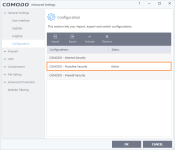
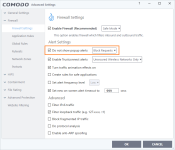
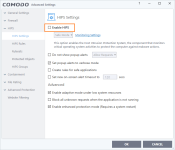
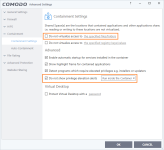
Okay, it looks like we agree on those 6 points.
I am truly surprised that you find it acceptable that any security software would allow a kernel level backdoor to be created, that also offers access to some rather dangerous tools. I am also surprised that you would not prefer to just block DP, so that the system remained uninfected... but to each their own I guess.
Keep in mind, DP was originally designed to be a backdoor spy utility that contains a lot of spy tools, but a lot of the built in tools can be used for malicious purposes.
The hacker tools I listed above can do a lot of damage and steal pretty much all of your sensitive data, just with the built in tools.
DP is already malware... but what happens when someone mods DP and transforms it into killer malware... and adds an encryptor and God knows what else? Are you going to be okay with the new variant of DP being installed? Or would you just prefer that the security software blocks DP, so that none of this happens?
I am truly surprised that you find it acceptable that any security software would allow a kernel level backdoor to be created, that also offers access to some rather dangerous tools. I am also surprised that you would not prefer to just block DP, so that the system remained uninfected... but to each their own I guess.
Keep in mind, DP was originally designed to be a backdoor spy utility that contains a lot of spy tools, but a lot of the built in tools can be used for malicious purposes.
The hacker tools I listed above can do a lot of damage and steal pretty much all of your sensitive data, just with the built in tools.
DP is already malware... but what happens when someone mods DP and transforms it into killer malware... and adds an encryptor and God knows what else? Are you going to be okay with the new variant of DP being installed? Or would you just prefer that the security software blocks DP, so that none of this happens?