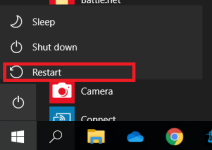
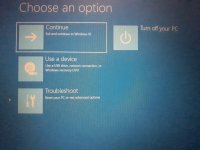
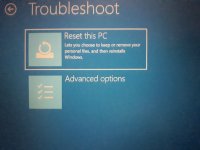
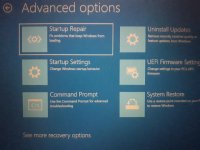
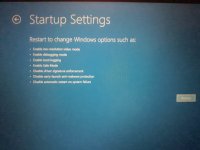
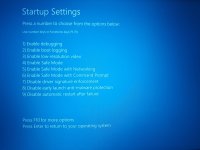
Try this for safe mode in Windows 10:
That looks like a good answer.
Thanks Nightwalker.
Me and my buddy @beavisviruses were the two inaugural members of the "I love ESET" Club.
I miss that guy...
Try this for safe mode in Windows 10:
Hold "Shift" whilst clicking on "Restart"my computer will not go into safe mode!!!!!!!!!!!!!!
your link says as follows
In Safe Mode, double-click the installer file you saved to your Desktop in step 1 to run ESET Uninstaller tool. If you want to use the Advanced user commands below, open an Administrative command prompt first and then change to the Desktop directory.
That looks like a good answer.
Thanks Nightwalker.
View attachment 228636
Me and my buddy @beavisviruses were the two inaugural members of the "I love ESET" Club.
I miss that guy...
He is still here posting with another clone https://malwaretips.com/members/virusesmaximum.81859/
Discuss - Kaspersky Security Network "KSN"
Me too, his "love letters" were so fun.
Back to talking about ESET: the signatures seem to be pretty decent. @Huchim ’s malware hub testing shows ESET catching more than average via static scan. This morning I encountered some malvertising and submitted it to VT, and it had a 2 or 3 engine detection ratio (not Symantec, Avira, or BitDefender) and NOD32 was one that detected it.


This is a common misconception of ESET, most of those detections are not via signatures, they are heuristics + generic detections, so by definition a zero day kind of protection.
Many security forum users think that ESET has a poor zero day protection because until recently it lacked a properly behavior blocker and most users confused the heuristic detection (proactive) with a signature (reactive) one.
Extremely low. For example, in the September False Alarm test, by AV-Comparatives, ESET and Kasperksy were the only products with no false positives. In March, there was only one false positive, beating all other antiviruses tested.How's the FP rate for ESET?
This is correct. Also what I've learnt from the ESET forum is that they are extremely sensitive about false positives and performance impact. Sometimes way too much. For example, a month ago in the hub a ransomware sample was missed by ESET as well as bypassed other popular AVs behavior blocker. I posted that sample on ESET forum and a day later upon analyzing they found out, ESET's ransomware shield initially detected that as a potential ransomware but another false positive mechanism triggered in so to avoid false positive ESET let that ransomware run. This is just one example. I've seen other discussion where they even said that they sometimes prioritize avoiding false positives over detection and their defense to this statement was that if an user run something malicious on their PC, soon their cloud protection which is named Live grid would be able to protect other users from executing that malware. They also said their enterprise customers care more about not having any false positives. But no matter what, to prioritize false positives avoiding over detection kind of sounds wrong. But this is how they are and one of the reason they focus a lot on signatures more than most other AVs. They have similar mindset for performance impact. They won't implement any feature that affects its performance hence it's extremely light.Extremely low. For example, in the September False Alarm test, by AV-Comparatives, ESET and Kasperksy were the only products with no false positives. In March, there was only one false positive, beating all other antiviruses tested.
This is a common misconception of ESET, most of those detections are not via signatures, they are heuristics + generic detections, so by definition a zero day kind of protection.
Many security forum users think that ESET has a poor zero day protection because until recently it lacked a properly behavior blocker and most users confused the heuristic detection (proactive) with a signature (reactive) one.
Take those tests from @Huchim as an example:

That’s interesting and rather concerning. However with non-risky habits and a good web extension probably pretty unlikely you would run across the type of zero day samples seen in the hub. Still it gives me pause.This is correct. Also what I've learnt from the ESET forum is that they are extremely sensitive about false positives and performance impact. Sometimes way too much. For example, a month ago in the hub a ransomware sample was missed by ESET as well as bypassed other popular AVs behavior blocker. I posted that sample on ESET forum and a day later upon analyzing they found out, ESET's ransomware shield initially detected that as a potential ransomware but another false positive mechanism triggered in so to avoid false positive ESET let that ransomware run. This is just one example. I've seen other discussion where they even said that they sometimes prioritize avoiding false positives over detection and their defense to this statement was that if an user run something malicious on their PC, soon their cloud protection which is named Live grid would be able to protect other users from executing that malware. They also said their enterprise customers care more about not having any false positives. But no matter what, to prioritize false positives avoiding over detection kind of sounds wrong. But this is how they are and one of the reason they focus a lot on signatures more than most other AVs. They have similar mindset for performance impact. They won't implement any feature that affects its performance hence it's extremely light.
I agree. ESET is still great though. It's also one of the best in web protection. In my personal brief testing over the last few months it performed better than Kaspersky, Bitdefender, Avira, SmartScreen in most cases. I don't use any security extension on my browser when I use ESET as I feel it's enough.That’s interesting and rather concerning. However with non-risky habits and a good web extension probably pretty unlikely you would run across the type of zero day samples seen in the hub. Still it gives me pause.
. While good zero day protection is a good thing to have, I still think that people stress about it way to much IMHO. Personally I feel like the chances of home users running into a true zero day (malware) is extremely low. Doesn't mean it doesn't happen, but I don't think it's as high, compared to if you were a business/enterprise, government body, etc...
That’s interesting and rather concerning. However with non-risky habits and a good web extension probably pretty unlikely you would run across the type of zero day samples seen in the hub. Still it gives me pause.
Yeah I'd say the last time I got surprised by malware (and needed to be saved by an AV) was 3+ years ago, when I was being stupid and thought I found a trustworthy Windows Loader (activation bypass) that was actually a rootkit. That wasn't even a zero day.
With that said, zero days are still a thing, albeit rare. Just yesterday when browsing 9to5mac I got redirected by a rogue advertisement to a "your Norton has expired" scam hosted on a .XYZ domain. The domain was fresh and had zero detection on VT. The payload it delivered was Mac malware but it was a zero day with a 2/59 detection ratio (up to 4/59 if I unpack various scripts and submit them separately, which more simulates what a runtime scanner would find). I checked again today and the detection ratio is much higher.
Sure it's Mac malware and that's different than Windows malware, but average Joes can still encounter these kinds of zero days.
(BTW ESET was one of 2 engines that actually caught it though, so I'd say your zero day protection is just fine on ESET)
It’s funny because that is sometimes true but not always. It is true that sometimes engines will detect the malware once the payload is actually delivered (the bogus installer or fake .app bundle is usually obfuscated and uses shell scripts or Python combined with the openssl command to decrypt a command for fetching the real malware, and the real malware itself tends to be more widely detected.I've seen a few of those too. But when I send them to the vendors they tell me that they do detect the actual malware, just not the .DMG file itself.
Back to talking about ESET: the signatures seem to be pretty decent. @Huchim ’s malware hub testing shows ESET catching more than average via static scan. This morning I encountered some malvertising and submitted it to VT, and it had a 2 or 3 engine detection ratio (not Symantec, Avira, or BitDefender) and NOD32 was one that detected it.
It’s funny because that is sometimes true but not always. It is true that sometimes engines will detect the malware once the payload is actually delivered (the bogus installer or fake .app bundle is usually obfuscated and uses shell scripts or Python combined with the openssl command to decrypt a command for fetching the real malware, and the real malware itself tends to be more widely detected.
But this particular one seemed so new that even the final payload isn’t detectable. I submitted it to a few vendors. Hilariously Symantec responded with the sample “is an archive” and then explains what a zip file is. Sigh.
It uses https scanning system wide, so no extension is used.eset smart security not have browser advisor like bitdefender or kaspersky ?