Here is the first public beta of ERP v4.0 (pre-release) test 1:
http://downloads.novirusthanks.org/files/exe_radar_pro_4_setup_test1.exe
*** Please do not share the download link, we will delete it when we'll release the official v4.0 ***
This is the changelog so far (summarized):
+ Redesigned the application from scratch
+ Kernel-drivers are co-signed by MS
+ Allow to enable\disable\search\sort\categorize rules
+ Simplified the user interface
+ More detailed events that show also the triggered rule
+ Create rules grouping process fields (name, signer, cmdline, parent, etc)
+ Allow matching parent process AND child process
+ Support wildcard (? and * character) on each process field
+ Improved support for Limited User Accounts and Fast User Switching
+ Self-protection against process termination is auto-enabled
+ Only Task Manager is allowed to terminate the program
+ Improved support for Windows 10
How to handle Vulnerable Processes?
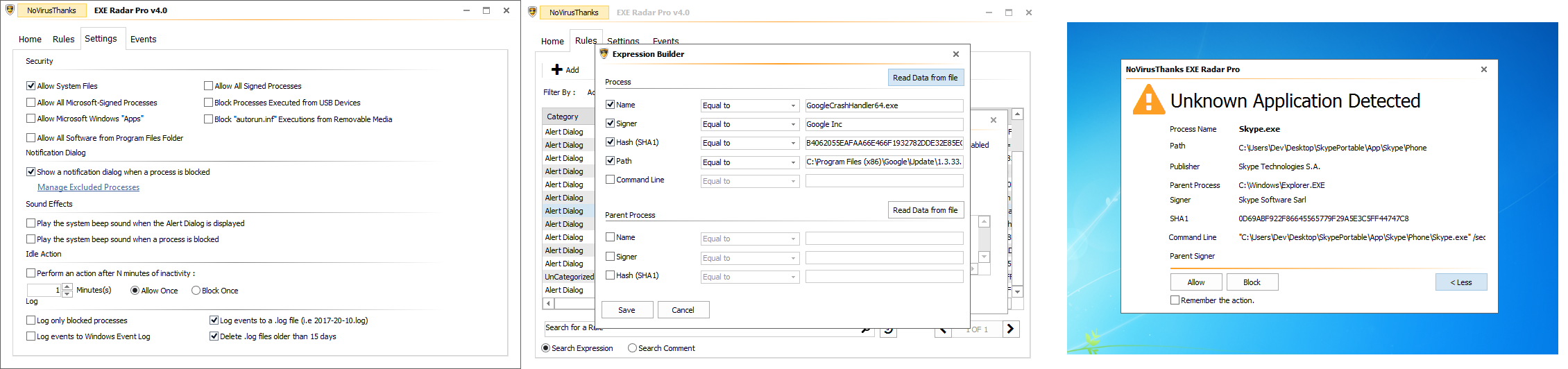
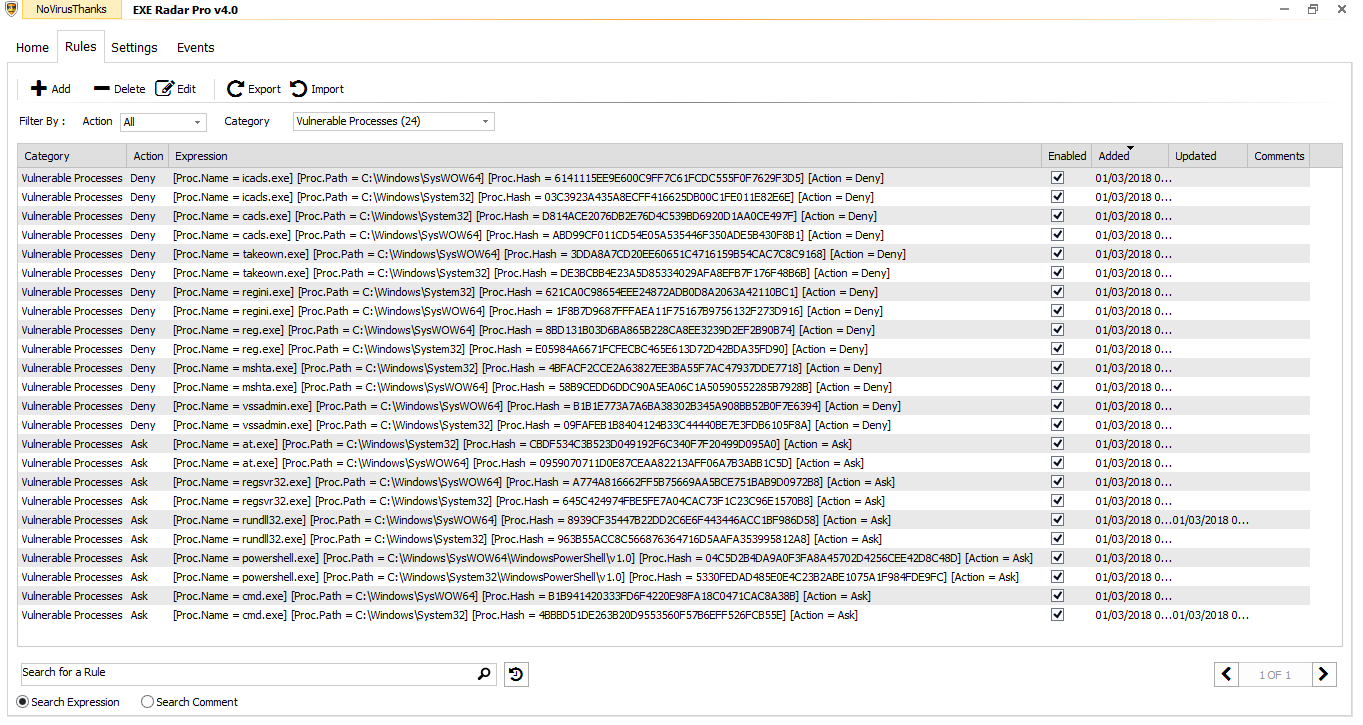
I create a new category in Rules, named like "Vulnerable Processes", and I add there all system processes commonly hijacked and misused by malware, example cmd.exe, powershell.exe, rundll32.exe, etc. I set the Action = Ask to be always notified when they are executed. Other system processes like vssadmin.exe, reg.exe, regini.exe, etc I prefer to set Action = Deny to automatically block them (I don't need them). As you can see from the screenshot below I added also the SysWOW64 versions (I'm on a 64-bit OS). To allow a vulnerable process I just create a new rule matching the process, the parent process (can be useful) and the command-line string. In some safe cases, I just match the parent process and the child (vulnerable) process, i.e C:\Program Files\Safe\Process.exe (parent) -> C:\WINDOWS\System32\cmd.exe (child), without matching the command-line.
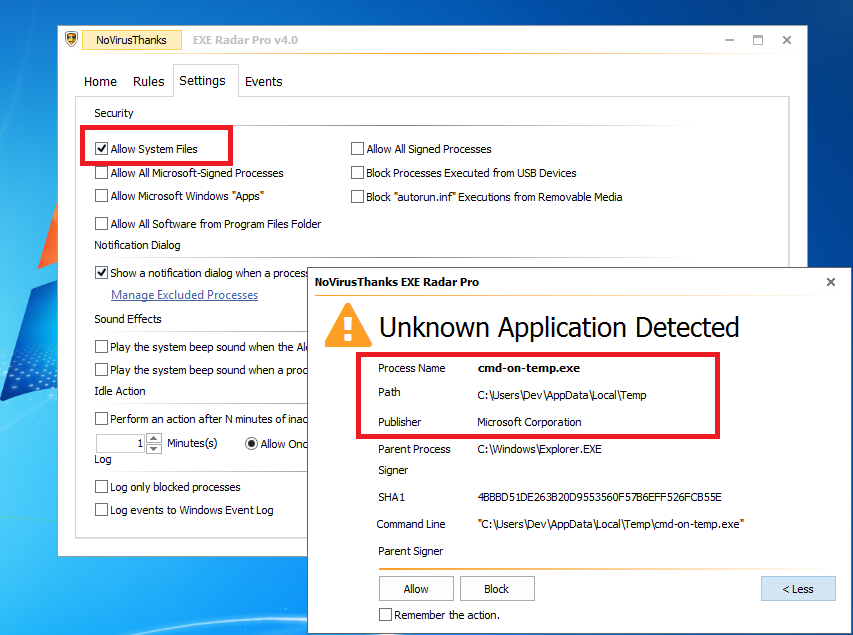
*** Probably you may avoid matching the SHA1 hash of vulnerable processes, because lets say a malware copies cmd.exe to Temp folder, then when it is executed you would get an Alert Dialog because it is not anymore a system process but is considered as an unknown process. Moreover the ones I added are not even digitally signed by MS. ***
I exported my list of vulnerable processes (made quickly, you may add some more):
http://downloads.novirusthanks.org/files/VulnerableProcesses_Rules.csv
Just click on "Rules" -> "Import" and select this CSV file to import them.
Now that rules can be categorized you can just create new categories and put your custom rules there. One important thing, if you create a rule to allow all processes on C:\WINDOWS\* then it takes precedence on the Action = Ask so all processes in C:\WINDOWS\* will be allowed (also processes with Action = Ask). This first public beta should be pretty stable and you should familiarize with it easily, it has a simple interface to create and manage rules and to check events. The settings tab has a few important and simple option. The self-protection against process termination is enabled by default and can't be changed via the settings (it is not present there as option). Only task manager can terminate EXE Radar Pro processes.
Let me know your feedback guys
http://downloads.novirusthanks.org/files/exe_radar_pro_4_setup_test1.exe
*** Please do not share the download link, we will delete it when we'll release the official v4.0 ***
This is the changelog so far (summarized):
+ Redesigned the application from scratch
+ Kernel-drivers are co-signed by MS
+ Allow to enable\disable\search\sort\categorize rules
+ Simplified the user interface
+ More detailed events that show also the triggered rule
+ Create rules grouping process fields (name, signer, cmdline, parent, etc)
+ Allow matching parent process AND child process
+ Support wildcard (? and * character) on each process field
+ Improved support for Limited User Accounts and Fast User Switching
+ Self-protection against process termination is auto-enabled
+ Only Task Manager is allowed to terminate the program
+ Improved support for Windows 10
How to handle Vulnerable Processes?
I create a new category in Rules, named like "Vulnerable Processes", and I add there all system processes commonly hijacked and misused by malware, example cmd.exe, powershell.exe, rundll32.exe, etc. I set the Action = Ask to be always notified when they are executed. Other system processes like vssadmin.exe, reg.exe, regini.exe, etc I prefer to set Action = Deny to automatically block them (I don't need them). As you can see from the screenshot below I added also the SysWOW64 versions (I'm on a 64-bit OS). To allow a vulnerable process I just create a new rule matching the process, the parent process (can be useful) and the command-line string. In some safe cases, I just match the parent process and the child (vulnerable) process, i.e C:\Program Files\Safe\Process.exe (parent) -> C:\WINDOWS\System32\cmd.exe (child), without matching the command-line.
*** Probably you may avoid matching the SHA1 hash of vulnerable processes, because lets say a malware copies cmd.exe to Temp folder, then when it is executed you would get an Alert Dialog because it is not anymore a system process but is considered as an unknown process. Moreover the ones I added are not even digitally signed by MS. ***
I exported my list of vulnerable processes (made quickly, you may add some more):
http://downloads.novirusthanks.org/files/VulnerableProcesses_Rules.csv
Just click on "Rules" -> "Import" and select this CSV file to import them.
Now that rules can be categorized you can just create new categories and put your custom rules there. One important thing, if you create a rule to allow all processes on C:\WINDOWS\* then it takes precedence on the Action = Ask so all processes in C:\WINDOWS\* will be allowed (also processes with Action = Ask). This first public beta should be pretty stable and you should familiarize with it easily, it has a simple interface to create and manage rules and to check events. The settings tab has a few important and simple option. The self-protection against process termination is enabled by default and can't be changed via the settings (it is not present there as option). Only task manager can terminate EXE Radar Pro processes.
Let me know your feedback guys
Last edited: