Hello again icotonev,
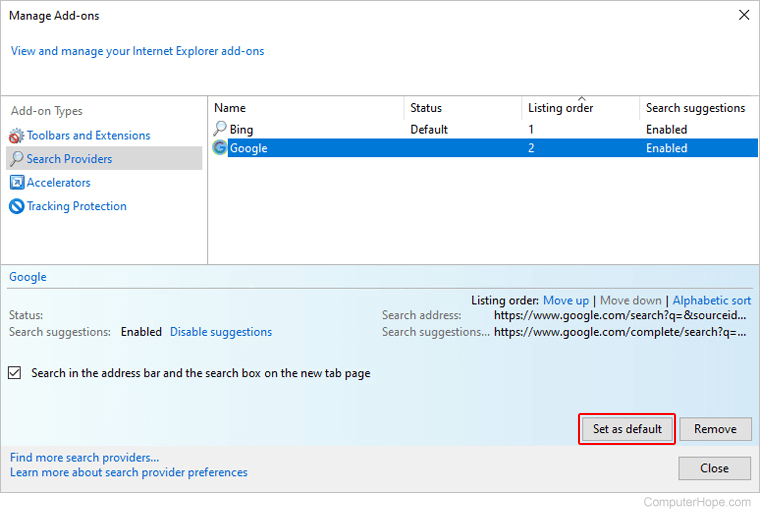
unfortunately I still get redirected, so here are the results from the FMRS log
# ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~ #
# Furtivex Malware Removal Script v5.5.4
#
Furtivex – Furtivex Computer Solutions
# Microsoft Windows 11 Home x64 24H2 0407 // 1252 // 65001
# 2025_02_09__19_28_04 - nicol -
# ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~ #
# Abläufe:
# Treiber:
# Dienste:
# Dateien:
C:\ProgramData\SEC9167.tmp
C:\ProgramData\SECA090.tmp
C:\Users\nicol\AppData\Local\Google\Chrome\User Data\Default\Cache\Cache_Data (507)
C:\Users\nicol\AppData\Local\Google\Chrome\User Data\Default\Code Cache\js (2437)
C:\Users\nicol\AppData\Local\Microsoft\Edge\User Data\Default\Cache\Cache_Data (19)
C:\Users\nicol\AppData\Local\Microsoft\Edge\User Data\Default\Code Cache\js (255)
C:\Users\nicol\AppData\Local\Tempwd.tmp
C:\Users\nicol\AppData\LocalLow\Sun\Java\Deployment\cache (0)
C:\WINDOWS\System32\config\systemprofile\AppData\Local\CM297CE.tmp
C:\WINDOWS\System32\config\systemprofile\AppData\Local\CM2CA4F.tmp
C:\WINDOWS\System32\config\systemprofile\AppData\Local\CM2CB3E.tmp
C:\WINDOWS\System32\config\systemprofile\AppData\Local\CM2DC0.tmp
C:\WINDOWS\System32\config\systemprofile\AppData\Local\tw-694-3e60-c58845.tmp
# Ordner:
C:\Users\nicol\AppData\Local\D3DSCache (39)
C:\Users\nicol\AppData\Local\Microsoft\Windows\INetCache\IE (4)
C:\WINDOWS\ServiceProfiles\LocalService\AppData\Local\D3DSCache (2)
C:\WINDOWS\System32\config\systemprofile\AppData\Local (2198)
C:\WINDOWS\System32\config\systemprofile\AppData\Local\D3DSCache (9)
# Aufgaben:
# Registrierung:
HKLM\Software\Policies\Mozilla\Firefox
HKLM\Software\Microsoft\Tracing\HPWarrantyChecker_RASAPI32
HKLM\Software\Microsoft\Tracing\HPWarrantyChecker_RASMANCS
HKLM\Software\Microsoft\Tracing\SolutionFinder_RASAPI32
HKLM\Software\Microsoft\Tracing\SolutionFinder_RASMANCS
HKLM\Software\Microsoft\Tracing\Squirrel_RASAPI32
HKLM\Software\Microsoft\Tracing\Squirrel_RASMANCS
HKLM\Software\Microsoft\Tracing\Update_RASAPI32
HKLM\Software\Microsoft\Tracing\Update_RASMANCS
HKCU\Software\Microsoft\Windows\CurrentVersion\ContentDeliveryManager\\SubscribedContent-338388Enabled
HKCU\Software\Microsoft\Windows\CurrentVersion\ContentDeliveryManager\\SubscribedContent-338389Enabled
HKCU\Software\Microsoft\Windows\CurrentVersion\ContentDeliveryManager\\SubscribedContent-88000326Enabled
HKCU\Software\Microsoft\Windows\CurrentVersion\Run\\CiscoMeetingDaemon
HKCU\Software\Microsoft\Windows\CurrentVersion\Run\\com.squirrel.Teams.Teams
HKCU\Software\Microsoft\Windows\CurrentVersion\Run\\HPSEU_Host_Launcher
HKCU\Software\Microsoft\Windows\CurrentVersion\Run\\MicrosoftEdgeAutoLaunch_B9B257C7C4ABB38D87EB5195476F971F
HKLM\System\CurrentControlSet\Control\CrashControl\\AutoReboot [1] => [0]
# Verschiedenes:
AntiVirus Software: Avast
AntiVirus Software: Malwarebytes
AntiVirus Software: McAfee
AntiVirus Software: Windows Defender
Wiederherstellungspunkt: Furtivex Malware Removal Script - Erstellt
HKLM\Software\Microsoft\Windows Defender\Exclusions\Extensions
HKLM\Software\Microsoft\Windows Defender\Exclusions\IpAddresses
HKLM\Software\Microsoft\Windows Defender\Exclusions\Paths
HKLM\Software\Microsoft\Windows Defender\Exclusions\Processes
HKLM\Software\Microsoft\Windows Defender\Exclusions\TemporaryPaths
C:\Users\nicol\AppData\Local\CrashDumps\click_and_teach.exe.12476.dmp
C:\Users\nicol\AppData\Local\CrashDumps\click_and_teach.exe.13228.dmp
C:\Users\nicol\AppData\Local\CrashDumps\click_and_teach.exe.13464.dmp
C:\Users\nicol\AppData\Local\CrashDumps\click_and_teach.exe.13860.dmp
C:\Users\nicol\AppData\Local\CrashDumps\click_and_teach.exe.1416.dmp
C:\Users\nicol\AppData\Local\CrashDumps\click_and_teach.exe.14784.dmp
C:\Users\nicol\AppData\Local\CrashDumps\click_and_teach.exe.17288.dmp
C:\Users\nicol\AppData\Local\CrashDumps\click_and_teach.exe.4796.dmp
C:\Users\nicol\AppData\Local\CrashDumps\ctfmon.exe.10260.dmp
C:\Users\nicol\AppData\Local\CrashDumps\slicer.exe.6380.dmp
C:\WINDOWS\System32\config\systemprofile\AppData\Local\CrashDumps\iprntsrv.exe.5760.dmp
C:\WINDOWS\System32\config\systemprofile\AppData\Local\CrashDumps\iprntsrv.exe.7480.dmp
C:\FRST\Quarantine\C\Program Files\HitmanPro\HitmanPro.exe
C:\FRST\Quarantine\C\Program Files\HitmanPro\hmpsched.exe
C:\FRST\Quarantine\C\ProgramData\HitmanPro\HitmanPro.key
C:\FRST\Quarantine\C\ProgramData\HitmanPro\HitmanPro.lic
C:\FRST\Quarantine\C\ProgramData\HitmanPro\Remnants.bin
C:\FRST\Quarantine\C\ProgramData\HitmanPro\Logs\HitmanPro_20250209_0636.log
C:\FRST\Quarantine\C\ProgramData\HitmanPro\Logs\HitmanPro_20250209_1559.log
C:\FRST\Quarantine\C\ProgramData\HitmanPro\Quarantine\quarantine.xml
C:\FRST\Quarantine\C\ProgramData\Microsoft\Windows\Start Menu\Programs\HitmanPro\HitmanPro 3.8 entfernen.lnk
C:\FRST\Quarantine\C\ProgramData\Microsoft\Windows\Start Menu\Programs\HitmanPro\HitmanPro.lnk
C:\FRST\Quarantine\C\Users\nicol\Downloads\HitmanPro_x64.exe.xBAD
C:\FRST\Quarantine\C\WINDOWS\System32\Tasks\HPDataRetriever.xBAD
C:\FRST\Quarantine\C\WINDOWS\System32\Tasks\HPSupportTool.xBAD
C:\FRST\Quarantine\C\WINDOWS\System32\Tasks\Opera scheduled Autoupdate 1612079694.xBAD
C:\FRST\Quarantine\C\WINDOWS\System32\Tasks\Microsoft\Windows\Location\Notifications.xBAD
C:\FRST\Quarantine\C\WINDOWS\System32\Tasks\Microsoft\Windows\Mobile Broadband Accounts\MNO Metadata Parser.xBAD
C:\FRST\Quarantine\C\WINDOWS\System32\Tasks\Microsoft\Windows\UpdateOrchestrator\MusUx_LogonUpdateResults.xBAD
C:\FRST\Quarantine\C\WINDOWS\System32\Tasks\Microsoft\Windows\UpdateOrchestrator\MusUx_UpdateInterval.xBAD
C:\FRST\Quarantine\C\WINDOWS\System32\Tasks\Microsoft\Windows\UpdateOrchestrator\Reboot_AC.xBAD
C:\FRST\Quarantine\C\WINDOWS\System32\Tasks\Microsoft\Windows\UpdateOrchestrator\Reboot_Battery.xBAD
C:\FRST\Quarantine\C\WINDOWS\System32\Tasks\Microsoft\Windows\UpdateOrchestrator\USO_UxBroker.xBAD
# ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~ #
The FRST logs are once again attached.
Thanks for your quick and easy to understand responses!