I noticed that many users are interested in securing Windows Home from PowerShell attacks. There are a few ways to do it, using GPO, reg tweaks or SRP.
A. Disabling PowerShell script execution by reg tweak (Windows 7+):
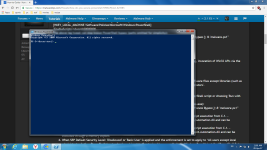
[HKEY_LOCAL_MACHINE \Software\Policies\Microsoft\Windows\PowerShell]
"EnableScripts"=dword:00000000
The above reg tweak can stop known PowerShell bypass (paths omitted for simplicity):
powershell.exe "-Command" "if((Get-ExecutionPolicy ) -ne 'AllSigned') { Set-ExecutionPolicy -Scope Process Bypass }; & 'malware.ps1'"
etc.
The user can still run scripts from PowerShell console, for example (paths omitted for simplicity):
Get-Content helloworld.ps1 | PowerShell.exe -noprofile -
B. Restricting PowerShell by reg tweak to Constrained Language mode (PowerShell v.3.0 or later).
Constrained language mode locks down PowerShell to the core elements (no access to: direct .NET scripting, invocation of Win32 APIs via the Add-Type cmdlet, and interaction with COM objects).
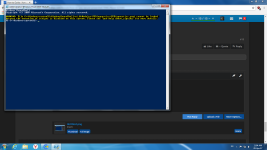
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Environment]
"__PSLockDownPolicy"="4"
C. Using Default Deny Software Restriction Policies with Enforcement setting 'All software files' or 'All software files except libraries (such as Dlls)'. Scripts can be run with Administrative Rights when SRP are applied to 'All users except local administrators'.
Post edited to add System.Management.Automation.ni.dll .
There is a way to bypass __PSLockDownPolicy, but this can be prevented when using it with Disabling PowerShell script execution reg tweak.
A. Disabling PowerShell script execution by reg tweak (Windows 7+):
[HKEY_LOCAL_MACHINE \Software\Policies\Microsoft\Windows\PowerShell]
"EnableScripts"=dword:00000000
The above reg tweak can stop known PowerShell bypass (paths omitted for simplicity):
powershell.exe "-Command" "if((Get-ExecutionPolicy ) -ne 'AllSigned') { Set-ExecutionPolicy -Scope Process Bypass }; & 'malware.ps1'"
etc.
The user can still run scripts from PowerShell console, for example (paths omitted for simplicity):
Get-Content helloworld.ps1 | PowerShell.exe -noprofile -
B. Restricting PowerShell by reg tweak to Constrained Language mode (PowerShell v.3.0 or later).
Constrained language mode locks down PowerShell to the core elements (no access to: direct .NET scripting, invocation of Win32 APIs via the Add-Type cmdlet, and interaction with COM objects).
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Environment]
"__PSLockDownPolicy"="4"
C. Using Default Deny Software Restriction Policies with Enforcement setting 'All software files' or 'All software files except libraries (such as Dlls)'. Scripts can be run with Administrative Rights when SRP are applied to 'All users except local administrators'.
- Adding PowerShell extensions to 'Designated File Types' list.
This can disable script execution when using Windows Explorer or Internet Explorer, by clicking PowerShell script or choosing 'Run with PowerShell' from the right click context menu.
The script can still be executed when using commands with sponsors (PowerShell.exe, PowerShell_ise.exe):
powershell.exe "-Command" "if((Get-ExecutionPolicy ) -ne 'AllSigned') { Set-ExecutionPolicy -Scope Process Bypass }; & 'malware.ps1'"
etc. - Adding Disallowed rule '*.PS1' (or similar rules for other extensions). This can stop all examples of script execution from C.1. - PowerShell console is accessible as standard user. PowerShell still exists in the System.Management.Automation.dll (System.Management.Automation.ni.dll) and can be executed through a memory exploit to run scripts with nonstandard extensions.
- Applying Disallowed rules to powershell.exe and powershell_ise.exe . This can stop all examples of script execution from C.1. - PowerShell console is not accessible as standard user. PowerShell still exists in the System.Management.Automation.dll (System.Management.Automation.ni.dll) and can be executed through a memory exploit.
- When SRP Default Security Level: 'Disallowed' or 'Basic User' is applied and the enforcement is set to apply to ‘All users except local administrators’, then PowerShell (as standard user) is set to Constrained Language Mode (in Windows 7+ with installed PowerShell 5+). This can stop many malware scripts and exploit tools. In Windows 7, one should have .NET Framework 4.5.2 installed, and then install WMF 5.1: Install and configure WMF 5.1 . Whitelisted locations in SRP, do not change Constrained Language Mode setting. When PowerShell is run as administrator the Language mode is set to FullLanguage.
Post edited to add System.Management.Automation.ni.dll .
There is a way to bypass __PSLockDownPolicy, but this can be prevented when using it with Disabling PowerShell script execution reg tweak.
Last edited: