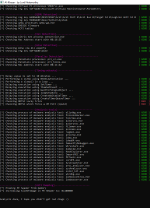
- Containment: VirtualBox 5.1.38
- Windows: 10 LTSB
- VPN: CyberGhost
- Product: Windows SmartScreen (activated by Hard_Configurator with recommended SRP and restrictions)
- Office: LibreOffice (standard settings)
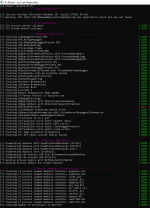
| February 2019 | Amount of samples | Samples that have harmed the system/ changed system configuration | Files aren't touched/encrypted | Thread link |
|---|---|---|---|---|
| Mixed Threats #13 (01/02/2019) | 13 | 0 | yes | link |
| #CDC Ransomware (almost FUD) - 02/02/2019 | 1 | 0 | yes | link |
| #Exploit (03/02/2019) | 1 | 0 | yes | link |
| 4/02/2019 #18 | 18 | 0 | yes | link |
| AZORult (5/02/2019) | 1 | 0 | yes | link |
| #Buhtrap Ransomware (signed) - 07/02/2019 | 1 | 1 | no | link |
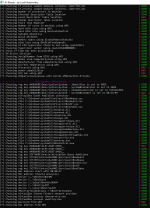
| 8/02/2019 #15 | 15 | 0 | yes | link |
| #FCrypt Ransomware | 1 | 0 | yes | link |
| AgentTesla (11/02/2019) | 1 | 0 | yes | link |
| 12/02/2019 #23 | 23 | 0 | yes | link |
| Malware Big Pack #24 (13/02/2019) | 24 | 0 | yes | link |
| Remcos RAT (14/02/2019) | 1 | 0 | yes | link |
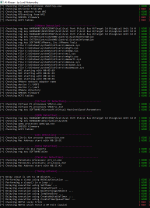
| Malware x4 (16/02/2019) | 4 | 0 | yes | link |
| 18/02/2019 #17 | 17 | 0 | yes | link |
| Rietspoof Malware | 1 | 0 | yes | link |
| #LockerGoga Ransomware (signed) | 1 | 0 | yes | link |
Hard_Configurator by @Andy Ful
Attachments
Last edited: