- May 10, 2019
- 2,289
No Kaspersky doesn't have HIPS but it has application control and behaviour blocker. Both of them when configured correctly can make you PC bulletproof.
No Kaspersky doesn't have HIPS but it has application control and behaviour blocker. Both of them when configured correctly can make you PC bulletproof.
Can others please clarify? Are they referring to Application Control as HIPS?@harlan4096
Great to see you back !A word of warning regarding ESET-
Although ESET has improved in detection of various types of Scriptors, some malware authors have circumvented the need for scripting in Powershell, Python, etc and have utilized other avenues to achieve similar results. These methods can yield malware that is harder for some AV applications to detect as they can be based on stuff like certutil, a valid command.
ESET has issues with this type of malware, even with the HIPS set at max protection. A ransomware file can be coded simply and easily to bypass the HIPS and encrypt files. Also, as coding is rather straightforward, the file would be zero day and bypass the AV.
This issue is by no means restricted to ESET, as programs from Forticlient to SEP will also fail. However quite a few (like Kaspersky, Avast/AVG, CF) will laugh at this stuff and block it quite easily.
As far as I know HIPS can be activated when you untick Kaspersky automatic mode (forgot the exact naming of that option as I am no longer using Kaspersky). Even on the automatic mode, HIPS runs in smart mode without asking for user's interaction.Can others please clarify? @harlan4096
Yeah in the interactive mode, kis produces a lot of alerts. But the last time I tried kis in Interactive mode, the alerts came from Application Control. I found no evidence relating to HIPS.As far as I know HIPS can be activated when you untick Kaspersky automatic mode (forgot the exact naming of that option as I am no longer using Kaspersky). Even on the automatic mode, HIPS runs in smart mode without asking for user's interaction.
Yes Application Control is one kind of HIPS. There are a minimum of 3 types of HIPS used in AV products. I forgot who it was but someone in the forum beautifully explained all types of HIPS in a thread.
Good question. I never though of it before. I am pretty sure that ESET's real time protection doesn't monitor registry changes except its own which is monitored by HIPS. If a malware makes registry modification ESET can't stop that from happening. About the scanning part I had to search and I found a very disappointing answer. This is a response from 2015 when a user asked why Eset can't fix the registry entries made by malware:One thing I really want to know but haven't found any concrete answers yet. Does ESET protect the registry? I've never seen it scan the windows registry hive even in the Full Scan.
So, Eset can't do anything about registry and I guess this is why you never saw it scanning registries.Because security policies were created by Microsoft for a reason and it's not possible to distinguish between policies set by malware and those set by users (administrators). ESET has stand-alone cleaners for some of the mentioned malware modifications which should be used to revert such changes, if not made intentionally
I suppose that you are referring to more and more LOLBins being exploited to bypass application control and UAC ... and that some AVs are just not focusing on this aspect enough.A word of warning regarding ESET-
Although ESET has improved in detection of various types of Scriptors, some malware authors have circumvented the need for scripting in Powershell, Python, etc and have utilized other avenues to achieve similar results. These methods can yield malware that is harder for some AV applications to detect as they can be based on stuff like certutil, a valid command.
ESET has issues with this type of malware, even with the HIPS set at max protection. A ransomware file can be coded simply and easily to bypass the HIPS and encrypt files. Also, as coding is rather straightforward, the file would be zero day and bypass the AV.
Kaspersky and the likes could be monitoring LOLBin exploitation methods in a better manner. Some AVs will cover a range of these attacks well, but others might just cover another range better, or overlap. In the cat-and-mouse game, different cats will have different points of strengthThis issue is by no means restricted to ESET, as programs from Forticlient to SEP will also fail. However quite a few (like Kaspersky, Avast/AVG, CF) will laugh at this stuff and block it quite easily.
@SeriousHoax has already covered the point. I'll just add that you can make HIPS rules to protect "specific" or "all" registry entries from below operations:One thing I really want to know but haven't found any concrete answers yet. Does ESET protect the registry? I've never seen it scan the windows registry hive even in the Full Scan. @SeriousHoax know anything on this?
And they did not care to explain on the forum whyI am pretty sure that ESET's real time protection doesn't monitor registry changes except its own which is monitored by HIPS. If a malware makes registry modification ESET can't stop that from happening. About the scanning part I had to search and I found a very disappointing answer.
Such as blocking powershell altogether if you don’t use it often.ESET HIPS is useful for making advance custom rules.
Yes they never explain this type of questionsAnd they did not care to explain on the forum whyTheir usual stand you must have seen is that they feel doing something is unnecessary. And that they have other modules to take care of it in some or the other way. Maybe their DNA detections are fortified to detect code related to suspicious registry operations and they are strongly relying just on that. .
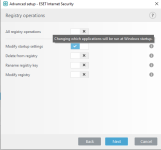
Yeah once upon a time I had a HIPS rule to monitor startup applications. But since Nvidia GeForce Experience came into my PC, I got mad with alerts. Is it so much of a hassle just to include the registry in a full scan? Malwarebytes seems to do a thorough registry scan with their quick scan and it's just the main reason I've kept the program as my back-up scanner. If Malwarebytes can implement it, why not ESET? And if ESET implements this I'll no longer need mbam.@SeriousHoax has already covered the point. I'll just add that you can make HIPS rules to protect "specific" or "all" registry entries from below operations:
View attachment 236612
For most users, "all" is not a practical option. You'll be bombarded with alerts and can screw the system. But you can use the option to protect 'startup settings' at the very least. Eg. you could use HIPS rule to protect registry changes done to restrict Powershell.
Not related to real-time protection, but you can use a "SysInspector" snapshot of a clean system and compare with a new snapshot whenever you wish to. SI takes a snapshot of processes, drivers, network connections, registry etc. SysInternals Autoruns is a good alternative.
And they did not care to explain on the forum whyTheir usual stand you must have seen is that they feel doing something is unnecessary. And that they have other modules to take care of it in some or the other way. Maybe their DNA detections are fortified to detect code related to suspicious registry operations and they are strongly relying just on that. .
In these cases OSArmor plays nice with ESET, or some hardening.Yes they never explain this type of questionsThey do rely heavily on their Advanced DNA detections which is serving them pretty well. They're also good against targeted attacks, remote code executions, etc but their product can't handle threats when legit processes like you said lolbins are used to do the dirty work. What's your opinion about this Enhanced Real World Test where only Eset and Kaspersky blocked everything and most other didn't even agree to take part in: Enhanced Real-World Test 2019 – Consumer | AV-Comparatives
You have good protection from ESET and OSArmor against email attachments and other downloads.Also, in this case since they add signatures so fast wouldn’t it work most of the time to just save attachments/download for a day or two Before executing them? I know that wouldn’t stop everything, but that would cover your butt for a whole bunch of stuff.
There are limitations. Eg. attacks can bring their own powershell binaries too. Hence it's about reducing the attack surface, limited by the features. Monitoring unknown executed binaries and restricting powershell-related commandlines is one step ahead of this.Such as blocking powershell altogether if you don’t use it often.One of my favorite rules. I have no doubt someone like @cruelsister could own my computer if they wanted. So I just lay low and try to play nice and avoid the every day attack. Zero days are very interesting, but if I worry about them too much I lose a lot of sleep unnecessarily.
Yeah spot on. OSArmor and ESET seems to make a great combo. I personally also suggest Syshardener to disable all scripts. I'm thinking of following @harlan4096 and adding sandboxie so that my browser always run sandboxed. That way 99% of threats will be eliminated.In these cases OSArmor plays nice with ESET, or some hardening.
Safe email habits should minimize the stakes already.
The test uses Powershell attacks for most of the part, C# (high level programming language) malware and office macros - all of these using different techniques and known exploit frameworks including pen-testing tools. What good would pen-test tools be if AVs could easily defeat them?They do rely heavily on their Advanced DNA detections which is serving them pretty well. They're also good against targeted attacks, remote code executions, etc but their product can't handle threats when legit processes like you said lolbins are used to do the dirty work. What's your opinion about this Enhanced Real World Test where only Eset and Kaspersky blocked everything and most other didn't even agree to take part in: Enhanced Real-World Test 2019 – Consumer | AV-Comparatives
Many others not participating just indicate they're either not prepared or are not confident about their efficacy.The tools employed include heavily obfuscated malicious code, the malicious use of benign system tools, and non-file-based malicious code.
I just missed your post buddywhat about false positives is it good for development environment ?? is it keep nagging like noisy child when new a new scripts or executable are created?
Exactly my setupYeah spot on. OSArmor and ESET seems to make a great combo. I personally also suggest Syshardener to disable all scripts. I'm thinking of following @harlan4096 and adding sandboxie so that my browser always run sandboxed.

