Exploit Shield
- Thread starter loveboy_lion
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
- Status
- Not open for further replies.
Thanks for testing!Littlebits said:I went into the forum to test the urls, the latest 120928 Exploit Kit URLs are all already blocked by Avast, most are also blocked by Google Chrome and Firefox.
Avast and Chrome are blocking those URLs by blacklisting the URL itself as those URLs are normally already 24 hours or older. One way of testing is to disable the URL blacklisting features of your other security programs so you can allow the browser to hit the exploit. Then you will see how ExploitShield behaves against exploits.
We add new URLs normally on a daily basis but mostly on a "whenever-we-get-some-spare-time" basis which is not very often.
We haven't tried it, but if you do please post your findings!InternetChicken said:Hi ZeroVulnLabs
Question Any issue with ExploitShield Browser Edition and Sandboxie ?
ExploitShield Browser Edition shields browsers and add-ons (Java, PDF, media players, Flash, Shockwave, etc.).arsenaloyal said:OK so is this only specifically for browsers or does is also block exploits in apps like MS office suite ? thanks.
ExploitShield Corporate Edition does some other things:
http://www.zerovulnerabilitylabs.com/home/exploitshield/
ok, the corporate shield looks interesting,how do i get a trial version ?
ExploitShield Corporate Edition
This product is currently in closed, private beta. Watch this page or our press releases for announcements regarding the availability of the product. To participate in the beta program please contact us from your corporate email account. Requests from non-corporate addresses will be ignored.
just saw that,too bad,.... so does this mean that its not available for personal and home use ?
It might still be a few months until we open the ExploitShield Corporate Edition beta program. Send us an email to info@ from your corporate mailbox if you want to be on the list.arsenaloyal said:just saw that,too bad,.... so does this mean that its not available for personal and home use ?
InternetChicken said:Hi ZeroVulnLabs
Question Any issue with ExploitShield Browser Edition and Sandboxie ?
i use sandboxie,but using sandboxie would make exploitshield redundant if i am not mistaken as a sandboxed browser would contain that specific exploit.... although not detect or block it.
ZeroVulnLabs said:It might still be a few months until we open the ExploitShield Corporate Edition beta program. Send us an email to info@ from your corporate mailbox if you want to be on the list.arsenaloyal said:just saw that,too bad,.... so does this mean that its not available for personal and home use ?
okies will do that the next week.
ZeroVulnLabs said:Thanks for testing!Littlebits said:I went into the forum to test the urls, the latest 120928 Exploit Kit URLs are all already blocked by Avast, most are also blocked by Google Chrome and Firefox.
Avast and Chrome are blocking those URLs by blacklisting the URL itself as those URLs are normally already 24 hours or older. One way of testing is to disable the URL blacklisting features of your other security programs so you can allow the browser to hit the exploit. Then you will see how ExploitShield behaves against exploits.
We add new URLs normally on a daily basis but mostly on a "whenever-we-get-some-spare-time" basis which is not very often.
We haven't tried it, but if you do please post your findings!InternetChicken said:Hi ZeroVulnLabs
Question Any issue with ExploitShield Browser Edition and Sandboxie ?
The main problem with Exploit Shield is it will have to offer something unique. If your browser and/or AV can already block exploits, there really isn't anything to benefit from using it. Blacklisting urls is very effective actually probably the best option instead of trying to just block the exploit in general.
Google Safe Browsing which is used in both Google Chrome and Mozilla products has a huge blocklist. Microsoft SmartScreen Filter on Internet Explorer has did huge improvements as well. Opera’s Fraud and Malware Protection is also very good. Not to mention all of the available browser extensions which can block exploits.
Unless you can provide urls with exploits not blocked by these other means and can be blocked by Exploit Shield, there really is no proof that it will be beneficial to users.
Good day.
Google Safe Browsing which is used in both Google Chrome and Mozilla products has a huge blocklist. Microsoft SmartScreen Filter on Internet Explorer has did huge improvements as well. Opera’s Fraud and Malware Protection is also very good. Not to mention all of the available browser extensions which can block exploits.
Unless you can provide urls with exploits not blocked by these other means and can be blocked by Exploit Shield, there really is no proof that it will be beneficial to users.
Well Littlebits has put the brick through the window with that one :+1:
having that issue with firefox, had to turn off everything in the security tab and disable all securiry and privacy addons
then went malware hunting , to see it I could get a hit out of Exploit Shield , and no not a peep ,,
:s:s
Unless you can provide urls with exploits not blocked by these other means and can be blocked by Exploit Shield, there really is no proof that it will be beneficial to users.
Well Littlebits has put the brick through the window with that one :+1:
having that issue with firefox, had to turn off everything in the security tab and disable all securiry and privacy addons
then went malware hunting , to see it I could get a hit out of Exploit Shield , and no not a peep ,,
:s:s
You are mistaken. Neither AV nor browser provides exploit blocking. They provide blacklisting-based URL blocking, which is extremely different. Confusing both would be a big mistake. Blacklisting relies on previous knowledge and analysis of a URL's maliciousness before it is added to the blacklist. This means a few patient zero infections, time wasted on the URL discovery, time wasted on the URL analysis and time wasted on the blacklisting signature being published.Littlebits said:The main problem with Exploit Shield is it will have to offer something unique. If your browser and/or AV can already block exploits, there really isn't anything to benefit from using it.
EDIT: it's actually very easy to test if you keep a watch out on MDL or similar sites for new "exploit kit" URLs being published. Als you can use metasploit to test the same exploits that exploit kits such as Blackhole use.
madyrocksin said:just a question, why it needs internet connection using svchost??
I think my question got unnoticed
It shouldn't use svchost.exe for any connectivity. Can you please PM me the details of why you think it does?madyrocksin said:I think my question got unnoticed
ZeroVulnLabs said:You are mistaken. Neither AV nor browser provides exploit blocking. They provide blacklisting-based URL blocking, which is extremely different. Confusing both would be a big mistake. Blacklisting relies on previous knowledge and analysis of a URL's maliciousness before it is added to the blacklist. This means a few patient zero infections, time wasted on the URL discovery, time wasted on the URL analysis and time wasted on the blacklisting signature being published.Littlebits said:The main problem with Exploit Shield is it will have to offer something unique. If your browser and/or AV can already block exploits, there really isn't anything to benefit from using it.
EDIT: it's actually very easy to test if you keep a watch out on MDL or similar sites for new "exploit kit" URLs being published. Als you can use metasploit to test the same exploits that exploit kits such as Blackhole use.
Well here is another problem, if an advanced user can not find a zero day exploit on a webpage when browsing then what are the odds that a novice user might accidentally visit that site?
Many of the urls on MDL only have direct links to the download not the website from where the files came from. It is unknown if they even exists in the wild other than listed on MDL. Another problem, MDL has a lot of false positives, the malware is not verified. I have download files from there before that were harmless files digitally signed by trusted vendors like Microsoft. I even executed them and they were programs like Microsoft Calculator, Microsoft Games and other trusted programs. A full scan with several scanners revealed no infections after running them. The exe's were renamed to make them look dangerous.
It makes me wonder if users upload the malware links to create paranoia.
So I don't personally trust MDL. Google Chrome and Firefox usually blocks the latest urls anyway. Others are blocked by Avast, I just check the most recent and all are already blocked.
It makes no difference how the exploits get blocked as long as they are blocked. If the website link can not load then exploit can not function.
And yes browsers do have extensions that can disable flash, Java, scripts, iFrames, etc. and provide exploit protection.
Thanks.
Actually advanced users are less likely to encounter an exploit which bypasses protection since they usually have much more updated software components (less vulnerabilities) and many more security layers.Littlebits said:Well here is another problem, if an advanced user can not find a zero day exploit on a webpage when browsing then what are the odds that a novice user might accidentally visit that site?
Wow, you would think that being in a forum where security-conscious users constantly upload undetected malware and malicious URLs which have low detection by traditional blacklisting security would know better. Ironic isn't it.Littlebits said:It makes me wonder if users upload the malware links to create paranoia.
Those are not anti-exploit techniques, those are feature/functionality limitations and the vast majority of regular, non computer saavy users, don't use them because they are not install-and-forget.Littlebits said:And yes browsers do have extensions that can disable flash, Java, scripts, iFrames, etc. and provide exploit protection.
I can actually forsee something like this replacing antivirus,the one that protects from app based exploits not just browserbased, just add to this whitelisting capabilities and you will not need an antivirus !
Most of the windows based malware these days are from 3rd party based exploits.
Most of the windows based malware these days are from 3rd party based exploits.
Regarding testing with live URLs, we've added a "tips for testing exploit kits" post:
http://www.zerovulnerabilitylabs.com/forum/viewtopic.php?f=14&t=49
Also the latest entry of URLs (121002 Exploit Kit URLs) is the sum total of all active URLs that we have, instead of only the incremental. So you can see quite a lot of URLs here for testing a variety of different exploits, although most of them are Blackhole EK 2.0.
http://www.zerovulnerabilitylabs.com/forum/viewtopic.php?f=14&t=49
Also the latest entry of URLs (121002 Exploit Kit URLs) is the sum total of all active URLs that we have, instead of only the incremental. So you can see quite a lot of URLs here for testing a variety of different exploits, although most of them are Blackhole EK 2.0.
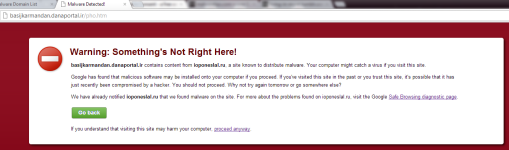
Found link on MDL:
[attachment=2454]
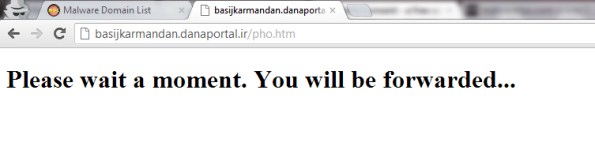
Paste & Go link into Chrome:
[attachment=2455]
Proceed anyway (1st & 2nd attempt at link showed Chrome: Do you want to install a missing plugin, ie. Java):
[attachment=2456]
PS: This is not a test. I do not have Java installed, but even I were to have Java installed, Google Safe Browsing would have stopped me.
It is an interesting idea, but what about using Secunia PSI to keep software updated to prevent most exploits from occurring?
Is ExploitShield targeted at more for Corporate environments rather than general consumer users? And would ExploitShield protect Mac and Linux users too, say in a future release?
I'm still unsure if I should try ExploitShield. :huh:
[attachment=2454]
Paste & Go link into Chrome:
[attachment=2455]
Proceed anyway (1st & 2nd attempt at link showed Chrome: Do you want to install a missing plugin, ie. Java):
[attachment=2456]
PS: This is not a test. I do not have Java installed, but even I were to have Java installed, Google Safe Browsing would have stopped me.
It is an interesting idea, but what about using Secunia PSI to keep software updated to prevent most exploits from occurring?
Is ExploitShield targeted at more for Corporate environments rather than general consumer users? And would ExploitShield protect Mac and Linux users too, say in a future release?
I'm still unsure if I should try ExploitShield. :huh:
Attachments
Yes you should use Secunia or something similar to keep all your software up-to-date and also an up-to-date AV to reduce the infection risk. ExploitShield is by no means a replacement for keeping your software up-to-date.Earth said:It is an interesting idea, but what about using Secunia PSI to keep software updated to prevent most exploits from occurring?
Is ExploitShield targeted at more for Corporate environments rather than general consumer users? And would ExploitShield protect Mac and Linux users too, say in a future release?
However there are 0-day exploits out there that exploit fully patched and fully up-to-date systems. This is not uncommon at all. Remember the handfull of Internet Explorer and Java zero-day vulnerabilities lately?
Also you might be an advanced users, but regular users don't use Secunia, NoScript and those type of things, and are at a much higher risk of infection.
ExploitShield could be beneficial to users who don't use browser extensions, have disabled their browser protection features or ignore warnings, don't keep their software updated and don't have a good AV installed and updated.
Otherwise users who are more aware of keeping their software updated, using their browser protection features and added extensions plus a good AV, probably would not benefit from using ExploitShield.
Like I said, I have everything updated and my browsers and Avast blocked all of the MLD links. I couldn't find one single exploit that could successfully function after searching all over the web.
Good day.
Otherwise users who are more aware of keeping their software updated, using their browser protection features and added extensions plus a good AV, probably would not benefit from using ExploitShield.
Like I said, I have everything updated and my browsers and Avast blocked all of the MLD links. I couldn't find one single exploit that could successfully function after searching all over the web.
Good day.
the problem with traditional AV's is the same it relies on blacklisting,perhaps this version of expoitshield (only browser based) might be blocked by AV,but actual application based exploits are rarely blocked or even detected by traditional AV's.
from my point of view a software like this could actually replace a traditional AV if its coupled with something like an antiexecutable! and perhaps if they throw something like an auto updater for all the softwares on your PC (something like secunia and more recently vipre 2013 !) then i would seriously give them a chance and something worth keeping an eye out for !
from my point of view a software like this could actually replace a traditional AV if its coupled with something like an antiexecutable! and perhaps if they throw something like an auto updater for all the softwares on your PC (something like secunia and more recently vipre 2013 !) then i would seriously give them a chance and something worth keeping an eye out for !
- Status
- Not open for further replies.
You may also like...
-
Security News Hackers Exploiting PDF24 App to Deploy Stealthy PDFSIDER Backdoor
- Started by Brownie2019
- Replies: 1
-
New Update Apple Issues Security Updates After Two WebKit Flaws Found Exploited in the Wild
- Started by Gandalf_The_Grey
- Replies: 2
-
Malware News CrashFix Chrome Extension Delivers ModeloRAT Using ClickFix-Style Browser Crash Lures
- Started by Parkinsond
- Replies: 2
-
A.I. News Gartner: All AI Browsers Should be Blocked for Foreseeable Future
- Started by Gandalf_The_Grey
- Replies: 5