, .diagcab, .dqy, .ecf, .elf, .fon, .ime, .iqy, .jar, .mdf, .mdn, .oqy, .pa, .ppa, .ppam, .rqy, .rtf, .settingcontent-ms, .wll, .wwl, .xla, .xll, .xlm
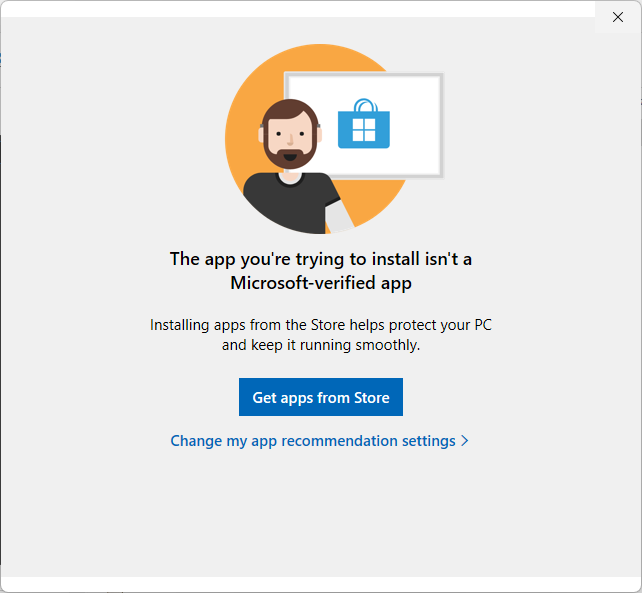
If it is applied by Windows Policy, the user cannot remove it via "Change my app recommendation settings."
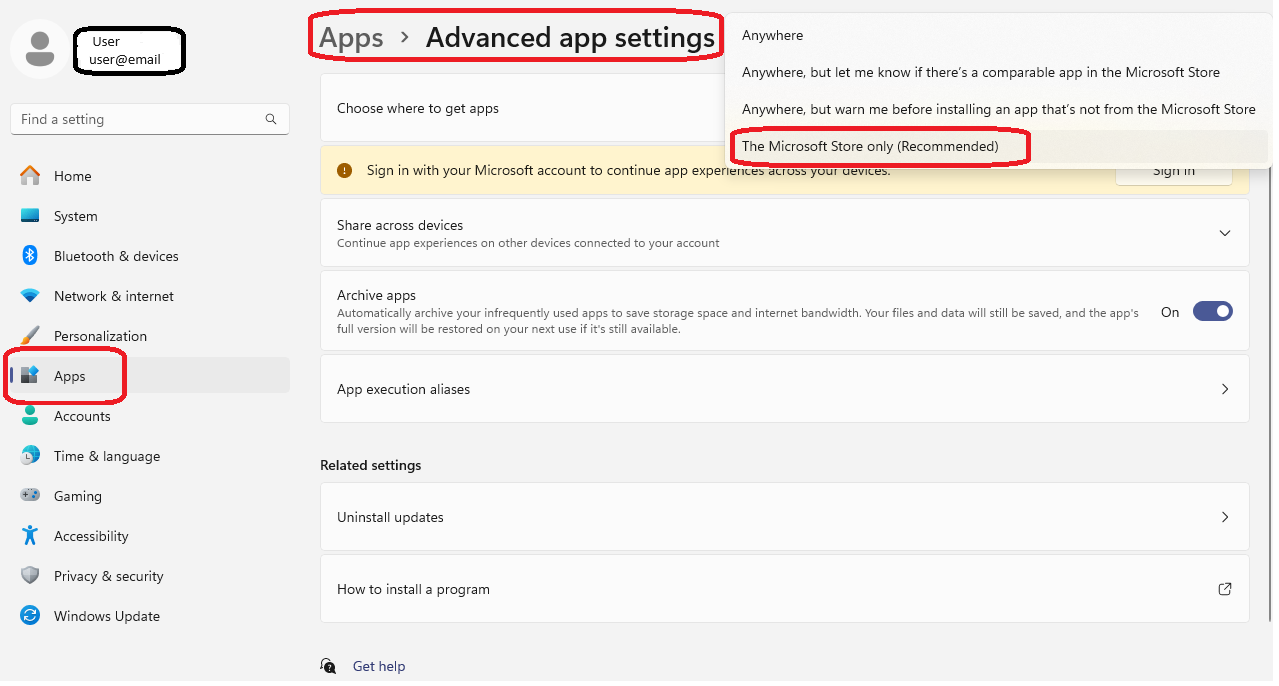
How to apply Easy Application Control from the Windows Settings panel (no policy).
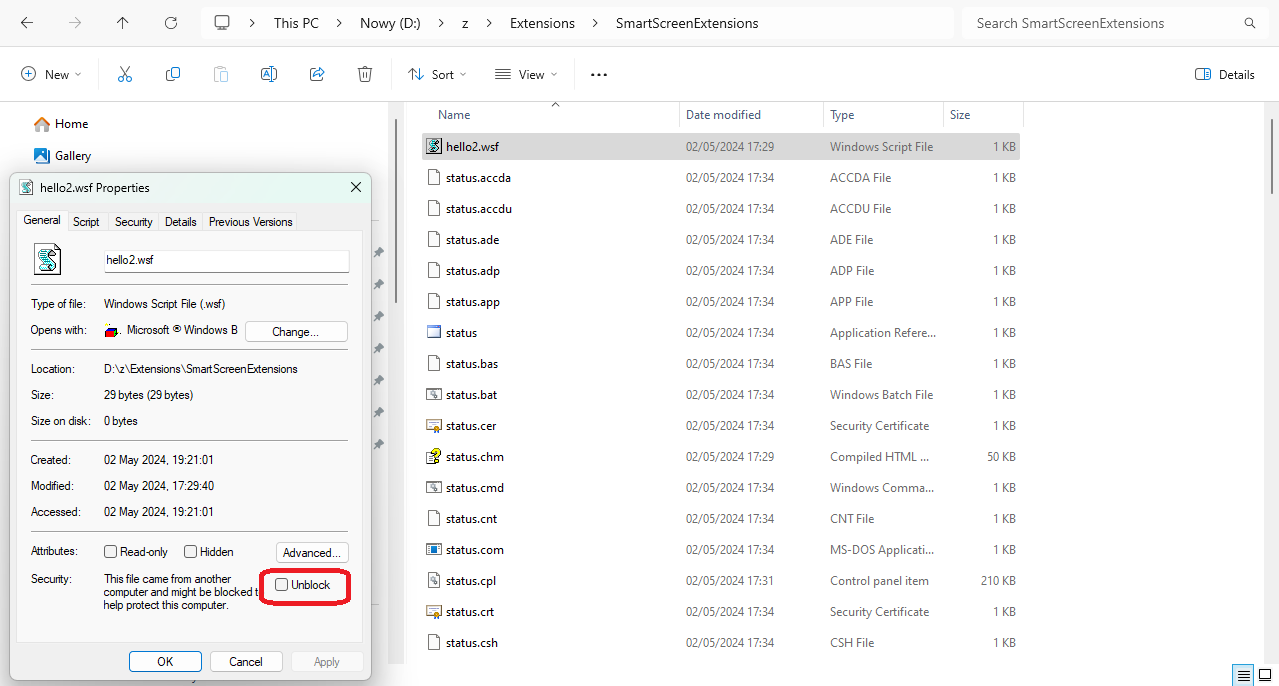
How to unblock the file.
Easy Application Control can cover almost all initial attack vectors at home if one uses Microsoft Defender + ConfigureDefender, Windows built-in applications (archiver, email-client, etc.), and MS Office. See also:
https://malwaretips.com/threads/easy-application-control-on-windows.130803/post-1085906
Post updated/corrected in July 2025
On Windows 11, App Install Control works when SAC is in Evaluate Mode or OFF.
- Can be easily applied in a few seconds.
- Blocks files originating from the Internet Zone (files downloaded from the Internet - files with MotW).
On Windows 11, the Default Block List includes over 100 file types (executables, scripts, scriptlets, shortcuts, etc.).
On Windows 10, the Block List is smaller (.appref-ms, .bat, .chm, .cmd, .com, .cpl, .exe, .gadget, .hta, .js, .jse, .msc, .msi, .msp, .msu, .printerexport, .pif, .ps1, .scr, .settingcontent-ms, .vb, .vbs, .wsf). - Allows popular documents, media files, and other files usually downloaded by home users (except application installers).
- Does not affect already installed applications and software auto-updates.
- Cannot break anything (installed software, Windows Updates, etc.).
- No whitelisting, but the blocked file can be unblocked from the right-click Explorer context menu. Unblocking files bypasses SmartScreen file reputation on execution, so this method should be used with caution and only for files downloaded from highly reputable sources like, for example, the Ninite or Softpedia websites:
https://ninite.com/
https://win.softpedia.com/ - The Ninite website can be added to the Trusted Zone via Internet Options, and then the downloaded app installers are ignored by Easy Application Control (no need to Unblock the downloaded executable). This method can be recommended for casual users.
https://malwaretips.com/threads/easy-application-control-on-windows.130803/post-1132454 - Another method that avoids Unblocking application installers is installing/updating applications via UniGetUI, Winstall, or Patch My PC. These reputable resources do not use MotW, so the installations are not affected by Easy Application Control.
https://apps.microsoft.com/detail/xpfftq032ptphf?hl=en-US&gl=US
https://winstall.app/apps
https://www.softpedia.com/get/Others/Signatures-Updates/Patch-My-PC.shtml - Allows application installations via Microsoft Store and gaming platforms (Steam, Epic Games, etc.).
- Does not protect from malware distributed via removable drives shared with other people.
Default list of blocked file types (Windows 11):
.ade, .adp, .app, .appref-ms, .asp, .bas, .bat, .cer, .chm, .cmd, .cnt, .com, .cpl, .crt, .csh, .der, .exe, .fxp, .gadget, .grp, .hlp, .hpj, .hta, .img, .inf, .ins, .iso, .isp, .its, .js, .jse, .ksh, .lnk, .mad, .maf, .mag, .mam, .maq, .mar, .mas, .mat, .mau, .mav, .maw, .mcf, .mda, .mdb, .mde, .mdt, .mdw, .mdz, .msc, .msh, .msh1, .msh1xml, .msh2, .msh2xml, .mshxml, .msi, .msp, .mst, .msu, .ops, .pcd, .pif, .pl, .plg, .prf, .prg, .printerexport, .ps1, .ps1xml, .ps2, .ps2xml, .psc1, .psc2, .psd1, .psm1, .pst, .reg, .scf, .scr, .sct, .shb, .shs, .slk, .theme, .tmp, .vb, .vbp, .vbs, .vhd, .vhdx, .vsmacros, .vsw, .webpnp, .website, .ws, .wsc, .wsf, .wsh, .xnk
Those are file types that Windows Attachment Manager labels as high-risk:
https://learn.microsoft.com/en-us/t...rivacy/information-about-the-unsafe-file-list
On Windows 11, it is possible to extend the Block List to include other file types by editing the Registry key:
Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\safer\CodeIdentifiers
Details can be found in the post:
https://malwaretips.com/threads/easy-application-control-on-windows.130803/post-1085791
It would be recommended to add:
.accda, .accdu, .cab, .csv, .diagcab, .dqy, .ecf, .elf, .fon, .ime, .iqy, .jar, .mdf, .mdn, .oqy, .pa, .ppa, .ppam, .rqy, .rtf, .settingcontent-ms, .wll, .wwl, .xla, .xll, .xlm
If it is applied by Windows Policy, the user cannot remove it via "Change my app recommendation settings."
Code:
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows Defender\SmartScreen]
"ConfigureAppInstallControlEnabled"=dword:00000001
"ConfigureAppInstallControl"="StoreOnly"How to apply Easy Application Control from the Windows Settings panel (no policy).
How to unblock the file.
Easy Application Control can cover almost all initial attack vectors at home if one uses Microsoft Defender + ConfigureDefender, Windows built-in applications (archiver, email-client, etc.), and MS Office. See also:
https://malwaretips.com/threads/easy-application-control-on-windows.130803/post-1085906
Last edited:





