Quote : In a day, we see about 7 billion events, 6 billion online reputation queries, 1 million suspicious URLs, 500 000 samples for analysis, and around 10 000 new malware. Endpoint protection solutions have transformed over the years. Early protection solutions employed anti-virus scanners designed to detect malware in files by checking for simple signatures stored in a local database. By 2006, this approach started to dwindle in effectiveness due to the rise in server-side polymorphic malware. The signature approach of yesteryears was easy to defeat; it was trivial to test samples against a scan engine and modify them until they were no longer detected.
The traditional file scanning approach is still in use in most endpoint protection solutions to this day as part of a wider toolset of protection technologies. Scanning engines have evolved to augment the simple signature approach with more complex detection logic based on parsers, disassemblers, and emulators. File scanning engines can still be an effective tool against the everexpanding pool of known threats. Nowadays, they are even optimized for speed, and is the remaining protection layer when no network connection is available on the local device.
Modern endpoint protection suites employ a multilayered approach to providing security. Technologies such as network filtering and scanning, behavioral analysis, and URL filtering augment traditional file scanning components. These different protection features are built into F-Secure Ultralight in a multilayered design, so that if a threat escapes one layer, there is still another layer that can catch it. And as the threat landscape changes, some layers may be removed or new ones may be added both in the endpoints and in the F-Secure Security Cloud.

What is F-Secure Ultralight?
Ultralight is an all-in-one package that contains F-Secure’s full endpoint protection stack. Ultralight provides a new, modern take on protecting devices in an intelligent and proactive way against the threats we see in the real world. It represents a fundamental breakthrough, not only in the way we protect our customers, but also in the way we work here at F-Secure. With the introduction of Ultralight, we have gained a wealth of new possibilities for protecting our customers now and in the future. Ultralight fully leverages the intelligence of F-Secure’s Security Cloud at the endpoint. Security Cloud is a threat analysis and repository system operated by F-Secure Corporation that provides a wide range of services to security products. Unlike traditional anti-virus solutions that receive periodic database updates and can go hours or days before they are protected against new threats, Ultralight’s direct connection to F-Secure’s cloud provides minute-to-minute protection for all users.
How does Ultralight work?
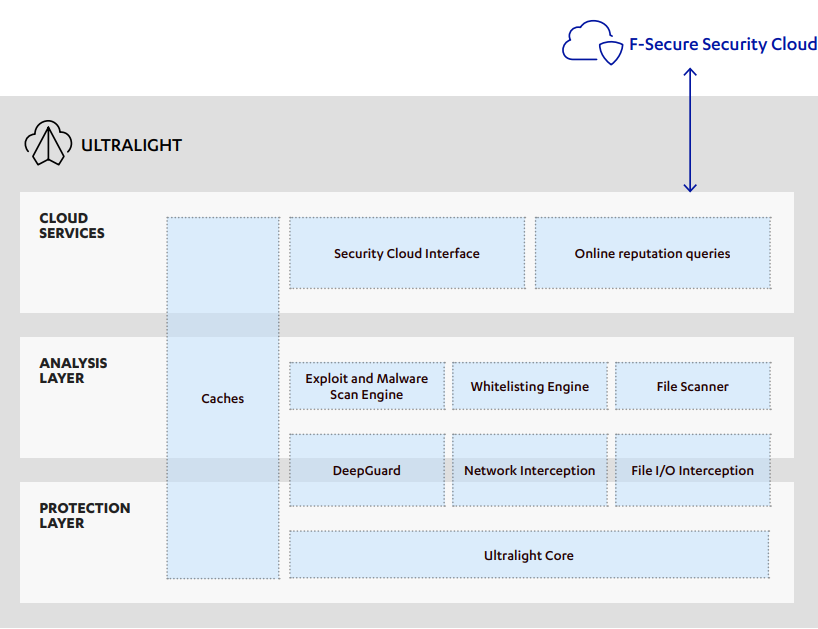
Ultralight combines all of the technologies present in F-Secure’s full endpoint protection stack into a single package. It consists of a number of drivers, engines, and system services that provide mechanisms to protect both a device and its users. Ultralight provides traditional anti-virus functionality, such as real-time file scanning and network scanning. In addition, it includes modern, proactive protection technologies that aim to stop zeroday exploits and stay ahead of new attacks. F-Secure’s Security Cloud provides Ultralight components with realtime information as the threat landscape changes.

Overview of the components that make up Ultralight.
Ultralight Core
Ultralight Core consists of a set of components including a driver (Gatekeeper) responsible for filesystem interception and a set of services and components that host all other Ultralight technologies. In addition, it provides a common communication layer between all components, performance optimization mechanisms, and several basic protection services. As the name suggests, Ultralight Core supplies all the underpinnings required for Ultralight’s technology stack to run.
Network Interception Framework (NIF)
Our Network Interception Framework is responsible for analyzing network traffic. It is used primarily to prevent exploit technologies from working and to prevent bots from connecting to command and control infrastructure.
Full whitepaper :

 blog.f-secure.com
blog.f-secure.com
The traditional file scanning approach is still in use in most endpoint protection solutions to this day as part of a wider toolset of protection technologies. Scanning engines have evolved to augment the simple signature approach with more complex detection logic based on parsers, disassemblers, and emulators. File scanning engines can still be an effective tool against the everexpanding pool of known threats. Nowadays, they are even optimized for speed, and is the remaining protection layer when no network connection is available on the local device.
Modern endpoint protection suites employ a multilayered approach to providing security. Technologies such as network filtering and scanning, behavioral analysis, and URL filtering augment traditional file scanning components. These different protection features are built into F-Secure Ultralight in a multilayered design, so that if a threat escapes one layer, there is still another layer that can catch it. And as the threat landscape changes, some layers may be removed or new ones may be added both in the endpoints and in the F-Secure Security Cloud.

What is F-Secure Ultralight?
Ultralight is an all-in-one package that contains F-Secure’s full endpoint protection stack. Ultralight provides a new, modern take on protecting devices in an intelligent and proactive way against the threats we see in the real world. It represents a fundamental breakthrough, not only in the way we protect our customers, but also in the way we work here at F-Secure. With the introduction of Ultralight, we have gained a wealth of new possibilities for protecting our customers now and in the future. Ultralight fully leverages the intelligence of F-Secure’s Security Cloud at the endpoint. Security Cloud is a threat analysis and repository system operated by F-Secure Corporation that provides a wide range of services to security products. Unlike traditional anti-virus solutions that receive periodic database updates and can go hours or days before they are protected against new threats, Ultralight’s direct connection to F-Secure’s cloud provides minute-to-minute protection for all users.
How does Ultralight work?
Ultralight combines all of the technologies present in F-Secure’s full endpoint protection stack into a single package. It consists of a number of drivers, engines, and system services that provide mechanisms to protect both a device and its users. Ultralight provides traditional anti-virus functionality, such as real-time file scanning and network scanning. In addition, it includes modern, proactive protection technologies that aim to stop zeroday exploits and stay ahead of new attacks. F-Secure’s Security Cloud provides Ultralight components with realtime information as the threat landscape changes.

Overview of the components that make up Ultralight.
Ultralight Core
Ultralight Core consists of a set of components including a driver (Gatekeeper) responsible for filesystem interception and a set of services and components that host all other Ultralight technologies. In addition, it provides a common communication layer between all components, performance optimization mechanisms, and several basic protection services. As the name suggests, Ultralight Core supplies all the underpinnings required for Ultralight’s technology stack to run.
Network Interception Framework (NIF)
Our Network Interception Framework is responsible for analyzing network traffic. It is used primarily to prevent exploit technologies from working and to prevent bots from connecting to command and control infrastructure.
- Utilizes cloud URL reputation queries to prevent a customer machine from contacting malicious or compromised sites.
- Prevents unknown sites from serving Flash, Java, Silverlight, or PDF files (exploit kits and other attack servers commonly use totally unknown fresh domains).
- Scans network traffic for exploits and known malware.
- Detects and blocks SSL MITM attacks performed by invasive governments by using SSL certificate reputation and analysis.
- Rapid detection of new exploit kit hosting sites via co-operation with Security Cloud and URL reputation rapid feedback mechanisms.
- Prevents known botnet command and control domains from working by querying URL reputation before allowing the DNS query.
- Facilitates banking protection functionality by isolating only trusted content during a banking session.
- Prevents users from accessing webpages associated with malicious certificates.
- Prevents users from accessing unwanted or disturbing content.
- Exploit and malware scan engine
- F-Secure’s advanced scan engine. It is primarily used for exploit detection, file scanning and memory scanning.
- Detects malware from active process memory.
- Detects exploits and exploit kits.
- Detects prevalent malware and attack scripts.
- Detects on-the-wire exploits and malware (via NIF).
- Identifies file types.
- Provides several parsers for file formats commonly used by malware.
- Provides file unpackers and de-obfuscators.
- Provides archive traversal mechanisms

Full whitepaper :

Useful online security tips and articles | F‑Secure
True cyber security combines advanced technology and best practice. Get tips and read articles on how to take your online security even further.