Google has begun integrating Gemini Nano, its on-device large language model (LLM), into the latest version of the Chrome browser to combat online spam, scams and phishing campaigns.
As it released its latest version of its browser, Chrome 137, Google announced that it was experimenting with the on-device LLM as an additional layer of protection in the Enhanced Protection mode of the new browser version’s Safe Browsing service.
Chrome's Enhanced Protection mode is the highest level of Google Safe Browsing and the company claims it provides twice the safeguard against phishing and scams compared to Standard Protection mode.
While the use of Gemini Nano is currently restricted to combating tech support scams on Chrome desktop, Google plans to expand this feature to detect other types of scams, including package tracking and unpaid toll scams.
The feature is also expected to be rolled out to Chrome on Android later in 2025.
Gemini Nano to Combat Tech Support Scams
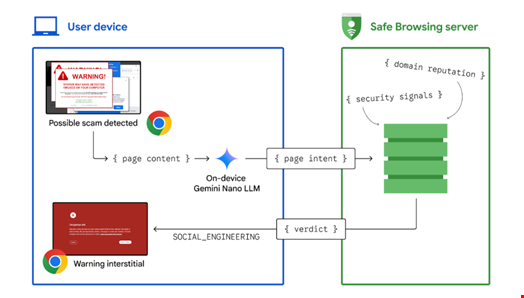
Using Gemini Nano in the Chrome Safe Browsing service leverages the LLM to generate signals that are used by Safe Browsing to deliver higher-confidence verdicts about potentially dangerous sites, such as tech support scams.
When a user visits a potentially malicious page, Chrome's on-device Gemini Nano LLM evaluates the page's content to extract security signals, such as intent. This information is sent to Safe Browsing, which makes a final determination on whether the page is a scam. If deemed a threat, Chrome displays a warning.
The process is designed to preserve performance and privacy. The LLM is triggered sparingly and runs locally on the device, with resource consumption carefully managed.
Overview of how on-device LLM assistance scam mitigation works. Source: Google
Only users with Enhanced Protection mode enabled have their LLM-generated security signals sent to Safe Browsing, while Standard Protection users benefit indirectly from updated blocklists.
Jasika Bawa, Google’s Group Product Manager for Chrome and Phiroze Parakh, Senior Director for Engineering at Google Search, commented in
a public statement on May 8: “Gemini Nano's LLM is perfect for this use because of its ability to distill the varied, complex nature of websites, helping us adapt to new scam tactics more quickly.”
Benefits of Running On-Device LLM
According to
a more detailed report on the Google Security blog, leveraging LLMs on-device has several benefits, aside from being less demanding than hosting the LLM remotely.
First, this feature, when running locally, enables Google to detect threats when users encounter them.
“We’ve found that the average malicious site exists for less than 10 minutes, so on-device protection allows us to detect and block attacks that haven't been crawled before,” the Google Chrome Security team wrote.
“The on-device approach also empowers us to see threats
the way users see them. Sites can render themselves differently for different users, often for legitimate purposes (e.g. to account for device differences, offer personalization, provide time-sensitive content), but sometimes for illegitimate purposes (e.g. to evade security crawlers) – as such, having visibility into how sites are presenting themselves to real users enhances our ability to assess the web.”
Alongside this announcement, Google is also launching
new AI-powered warnings for Chrome on Android.
When the on-device machine learning model flags a notification, users will receive a warning that allows them to unsubscribe or view the blocked content. It also provides an option to enable future notifications from the website if users believe the warning was incorrect.
These features follow Google's introduction of
AI-powered scam detection in the Android Messages app just over two months ago, as well as its unveiling of scam call flagging capabilities last year.
Google’s Fighting Scams in Search Report
Finally, Google launched its latest
Fighting Scams in Search report on May 8.
In this document, the company asserts that the investments the company has made in its AI-powered scam detection systems and improvements to its classifiers have enabled it to catch 20 times more scammy pages than before.
Google also stated that it has observed a significant increase in scammers impersonating airline customer service providers and claims to have successfully reduced such scams by over 80% in its search results.

 chromereleases.googleblog.com
chromereleases.googleblog.com