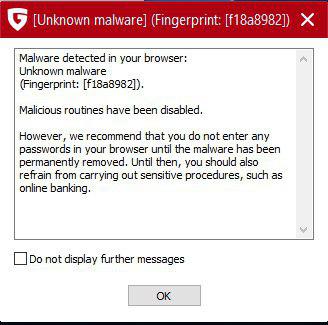
Hey guys,
Today I was a bit a free and decided to give G DATA a test..Got on hands a Dangerous Banking Trojan from an Ikarus Analyst which is just 1-2 hrs old.. VT scan attached (Ikarus came up a bit closer detection name). Bitdefender missed it and so its friends, however G DATA gave me back a Surprise Kick ..)
Verdict: It indeed caught it pro actively (Unknown Malware)..BB triggered and so the BankGuard as well asked a restart which took 15 min> ..with a clean disinfection...Sexy isn't it..)
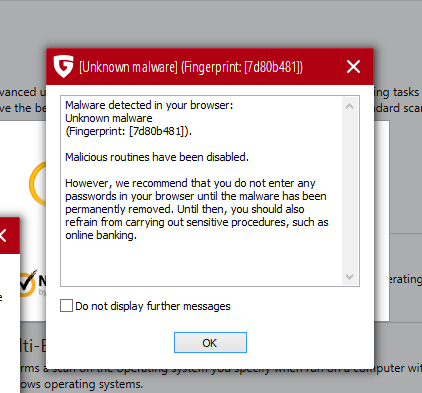
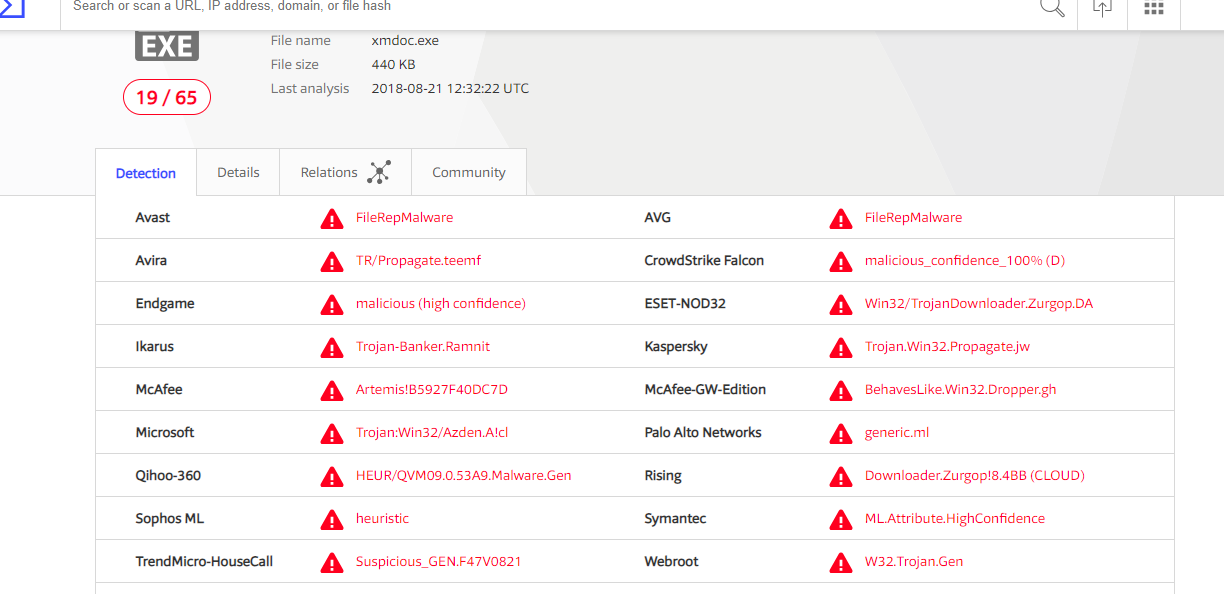
Today I was a bit a free and decided to give G DATA a test..Got on hands a Dangerous Banking Trojan from an Ikarus Analyst which is just 1-2 hrs old.. VT scan attached (Ikarus came up a bit closer detection name). Bitdefender missed it and so its friends, however G DATA gave me back a Surprise Kick ..)
Verdict: It indeed caught it pro actively (Unknown Malware)..BB triggered and so the BankGuard as well asked a restart which took 15 min> ..with a clean disinfection...Sexy isn't it..)
Last edited by a moderator: