How to find cryptojacking malware
badpackets.net: How to find cryptojacking malware
MOTTO:
Source Code Search Engine: PublicWWW. This is a search engine that indexes the entire source code of websites.
by Troy
How to find cryptojacking malware
Cryptojacking malware continues to spread across the web, largely due to the popularity of Coinhive. Since Coinhive’s launch in September 2017, numerous cryptojacking clones have come about.
The tool I’ve chosen to locate them with is PublicWWW. This is a search engine that indexes the entire source code of websites. I previously offered a comparison of their dataset versus other providers in my discussion of Coinhive malware specifically.
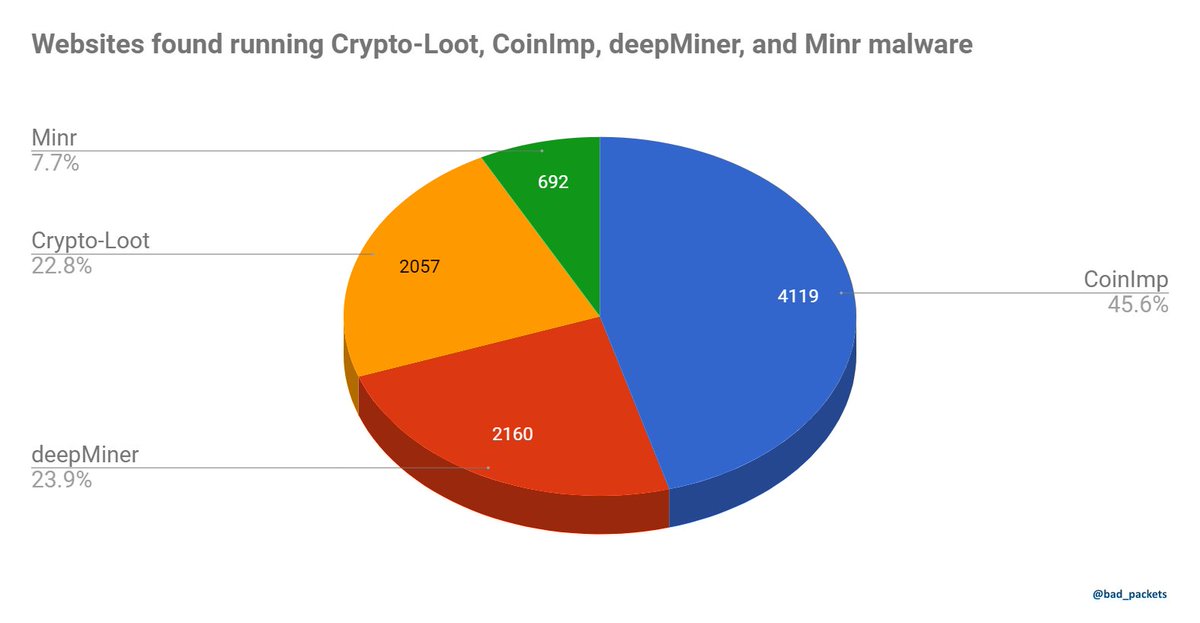
In this post, I detail how to find websites containing Coinhive, Crypto-Loot, CoinImp, and deepMiner in PublicWWW.
Let’s jump in and see how many sites with cryptojacking malware we can find!
Coinhive
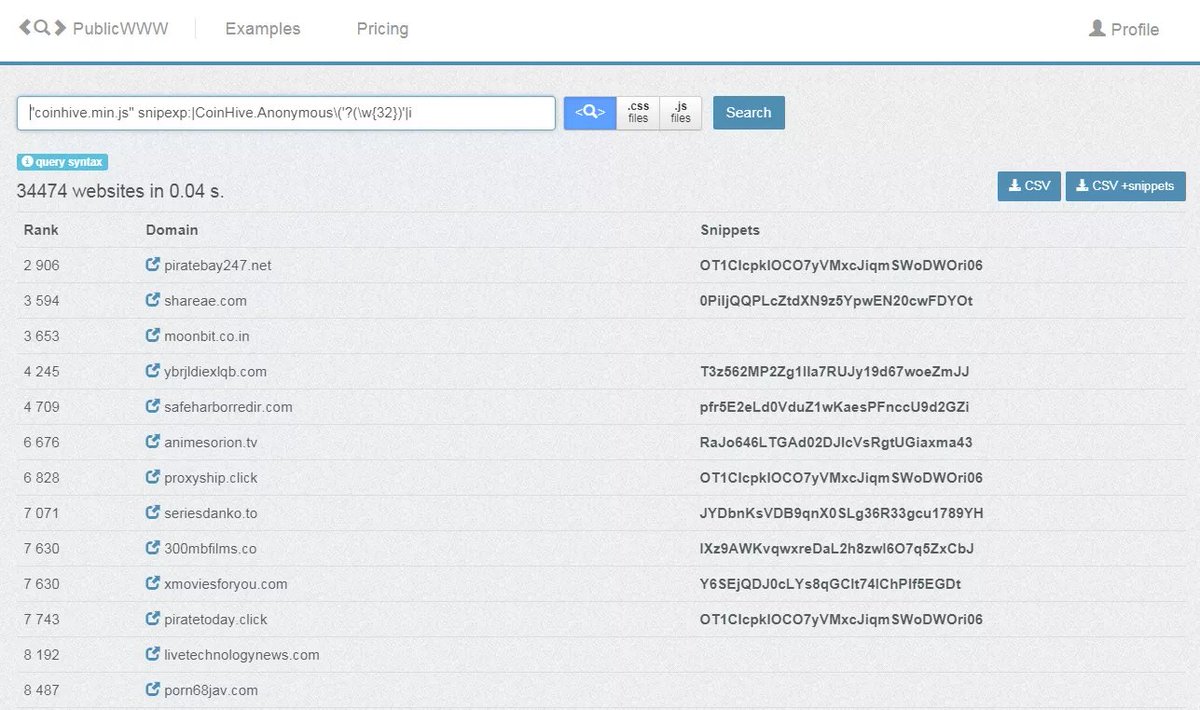
Before we review some of the knock-offs, let’s look at the most synonymous name with cryptojacking, Coinhive. Finding this malware is relatively easy and various queries can be used to locate it. The original Coinhive JavaScript library used in cryptojacking is “coinhive.min.js” and we can start by simply searching for that. It’s important to search for the entire name in quotes to ensure an exact match is returned by PublicWWW.

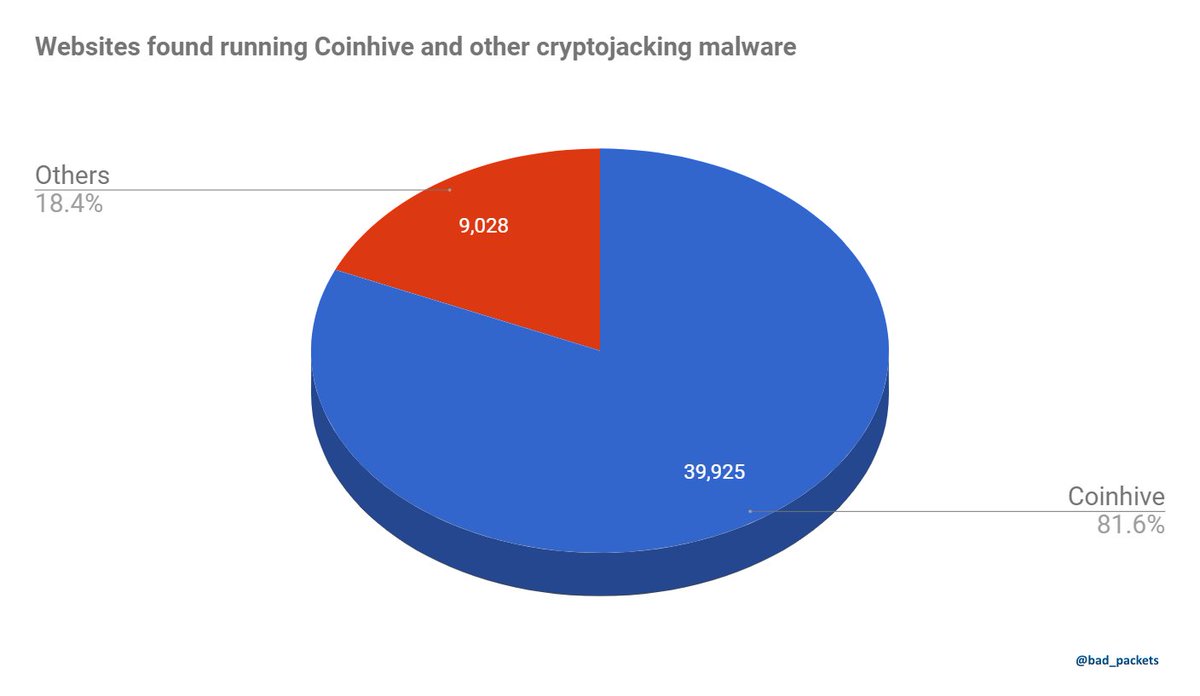
Using this query, we find 34,474 sites. While this may seem like an astounding number, it’s only a modest increase since I wrote about the 30,000 sites found back in November 2017.
While this list of sites is great for an overview of sites with Coinhive malware, we can dig even deeper into PublicWWW’s dataset to extract the Coinhive site key used on each site. This can be done using regex to extract the site key as a snippet: “coinhive.min.js” snipexp:|CoinHive.Anonymous\(‘?(\w{32})’|i

Once the Coinhive site key is extracted, we can export the results and correlate which sites are part of a cryptojacking campaign. This correlation of a small number of Coinhive site keys to hundreds and even thousands of websites was documented in my previous post.
Recently I found a large cryptojacking campaign targeting 5,451 WordPress sites. In each case, the JavaScript containing Coinhive was hidden via obfuscation. While PublicWWW can’t search within the deobfuscated JavaScript itself, we can find a way to work around it.

To search for the affected sites, the following query, graciously crafted for me by VriesHd, was used:
“[\”(k” “\\x43\\x72\\x79\\x70\\x74\\x6f\\x6e\\x69\\x67\\x68\\x74\\x57\\x41\\x53\\x4d\\x57\\x72\\x61\\x70\\x70\\x65\\x72” snipexp:|(var _0x[0-z]{4}=)|
This query searches for the JavaScript function name used for the obfuscated code and then regex to extract a snippet of that name. This is useful to correlate the function name, such as “var _0xb70e” to the Coinhive site key used. Six unique keys were found to be used in this cryptojacking campaign:
Coinhive site key (function name)
DhGEVUgOoquJP68XByYLFs0nRVV4gq4J (0xb70e)
bbgnHTSmMLKUMaQzNa3Yfoul34A3cACd (0xbcba,0xe2f6)
hg9mNsA2DPkqe1F9yCUyWXggnDyrPqVW (0x1b00)
T6Oy0x11TMdeZRjy684Xow4GNBpb07SK (0xf80b)
OQoqVYH65ER2Eg2xcmoVtv4qrcHP2Z7G (0xe4d0,0xb765,0xcc28)
VW8fWIsg9hjn47qBdmb0jImf7pDHmU28 (0x8f35)
In some cases the same Coinhive site key was associated to multiple functions, shown above.
Crypto-Loot
Crypto-Loot has steadily remained as one the most popular alternatives to Coinhive since its inception. Similar to Coinhive, Crypto-Loot doesn’t require any user interaction and can run steathlity in the background....
...read MORE at the website...
_____________________________________________
Mmm so it's not possible to stop cryptojacking malwares with coin miner blockers extensions
so at your searches with Source Code Search Engine...
Usage Examples: Advertising Examples - PublicWWW.com
badpackets.net: How to find cryptojacking malware
MOTTO:
Source Code Search Engine: PublicWWW. This is a search engine that indexes the entire source code of websites.
by Troy
How to find cryptojacking malware
Cryptojacking malware continues to spread across the web, largely due to the popularity of Coinhive. Since Coinhive’s launch in September 2017, numerous cryptojacking clones have come about.
The tool I’ve chosen to locate them with is PublicWWW. This is a search engine that indexes the entire source code of websites. I previously offered a comparison of their dataset versus other providers in my discussion of Coinhive malware specifically.
In this post, I detail how to find websites containing Coinhive, Crypto-Loot, CoinImp, and deepMiner in PublicWWW.
Let’s jump in and see how many sites with cryptojacking malware we can find!
Coinhive
Before we review some of the knock-offs, let’s look at the most synonymous name with cryptojacking, Coinhive. Finding this malware is relatively easy and various queries can be used to locate it. The original Coinhive JavaScript library used in cryptojacking is “coinhive.min.js” and we can start by simply searching for that. It’s important to search for the entire name in quotes to ensure an exact match is returned by PublicWWW.

Using this query, we find 34,474 sites. While this may seem like an astounding number, it’s only a modest increase since I wrote about the 30,000 sites found back in November 2017.
While this list of sites is great for an overview of sites with Coinhive malware, we can dig even deeper into PublicWWW’s dataset to extract the Coinhive site key used on each site. This can be done using regex to extract the site key as a snippet: “coinhive.min.js” snipexp:|CoinHive.Anonymous\(‘?(\w{32})’|i

Once the Coinhive site key is extracted, we can export the results and correlate which sites are part of a cryptojacking campaign. This correlation of a small number of Coinhive site keys to hundreds and even thousands of websites was documented in my previous post.
Recently I found a large cryptojacking campaign targeting 5,451 WordPress sites. In each case, the JavaScript containing Coinhive was hidden via obfuscation. While PublicWWW can’t search within the deobfuscated JavaScript itself, we can find a way to work around it.

To search for the affected sites, the following query, graciously crafted for me by VriesHd, was used:
“[\”(k” “\\x43\\x72\\x79\\x70\\x74\\x6f\\x6e\\x69\\x67\\x68\\x74\\x57\\x41\\x53\\x4d\\x57\\x72\\x61\\x70\\x70\\x65\\x72” snipexp:|(var _0x[0-z]{4}=)|
This query searches for the JavaScript function name used for the obfuscated code and then regex to extract a snippet of that name. This is useful to correlate the function name, such as “var _0xb70e” to the Coinhive site key used. Six unique keys were found to be used in this cryptojacking campaign:
Coinhive site key (function name)
DhGEVUgOoquJP68XByYLFs0nRVV4gq4J (0xb70e)
bbgnHTSmMLKUMaQzNa3Yfoul34A3cACd (0xbcba,0xe2f6)
hg9mNsA2DPkqe1F9yCUyWXggnDyrPqVW (0x1b00)
T6Oy0x11TMdeZRjy684Xow4GNBpb07SK (0xf80b)
OQoqVYH65ER2Eg2xcmoVtv4qrcHP2Z7G (0xe4d0,0xb765,0xcc28)
VW8fWIsg9hjn47qBdmb0jImf7pDHmU28 (0x8f35)
In some cases the same Coinhive site key was associated to multiple functions, shown above.
Crypto-Loot
Crypto-Loot has steadily remained as one the most popular alternatives to Coinhive since its inception. Similar to Coinhive, Crypto-Loot doesn’t require any user interaction and can run steathlity in the background....
...read MORE at the website...
_____________________________________________
Mmm so it's not possible to stop cryptojacking malwares with coin miner blockers extensions
so at your searches with Source Code Search Engine...
Usage Examples: Advertising Examples - PublicWWW.com
Last edited:






 Bad Packets Report @bad_packets
Bad Packets Report @bad_packets