silversurfer
Super Moderator
Thread author
Verified
Top Poster
Staff Member
Malware Hunter
Forum Veteran
- Aug 17, 2014
- 12,746
- 123,924
- 8,399
An APT hacking group known as "Dragon Breath," "Golden Eye Dog," or "APT-Q-27" is demonstrating a new trend of using several complex variations of the classic DLL sideloading technique to evade detection.
These attack variations begin with an initial vector that leverages a clean application, most often Telegram, that sideloads a second-stage payload, sometimes also clean, which in turn, sideloads a malicious malware loader DLL.
The lure for victims is trojanized Telegram, LetsVPN, or WhatsApp apps for Android, iOS, or Windows that have been supposedly localized for people in China. The trojanized apps are believed to be promoted using BlackSEO or malvertizing.
According to Sophos analysts who followed the threat actor's recent attacks, the targeting scope of this campaign is focused on Chinese-speaking Windows users in China, Japan, Taiwan, Singapore, Hong Kong, and the Philippines.
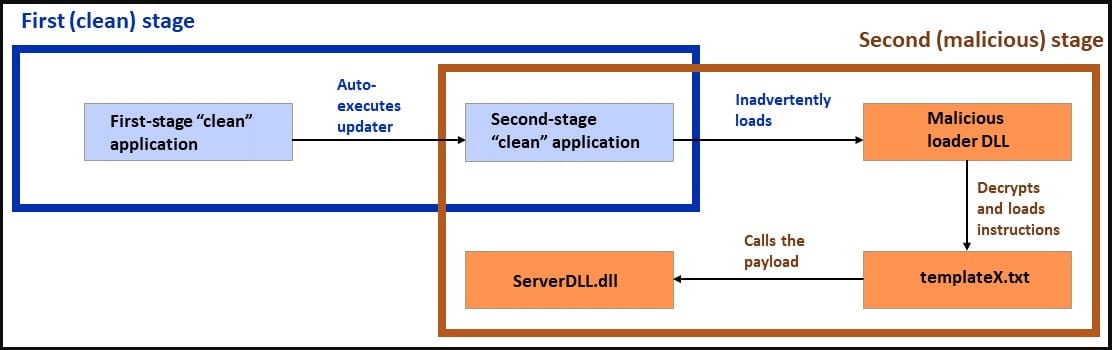
General attack diagram (Sophos)
Full report published by Sophos:

A doubled “Dragon Breath” adds new air to DLL sideloading attacks
Exploits of the venerable vulnerability gain in complexity
news.sophos.com
